[Resolved] WinFixer woes
#1
![[Resolved] WinFixer woes: post #1](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 08 October 2009 - 08:19 PM
Register to Remove
#2
![[Resolved] WinFixer woes: post #2](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 08 October 2009 - 08:22 PM
#3
![[Resolved] WinFixer woes: post #3](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 09 October 2009 - 04:13 AM
#4
![[Resolved] WinFixer woes: post #4](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 10 October 2009 - 04:13 AM
#5
![[Resolved] WinFixer woes: post #5](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 11 October 2009 - 08:26 AM
Please do the following:
Please download exeHelper to your desktop.
- Double-click on exeHelper.com to run the fix.
- A black window should pop up, press any key to close once the fix is completed.
- Post the contents of log.txt (Will be created in the directory where you ran exeHelper.com)
NEXT
Please download DDS from either of these links
LINK 1
LINK 2
and save it to your desktop.
- Disable any script blocking protection
- Double click dds.pif to run the tool.
- When done, two DDS.txt's will open.
- Save both reports to your desktop.
Please include the contents of the following in your next reply:
DDS.txt
Attach.txt.
NEXT

Download GMER Rootkit Scanner from here or here.
- Extract the contents of the zipped file to desktop.
- Double click GMER.exe. If asked to allow gmer.sys driver to load, please consent .
- If it gives you a warning about rootkit activity and asks if you want to run scan...click on NO.

Click the image to enlarge it
- In the right panel, you will see several boxes that have been checked. Uncheck the following ...
- Sections
- IAT/EAT
- Drives/Partition other than Systemdrive (typically C:\)
- Show All (don't miss this one)
- Then click the Scan button & wait for it to finish.
- Once done click on the [Save..] button, and in the File name area, type in "Gmer.txt" or it will save as a .log file which cannot be uploaded to your post.
- Save it where you can easily find it, such as your desktop, and post it in your next reply.
**Caution**
Rootkit scans often produce false positives. Do NOT take any action on any "<--- ROOKIT" entries
Microsoft MVP 2010, 2011, 2012, 2013, 2014, 2015
#6
![[Resolved] WinFixer woes: post #6](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 11 October 2009 - 08:37 PM
Edited by someguy, 11 October 2009 - 09:04 PM.
#7
![[Resolved] WinFixer woes: post #7](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 11 October 2009 - 11:03 PM
there is a possibility of transference.
use this on the usb
Download Flash_Disinfector.exe from HERE and save it to your desktop.
- Double-click Flash_Disinfector.exe to run it and follow any prompts that may appear.
- The utility may ask you to insert your flash drive and/or other removable drives including your mobile phone. Please do so and allow the utility to clean up those drives as well.
- Wait until it has finished scanning and then exit the program.
- Reboot your computer when done.
The following tool will run from a USB, download on another computer and transfer to the infected PC and run it:
Download ComboFix from one of the following locations:
Link 1
Link 2
VERY IMPORTANT !!! Save ComboFix.exe to your Desktop
* IMPORTANT - Disable your AntiVirus and AntiSpyware applications, usually via a right click on the System Tray icon. They may otherwise interfere with our tools. If you have difficulty properly disabling your protective programs, refer to this link here
- Double click on ComboFix.exe & follow the prompts.
- Follow the prompts to allow ComboFix to download and install the Microsoft Windows Recovery Console, and when prompted, agree to the End-User License Agreement to install the Microsoft Windows Recovery Console.

- Once the Microsoft Windows Recovery Console is installed using ComboFix, you should see the following message:

- Click on Yes, to continue scanning for malware.
Notes:
1. Do not mouse-click Combofix's window while it is running. That may cause it to stall.
2. Do not "re-run" Combofix. If you have a problem, reply back for further instructions.
Please make sure you include the combo fix log in your next reply as well as describe how your computer is running now
Microsoft MVP 2010, 2011, 2012, 2013, 2014, 2015
#8
![[Resolved] WinFixer woes: post #8](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 12 October 2009 - 12:56 AM
Edited by someguy, 12 October 2009 - 01:06 AM.
#9
![[Resolved] WinFixer woes: post #9](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 12 October 2009 - 01:08 AM
#10
![[Resolved] WinFixer woes: post #10](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 12 October 2009 - 04:31 AM
Here is the combofix log:
ComboFix 09-10-11.01 - John 10/12/2009 4:10.1.2 - NTFSx86
Microsoft Windows XP Home Edition 5.1.2600.3.1252.1.1033.18.2046.1555 [GMT -5:00]
Running from: c:\documents and settings\John\Desktop\ComboFix.exe
.
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
c:\docume~1\John\LOCALS~1\Temp\lsass.exe
c:\docume~1\John\LOCALS~1\Temp\services.exe
c:\docume~1\John\LOCALS~1\Temp\svchost.exe
c:\docume~1\John\LOCALS~1\Temp\winlogon.exe
c:\documents and settings\John\ntuser.dll
c:\documents and settings\John\Start Menu\Programs\Startup\scandisk.dll
c:\documents and settings\John\Start Menu\Programs\Startup\scandisk.lnk
c:\documents and settings\LocalService\ntuser.dll
c:\program files\INSTALL.LOG
c:\program files\Windows Police Pro
c:\program files\Windows Police Pro\msvcm80.dll
c:\program files\Windows Police Pro\msvcp80.dll
c:\program files\Windows Police Pro\msvcr80.dll
c:\program files\Windows Police Pro\winivsetup.exe
c:\windows\msa.exe
c:\windows\struct~.ini
c:\windows\system32\6to4v32.dll
c:\windows\system32\bamonipo.exe
c:\windows\system32\calc.dll
c:\windows\system32\config\systemprofile\ntuser.dll
c:\windows\system32\drivers\gasfkyvdadtelr.sys
c:\windows\system32\filokinu.dll
c:\windows\system32\FInstall.sys
c:\windows\system32\gasfkydbmfjnpd.dat
c:\windows\system32\gasfkyepmbivkp.dll
c:\windows\system32\gasfkypyfdevel.dll
c:\windows\system32\gasfkyyavhlype.dat
c:\windows\system32\giyesewu.exe
c:\windows\system32\Install.txt
c:\windows\system32\isasdk.sys
c:\windows\system32\losamine.dll
c:\windows\system32\lowsec
c:\windows\system32\lowsec\local.ds
c:\windows\system32\lowsec\user.ds
c:\windows\system32\lowsec\user.ds.lll
c:\windows\system32\lujorosu.dll
c:\windows\system32\msXMl71.dll
c:\windows\system32\pebapehe.exe
c:\windows\system32\plUGie.dll
c:\windows\system32\pump.exe
c:\windows\system32\sdra64.exe
c:\windows\system32\vafubamu.dll
c:\windows\system32\x9212.dll
c:\windows\TEMP\mta65584.dll
.
((((((((((((((((((((((((((((((((((((((( Drivers/Services )))))))))))))))))))))))))))))))))))))))))))))))))
.
-------\Legacy_6TO4
-------\Legacy_gasfkysxhgufyc
-------\Legacy_ISASDK
-------\Service_6to4
-------\Service_gasfkysxhgufyc
-------\Service_isasdk
((((((((((((((((((((((((( Files Created from 2009-09-12 to 2009-10-12 )))))))))))))))))))))))))))))))
.
2009-10-12 07:15 . 2009-10-12 07:15 -------- d--h--w- c:\windows\PIF
2009-10-12 06:37 . 2009-10-12 06:37 -------- d-----w- c:\documents and settings\John\Application Data\Malwarebytes
2009-10-12 06:37 . 2009-09-10 19:54 38224 ----a-w- c:\windows\system32\drivers\mbamswissarmy.sys
2009-10-12 06:37 . 2009-10-12 06:37 -------- d-----w- c:\program files\Malwarebytes' Anti-Malware
2009-10-12 06:37 . 2009-10-12 06:37 -------- d-----w- c:\documents and settings\All Users\Application Data\Malwarebytes
2009-10-12 06:37 . 2009-09-10 19:53 19160 ----a-w- c:\windows\system32\drivers\mbam.sys
2009-10-09 10:06 . 2009-10-12 07:57 -------- d-----w- c:\documents and settings\All Users\Application Data\65104824
2009-10-09 10:06 . 2009-10-12 07:49 -------- d-----w- c:\documents and settings\All Users\Application Data\88742938
2009-10-09 00:56 . 2009-10-12 06:11 58 ----a-w- c:\windows\wf4.dat
2009-10-09 00:56 . 2009-10-12 06:11 2 ----a-w- c:\windows\wf3.dat
2009-10-09 00:56 . 2009-10-09 00:56 36 ----a-w- c:\windows\system32\skynet.dat
2009-10-09 00:55 . 2009-10-09 00:55 9216 ----a-w- C:\fdgoti.exe
2009-10-09 00:55 . 2009-10-09 00:55 208384 ----a-w- C:\scxmgj.exe
2009-10-09 00:55 . 2009-10-09 00:55 90624 ----a-w- C:\gfsufon.exe
2009-10-09 00:55 . 2009-10-09 00:55 48640 ----a-w- C:\jyvtfwu.exe
2009-10-09 00:55 . 2009-10-09 00:55 52224 ----a-w- C:\srvgdoqj.exe
2009-10-09 00:49 . 2009-10-09 00:49 -------- d-----w- c:\documents and settings\John\Application Data\Pamela
2009-10-09 00:49 . 2009-10-09 00:49 175104 ----a-w- c:\windows\system32\RemoteControl.dll
2009-10-09 00:49 . 2009-10-09 00:53 -------- d-----w- c:\program files\Pamela
2009-10-09 00:36 . 2009-10-09 00:37 -------- d-----w- c:\documents and settings\All Users\Application Data\PrettyMay
2009-10-09 00:36 . 2009-10-09 00:36 -------- d-----w- c:\documents and settings\John\Application Data\PrettyMay
2009-09-24 16:01 . 2009-09-24 16:01 -------- d-----w- C:\PROGRAM1
2009-09-24 00:56 . 2009-09-24 00:56 -------- d-----w- c:\program files\Kap.GRETests
2009-09-24 00:56 . 1999-02-25 11:32 122880 ----a-w- c:\windows\system32\fxtls532.dll
2009-09-24 00:56 . 1999-01-29 05:28 29184 ----a-w- c:\windows\system32\picn20.dll
2009-09-24 00:56 . 1999-03-26 00:00 101888 ----a-w- c:\windows\system32\VB6STKIT.DLL
2009-09-21 16:42 . 2009-06-21 21:44 153088 -c----w- c:\windows\system32\dllcache\triedit.dll
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2009-10-12 09:04 . 2009-07-17 15:16 -------- d-----w- c:\program files\TextAloud
2009-10-11 04:14 . 2009-10-11 04:14 93184 ----a-w- c:\windows\system32\win4.tmp
2009-10-11 04:14 . 2009-07-11 04:14 1011452 --sha-w- c:\windows\system32\kanelewu.exe
2009-10-11 04:14 . 2009-07-11 04:14 91136 --sha-w- c:\windows\system32\sobamehu.dll
2009-10-10 10:35 . 2009-10-10 10:35 93184 ----a-w- c:\windows\system32\win6.tmp
2009-10-10 08:38 . 2009-07-10 08:38 52736 --sha-w- c:\windows\system32\salizuya.dll
2009-10-10 08:38 . 2009-07-10 08:38 1011343 --sha-w- c:\windows\system32\nifisofo.exe
2009-10-10 08:38 . 2009-07-10 08:38 39424 --sha-w- c:\windows\system32\gokisoso.dll
2009-10-09 10:05 . 2009-07-09 10:05 39424 --sha-w- c:\windows\system32\bovenage.dll
2009-10-09 10:05 . 2009-07-09 10:05 28160 --sha-w- c:\windows\system32\yomoviya.dll
2009-10-09 10:05 . 2009-04-16 14:25 -------- d-----w- c:\documents and settings\All Users\Application Data\Google Updater
2009-10-09 00:58 . 2009-10-09 00:58 93184 ----a-w- c:\windows\system32\win1F9D.tmp
2009-10-09 00:50 . 2009-05-06 17:12 -------- d-----w- c:\documents and settings\John\Application Data\Skype
2009-10-08 23:49 . 2009-05-06 17:14 -------- d-----w- c:\documents and settings\John\Application Data\skypePM
2009-10-08 08:57 . 2009-06-04 21:15 25 ----a-w- c:\windows\popcinfot.dat
2009-10-07 21:39 . 2009-02-14 01:09 -------- d-----w- c:\program files\IrfanView
2009-10-03 13:43 . 2009-02-21 23:02 -------- d-----w- c:\program files\BitComet
2009-10-03 02:14 . 2009-08-09 17:48 -------- d-----w- c:\program files\BFG
2009-10-03 02:02 . 2009-08-09 22:06 -------- d-----w- c:\program files\Codemasters
2009-10-03 02:02 . 2009-02-14 20:12 -------- d--h--w- c:\program files\InstallShield Installation Information
2009-09-30 06:32 . 2009-02-16 09:15 107888 ----a-w- c:\windows\system32\CmdLineExt.dll
2009-09-22 14:44 . 2009-02-16 02:48 60096 ----a-w- c:\windows\system32\nvModes.dat
2009-08-24 16:13 . 2009-03-11 21:19 -------- d-----w- c:\program files\PowerISO
2009-08-11 07:42 . 2009-02-18 03:36 100800 ----a-w- c:\documents and settings\John\Local Settings\Application Data\GDIPFONTCACHEV1.DAT
2009-08-10 05:42 . 2009-08-10 05:42 43520 ----a-w- c:\windows\system32\CmdLineExt03.dll
2009-08-09 18:24 . 2009-08-09 18:24 0 ----a-w- c:\windows\popcinfo.dat
2009-08-07 00:24 . 2009-02-13 02:02 327896 ----a-w- c:\windows\system32\wucltui.dll
2009-08-07 00:24 . 2009-02-13 02:02 209632 ----a-w- c:\windows\system32\wuweb.dll
2009-08-07 00:24 . 2009-02-13 02:02 35552 ----a-w- c:\windows\system32\wups.dll
2009-08-07 00:24 . 2008-10-16 20:09 44768 ----a-w- c:\windows\system32\wups2.dll
2009-08-07 00:24 . 2009-02-13 02:02 53472 ----a-w- c:\windows\system32\wuauclt.exe
2009-08-07 00:24 . 2004-08-12 13:56 96480 ----a-w- c:\windows\system32\cdm.dll
2009-08-07 00:23 . 2009-02-13 02:02 575704 ----a-w- c:\windows\system32\wuapi.dll
2009-08-07 00:23 . 2009-02-13 02:02 1929952 ----a-w- c:\windows\system32\wuaueng.dll
2009-08-05 09:01 . 2004-08-12 14:01 204800 ----a-w- c:\windows\system32\mswebdvd.dll
2009-07-29 03:42 . 2009-07-29 03:42 796672 ----a-w- c:\windows\GPInstall.exe
2009-07-27 02:43 . 2009-07-27 02:43 58908 ----a-w- c:\windows\system32\drivers\scdemu.sys
2009-07-17 19:01 . 2004-08-12 13:55 58880 ----a-w- c:\windows\system32\atl.dll
2003-12-18 16:33 . 2009-08-10 05:39 20102 ----a-w- c:\program files\Readme.txt
2003-09-03 12:46 . 2009-08-10 05:39 10960 ----a-w- c:\program files\EULA.txt
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"DAEMON Tools Lite"="c:\program files\DAEMON Tools Lite\daemon.exe" [2009-04-23 691656]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"NvCplDaemon"="c:\windows\system32\NvCpl.dll" [2009-01-30 13594624]
"NvMediaCenter"="c:\windows\system32\NvMcTray.dll" [2009-01-30 86016]
"Dell QuickSet"="c:\program files\Dell\QuickSet\Quickset.exe" [2007-05-14 1191936]
"SigmatelSysTrayApp"="c:\program files\SigmaTel\C-Major Audio\WDM\stsystra.exe" [2007-05-10 405504]
"nwiz"="nwiz.exe" - c:\windows\system32\nwiz.exe [2009-01-30 1657376]
"NVHotkey"="nvHotkey.dll" - c:\windows\system32\nvhotkey.dll [2009-01-30 90112]
[HKEY_LOCAL_MACHINE\software\microsoft\windows nt\currentversion\winlogon\notify\GoToAssist]
2009-08-11 07:19 10536 ----a-w- c:\program files\Citrix\GoToAssist\514\g2awinlogon.dll
[HKEY_LOCAL_MACHINE\system\currentcontrolset\control\lsa]
Notification Packages REG_MULTI_SZ scecli moneap.dll
[HKLM\~\startupfolder\C:^Documents and Settings^John^Start Menu^Programs^Startup^Adobe Gamma.lnk]
path=c:\documents and settings\John\Start Menu\Programs\Startup\Adobe Gamma.lnk
backup=c:\windows\pss\Adobe Gamma.lnkStartup
[HKLM\~\startupfolder\C:^Documents and Settings^John^Start Menu^Programs^Startup^OneNote 2007 Screen Clipper and Launcher.lnk]
path=c:\documents and settings\John\Start Menu\Programs\Startup\OneNote 2007 Screen Clipper and Launcher.lnk
backup=c:\windows\pss\OneNote 2007 Screen Clipper and Launcher.lnkStartup
[HKEY_LOCAL_MACHINE\software\microsoft\security center]
"UpdatesDisableNotify"=dword:00000001
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile]
"EnableFirewall"= 0 (0x0)
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"%windir%\\system32\\sessmgr.exe"=
"%windir%\\Network Diagnostic\\xpnetdiag.exe"=
"c:\\Program Files\\Valve\\Steam\\SteamApps\\sulljoh1\\source sdk base 2007\\hl2.exe"=
"c:\\Program Files\\Opera\\opera.exe"=
"c:\\Program Files\\Valve\\Steam\\SteamApps\\sulljoh1\\source sdk base\\hl2.exe"=
"c:\\Program Files\\BitComet\\BitComet.exe"=
"c:\\Program Files\\Bonjour\\mDNSResponder.exe"=
"c:\\Program Files\\iTunes\\iTunes.exe"=
"c:\\Program Files\\LucasArts\\Star Wars Empire at War\\GameData\\sweaw.exe"=
"c:\\Documents and Settings\\John\\Local Settings\\Application Data\\Google\\Google Talk Plugin\\googletalkplugin.dll"=
"c:\\Documents and Settings\\John\\Local Settings\\Application Data\\Google\\Google Talk Plugin\\googletalkplugin.exe"=
"c:\\Program Files\\Google\\Google Talk\\googletalk.exe"=
"c:\\Program Files\\ICQ6.5\\ICQ.exe"=
"c:\\Program Files\\Autodesk\\3ds Max 9\\3dsmax.exe"=
"c:\\Program Files\\Autodesk\\Backburner\\monitor.exe"=
"c:\\Program Files\\Autodesk\\Backburner\\manager.exe"=
"c:\\Program Files\\Autodesk\\Backburner\\server.exe"=
"c:\\Program Files\\Microsoft Office\\Office12\\OUTLOOK.EXE"=
"c:\\Program Files\\Microsoft Office\\Office12\\GROOVE.EXE"=
"c:\\Program Files\\Microsoft Office\\Office12\\ONENOTE.EXE"=
"c:\\Program Files\\Codemasters\\Overlord\\Overlord.exe"=
"c:\\Program Files\\Codemasters\\Overlord II\\Overlord2.exe"=
"c:\\Program Files\\Skype\\Phone\\Skype.exe"=
"c:\\WINDOWS\\system32\\HPZipm12.exe"=
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\GloballyOpenPorts\List]
"15043:TCP"= 15043:TCP:BitComet 15043 TCP
"15043:UDP"= 15043:UDP:BitComet 15043 UDP
R2 BtwSrv;BtwSrv;c:\windows\system32\svchost.exe -k netsvcs [8/12/2004 9:06 AM 14336]
R2 fastnetsrv;fastnetsrv Service;c:\windows\system32\FastNetSrv.exe [8/12/2004 8:56 AM 94720]
R2 ICQ Service;ICQ Service;c:\program files\ICQ6Toolbar\ICQ Service.exe [4/14/2009 4:19 PM 222456]
S2 AntiPol;AntiPol;c:\windows\svchast.exe --> c:\windows\svchast.exe [?]
S2 gupdate1c9be9f4c4ca05c;Google Update Service (gupdate1c9be9f4c4ca05c);c:\program files\Google\Update\GoogleUpdate.exe [4/16/2009 9:26 AM 133104]
--- Other Services/Drivers In Memory ---
*NewlyCreated* - BTWSRV
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost - NetSvcs
BtwSrv
.
Contents of the 'Scheduled Tasks' folder
2009-10-12 c:\windows\Tasks\Google Software Updater.job
- c:\program files\Google\Common\Google Updater\GoogleUpdaterService.exe [2009-04-16 14:25]
2009-10-12 c:\windows\Tasks\GoogleUpdateTaskMachineCore.job
- c:\program files\Google\Update\GoogleUpdate.exe [2009-04-16 14:26]
2009-10-10 c:\windows\Tasks\GoogleUpdateTaskMachineUA.job
- c:\program files\Google\Update\GoogleUpdate.exe [2009-04-16 14:26]
2009-10-08 c:\windows\Tasks\GoogleUpdateTaskUserS-1-5-21-1177238915-1844823847-725345543-1004Core.job
- c:\documents and settings\John\Local Settings\Application Data\Google\Update\GoogleUpdate.exe [2009-04-06 00:12]
2009-10-09 c:\windows\Tasks\GoogleUpdateTaskUserS-1-5-21-1177238915-1844823847-725345543-1004UA.job
- c:\documents and settings\John\Local Settings\Application Data\Google\Update\GoogleUpdate.exe [2009-04-06 00:12]
.
.
------- Supplementary Scan -------
.
uStart Page = hxxp://start.icq.com/
uInternet Settings,ProxyOverride = *.local
IE: &D&ownload &with BitComet - c:\program files\BitComet\BitComet.exe/AddLink.htm
IE: &D&ownload all video with BitComet - c:\program files\BitComet\BitComet.exe/AddVideo.htm
IE: &D&ownload all with BitComet - c:\program files\BitComet\BitComet.exe/AddAllLink.htm
IE: E&xport to Microsoft Excel - c:\progra~1\MICROS~2\Office12\EXCEL.EXE/3000
FF - ProfilePath - c:\documents and settings\John\Application Data\Mozilla\Firefox\Profiles\j1cizrmh.default\
FF - prefs.js: browser.startup.homepage - hxxp://www.google.com
FF - component: c:\program files\Mozilla Firefox\extensions\{B13721C7-F507-4982-B2E5-502A71474FED}\components\NPComponent.dll
FF - plugin: c:\documents and settings\John\Application Data\Mozilla\plugins\npgoogletalk.dll
FF - plugin: c:\documents and settings\John\Local Settings\Application Data\Google\Update\1.2.183.7\npGoogleOneClick8.dll
FF - plugin: c:\program files\Google\Google Updater\2.4.1536.6592\npCIDetect13.dll
FF - plugin: c:\program files\Google\Update\1.2.183.7\npGoogleOneClick8.dll
FF - plugin: c:\program files\Opera\program\plugins\nppl3260.dll
FF - plugin: c:\program files\Opera\program\plugins\nprpjplug.dll
FF - HiddenExtension: Microsoft .NET Framework Assistant: {20a82645-c095-46ed-80e3-08825760534b} - c:\windows\Microsoft.NET\Framework\v3.5\Windows Presentation Foundation\DotNetAssistantExtension\
.
- - - - ORPHANS REMOVED - - - -
HKLM-Run-pazubosiye - losamine.dll
AddRemove-DAEMON Tools Toolbar - c:\program files\DAEMON Tools Toolbar\uninst.exe
AddRemove-divxh264_is1 - c:\program files\DivX H.264
**************************************************************************
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2009-10-12 04:15
Windows 5.1.2600 Service Pack 3 NTFS
scanning hidden processes ...
scanning hidden autostart entries ...
scanning hidden files ...
c:\windows\system32\Install.txt 265 bytes
scan completed successfully
hidden files: 1
**************************************************************************
.
--------------------- LOCKED REGISTRY KEYS ---------------------
[HKEY_USERS\S-1-5-21-1177238915-1844823847-725345543-1004\Software\SecuROM\License information*]
"datasecu"=hex:98,83,92,bc,bd,a4,1b,90,d7,8b,71,08,35,d6,44,ac,c0,9a,4f,d7,88,
10,33,be,78,3a,0f,54,ee,6a,27,80,1f,f4,52,24,2c,b4,69,fa,6b,fb,ce,c2,af,e2,\
"rkeysecu"=hex:5c,6a,b3,2c,b9,5a,0d,e2,88,50,3c,5d,3e,01,f6,0e
.
--------------------- DLLs Loaded Under Running Processes ---------------------
- - - - - - - > 'winlogon.exe'(964)
c:\program files\Citrix\GoToAssist\514\G2AWinLogon.dll
- - - - - - - > 'lsass.exe'(1020)
c:\windows\moneap.dll
c:\windows\system32\WININET.dll
- - - - - - - > 'explorer.exe'(3432)
c:\windows\system32\WININET.dll
c:\windows\system32\ieframe.dll
c:\windows\moneap.dll
c:\program files\Bonjour\mdnsNSP.dll
c:\windows\system32\hnetcfg.dll
.
------------------------ Other Running Processes ------------------------
.
c:\windows\system32\scardsvr.exe
c:\program files\Common Files\Apple\Mobile Device Support\bin\AppleMobileDeviceService.exe
c:\program files\Common Files\Autodesk Shared\Service\AdskScSrv.exe
c:\program files\Bonjour\mDNSResponder.exe
c:\windows\system32\Crypserv.exe
c:\program files\Dell\QuickSet\NicConfigSvc.exe
c:\windows\system32\nvsvc32.exe
c:\windows\system32\HPZipm12.exe
c:\windows\system32\wdfmgr.exe
c:\windows\system32\wscntfy.exe
c:\windows\system32\rundll32.exe
c:\windows\system32\rundll32.exe
c:\windows\system32\opeia.exe
c:\windows\system32\lsm32.sys
.
**************************************************************************
.
Completion time: 2009-10-12 4:22 - machine was rebooted
ComboFix-quarantined-files.txt 2009-10-12 09:22
Pre-Run: 440,459,264 bytes free
Post-Run: 5,472,632,832 bytes free
WindowsXP-KB310994-SP2-Home-BootDisk-ENU.exe
[boot loader]
timeout=2
default=multi(0)disk(0)rdisk(0)partition(1)\WINDOWS
[operating systems]
c:\cmdcons\BOOTSECT.DAT="Microsoft Windows Recovery Console" /cmdcons
multi(0)disk(0)rdisk(0)partition(1)\WINDOWS="Microsoft Windows XP Home Edition" /noexecute=optin /fastdetect
295 --- E O F --- 2009-09-22 08:02
I am now positive the malware come from an infected torrent, for a skype plugin. I was in a hurry and did not look up comments on it. Stupid mistake.
Register to Remove
#11
![[Resolved] WinFixer woes: post #11](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 12 October 2009 - 07:08 AM
Some of the infections found on your machine have 'backdoor' capabilities, meaning they have the capability of compromising your personal information.
As a precaution, you should change all your passwords and notify your financial institutions that your personal information may have been compromised so they can put a watch on your account.
Peer to peer programs and torrents are a certain way to become infected. Many of the files/programs are injected with malicious code, just for the purpose of stealing your passwords and personal information.
You will be doing yourself a favour to remove them completely from your machine.
Please do the following:
- Very Important! Temporarily disable your anti-virus, script blocking and any anti-malware real-time protection before following the steps below.
- They can interfere with ComboFix or remove some of its embedded files which may cause "unpredictable results".
Here's how to do that:
Click Start > Run type Notepad click OK.
This will open an empty notepad file:
Copy all the text inside of the code box - Press Ctrl+C (or right click on the highlighted section and choose 'copy')
http://forums.whatthetech.com/WinFixer_woes_t107488.html&view=findpost&p=602393#entry602393 Collect:: c:\windows\wf4.dat c:\windows\wf3.dat c:\windows\system32\skynet.dat C:\fdgoti.exe C:\scxmgj.exe C:\gfsufon.exe C:\jyvtfwu.exe C:\srvgdoqj.exe c:\windows\system32\win4.tmp c:\windows\system32\kanelewu.exe c:\windows\system32\sobamehu.dll c:\windows\system32\win6.tmp c:\windows\system32\salizuya.dll c:\windows\system32\nifisofo.exe c:\windows\system32\gokisoso.dll c:\windows\system32\bovenage.dll c:\windows\system32\yomoviya.dll c:\windows\system32\win1F9D.tmp c:\windows\system32\opeia.exe c:\windows\system32\lsm32.sys c:\windows\moneap.dll KillAll:: Folder:: c:\documents and settings\All Users\Application Data\65104824 c:\documents and settings\All Users\Application Data\88742938 C:\PROGRAM1 Registry:: [HKEY_LOCAL_MACHINE\system\currentcontrolset\control\lsa] "Notification Packages"=hex(7):73,63,65,63,6c,69,00,41,43,47,69,6e,61,00,00 Driver:: AntiPol Rootkit:: c:\windows\system32\Install.txt
Now paste the copied text into the open notepad - press CTRL+V (or right click and choose 'paste')
Save this file to your desktop, Save this as "CFScript"
Here's how to do that:
1.Click File;
2.Click Save As... Change the directory to your desktop;
3.Change the Save as type to "All Files";
4.Type in the file name: CFScript
5.Click Save ...

- Referring to the screenshot above, drag CFScript.txt into ComboFix.exe.
- ComboFix will now run a scan on your system. It may reboot your system when it finishes. This is normal.
- When finished, it shall produce a log for you.
- Copy and paste the contents of the log in your next reply.
CAUTION: Do not mouse-click ComboFix's window while it is running. That may cause it to stall.
**Note**
When CF finishes running, the ComboFix log will open along with a message box--do not be alarmed. With the above script, ComboFix will capture files to submit for analysis.
- Ensure you are connected to the internet and click OK on the message box.
NEXT
- Please open your MalwareBytes AntiMalware Program
- Click the Update Tab and search for updates
- If an update is found, it will download and install the latest version.
- Once the program has loaded, select "Perform Quick Scan", then click Scan.
- The scan may take some time to finish, so please be patient.
- When the scan is complete, click OK, then Show Results to view the results.
- Make sure that everything is checked, and click Remove Selected. <-- very important
- When disinfection is completed, a log will open in Notepad and you may be prompted to Restart. (See Extra Note)
- The log is automatically saved by MBAM and can be viewed by clicking the Logs tab in MBAM.
- Copy&Paste the entire report in your next reply.
Extra Note:If MBAM encounters a file that is difficult to remove, you will be presented with 1 of 2 prompts, click OK to either and let MBAM proceed with the disinfection process, if asked to restart the computer, please do so immediately.
NEXT
Run an on-line scan with Kaspersky
Using Internet Explorer or Firefox, visit Kaspersky On-line Scanner
1. Click Accept, when prompted to download and install the program files and database of malware definitions.
2. To optimize scanning time and produce a more sensible report for review:
- Close any open programs
- Turn off the real time scanner of any existing antivirus program while performing the online scan
The program will then begin downloading and installing and will also update the database.
Please be patient as this can take several minutes.
- Once the update is complete, click on My Computer under the green Scan bar to the left to start the scan.
- Once the scan is complete, it will display if your system has been infected. It does not provide an option to clean/disinfect. We only require a report from it.
- Do NOT be alarmed by what you see in the report. Many of the finds have likely been quarantined.
- Click View scan report at the bottom.
- Click the Save as Text button to save the file to your desktop so that you may post it in your next reply
Microsoft MVP 2010, 2011, 2012, 2013, 2014, 2015
#12
![[Resolved] WinFixer woes: post #12](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 12 October 2009 - 07:37 AM
#13
![[Resolved] WinFixer woes: post #13](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 12 October 2009 - 07:45 AM
Microsoft MVP 2010, 2011, 2012, 2013, 2014, 2015
#14
![[Resolved] WinFixer woes: post #14](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 12 October 2009 - 11:18 PM
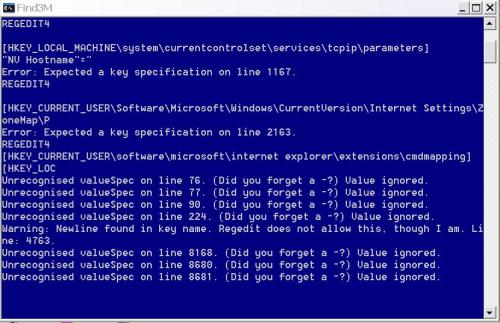
combofix seemed to be displaying some strange text, or it seemed strange to me. I took a screenshot and will attach it.
Here is the combofix log
ComboFix 09-10-12.03 - John 10/13/2009 0:03.2.2 - NTFSx86
Microsoft Windows XP Home Edition 5.1.2600.3.1252.1.1033.18.2046.1508 [GMT -5:00]
Running from: c:\documents and settings\John\Desktop\ComboFix.exe
Command switches used :: c:\documents and settings\John\Desktop\CFScript.txt
file zipped: C:\fdgoti.exe
file zipped: C:\gfsufon.exe
file zipped: C:\jyvtfwu.exe
file zipped: C:\scxmgj.exe
file zipped: C:\srvgdoqj.exe
file zipped: c:\windows\moneap.dll
file zipped: c:\windows\system32\bovenage.dll
file zipped: c:\windows\system32\gokisoso.dll
file zipped: c:\windows\system32\kanelewu.exe
file zipped: c:\windows\system32\lsm32.sys
file zipped: c:\windows\system32\nifisofo.exe
file zipped: c:\windows\system32\opeia.exe
file zipped: c:\windows\system32\salizuya.dll
file zipped: c:\windows\system32\skynet.dat
file zipped: c:\windows\system32\sobamehu.dll
file zipped: c:\windows\system32\win1F9D.tmp
file zipped: c:\windows\system32\win4.tmp
file zipped: c:\windows\system32\win6.tmp
file zipped: c:\windows\system32\yomoviya.dll
file zipped: c:\windows\wf3.dat
file zipped: c:\windows\wf4.dat
.
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
c:\documents and settings\All Users\Application Data\65104824
c:\documents and settings\All Users\Application Data\88742938
c:\documents and settings\John\Desktop\Security Tool.lnk
c:\documents and settings\John\Start Menu\Programs\Security Tool.lnk
c:\documents and settings\John\Start Menu\Programs\Windows Police Pro
c:\documents and settings\John\Start Menu\Programs\Windows Police Pro\Windows Police Pro.lnk
C:\fdgoti.exe
C:\gfsufon.exe
C:\jyvtfwu.exe
C:\PROGRAM1
c:\program1\CATDESC.CDX
c:\program1\CATDESC.DBF
c:\program1\CATDESC.FPT
c:\program1\CQUEST.EXE
c:\program1\FOXFONT.FON
c:\program1\FOXW2600.ESL
c:\program1\install.log
c:\program1\INTEREST.DBF
c:\program1\IQS.ICO
c:\program1\lslogo.bmp
c:\program1\OOH1999.CDX
c:\program1\OOH1999.DBF
c:\program1\OOH1999.FPT
c:\program1\QUESTION.DBF
c:\program1\unstall.exe
C:\scxmgj.exe
C:\srvgdoqj.exe
c:\windows\ibakulemu.dll
c:\windows\Install.txt
c:\windows\moneap.dll
c:\windows\system32\bovenage.dll
c:\windows\system32\FInstall.sys
c:\windows\system32\gokisoso.dll
c:\windows\system32\Install.txt
c:\windows\system32\kanelewu.exe
c:\windows\system32\lsm32.sys
c:\windows\system32\nifisofo.exe
c:\windows\system32\nuar.old
c:\windows\system32\opeia.exe
c:\windows\system32\salizuya.dll
c:\windows\system32\skynet.dat
c:\windows\system32\sobamehu.dll
c:\windows\system32\win1F9D.tmp
c:\windows\system32\win4.tmp
c:\windows\system32\win6.tmp
c:\windows\system32\yomoviya.dll
c:\windows\TEMP\mta83589.dll
c:\windows\wf3.dat
c:\windows\wf4.dat
.
((((((((((((((((((((((((((((((((((((((( Drivers/Services )))))))))))))))))))))))))))))))))))))))))))))))))
.
-------\Legacy_ANTIPOL
-------\Service_AntiPol
((((((((((((((((((((((((( Files Created from 2009-09-13 to 2009-10-13 )))))))))))))))))))))))))))))))
.
2009-10-13 04:53 . 2009-10-13 05:04 0 ----a-w- c:\windows\Cwawuqahiv.bin
2009-10-13 04:53 . 2009-10-13 04:53 120 ----a-w- c:\windows\Dgebeqicoxicak.dat
2009-10-12 09:25 . 2009-10-12 09:25 -------- d-----w- c:\documents and settings\John\Local Settings\Application Data\{4BF73112-CBC1-4A44-8924-6123A4FBDC00}
2009-10-12 07:15 . 2009-10-12 07:15 -------- d--h--w- c:\windows\PIF
2009-10-12 06:37 . 2009-10-12 06:37 -------- d-----w- c:\documents and settings\John\Application Data\Malwarebytes
2009-10-12 06:37 . 2009-09-10 19:54 38224 ----a-w- c:\windows\system32\drivers\mbamswissarmy.sys
2009-10-12 06:37 . 2009-10-12 06:37 -------- d-----w- c:\program files\Malwarebytes' Anti-Malware
2009-10-12 06:37 . 2009-10-12 06:37 -------- d-----w- c:\documents and settings\All Users\Application Data\Malwarebytes
2009-10-12 06:37 . 2009-09-10 19:53 19160 ----a-w- c:\windows\system32\drivers\mbam.sys
2009-10-09 00:49 . 2009-10-09 00:49 -------- d-----w- c:\documents and settings\John\Application Data\Pamela
2009-10-09 00:49 . 2009-10-09 00:49 175104 ----a-w- c:\windows\system32\RemoteControl.dll
2009-10-09 00:49 . 2009-10-09 00:53 -------- d-----w- c:\program files\Pamela
2009-10-09 00:36 . 2009-10-09 00:37 -------- d-----w- c:\documents and settings\All Users\Application Data\PrettyMay
2009-10-09 00:36 . 2009-10-09 00:36 -------- d-----w- c:\documents and settings\John\Application Data\PrettyMay
2009-09-24 00:56 . 2009-09-24 00:56 -------- d-----w- c:\program files\Kap.GRETests
2009-09-24 00:56 . 1999-02-25 11:32 122880 ----a-w- c:\windows\system32\fxtls532.dll
2009-09-24 00:56 . 1999-01-29 05:28 29184 ----a-w- c:\windows\system32\picn20.dll
2009-09-24 00:56 . 1999-03-26 00:00 101888 ----a-w- c:\windows\system32\VB6STKIT.DLL
2009-09-21 16:42 . 2009-06-21 21:44 153088 -c----w- c:\windows\system32\dllcache\triedit.dll
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2009-10-13 04:55 . 2009-07-17 15:16 -------- d-----w- c:\program files\TextAloud
2009-10-09 10:05 . 2009-04-16 14:25 -------- d-----w- c:\documents and settings\All Users\Application Data\Google Updater
2009-10-09 00:50 . 2009-05-06 17:12 -------- d-----w- c:\documents and settings\John\Application Data\Skype
2009-10-08 23:49 . 2009-05-06 17:14 -------- d-----w- c:\documents and settings\John\Application Data\skypePM
2009-10-08 08:57 . 2009-06-04 21:15 25 ----a-w- c:\windows\popcinfot.dat
2009-10-07 21:39 . 2009-02-14 01:09 -------- d-----w- c:\program files\IrfanView
2009-10-03 13:43 . 2009-02-21 23:02 -------- d-----w- c:\program files\BitComet
2009-10-03 02:14 . 2009-08-09 17:48 -------- d-----w- c:\program files\BFG
2009-10-03 02:02 . 2009-08-09 22:06 -------- d-----w- c:\program files\Codemasters
2009-10-03 02:02 . 2009-02-14 20:12 -------- d--h--w- c:\program files\InstallShield Installation Information
2009-09-30 06:32 . 2009-02-16 09:15 107888 ----a-w- c:\windows\system32\CmdLineExt.dll
2009-09-22 14:44 . 2009-02-16 02:48 60096 ----a-w- c:\windows\system32\nvModes.dat
2009-08-24 16:13 . 2009-03-11 21:19 -------- d-----w- c:\program files\PowerISO
2009-08-11 07:42 . 2009-02-18 03:36 100800 ----a-w- c:\documents and settings\John\Local Settings\Application Data\GDIPFONTCACHEV1.DAT
2009-08-10 05:42 . 2009-08-10 05:42 43520 ----a-w- c:\windows\system32\CmdLineExt03.dll
2009-08-09 18:24 . 2009-08-09 18:24 0 ----a-w- c:\windows\popcinfo.dat
2009-08-07 00:24 . 2009-02-13 02:02 327896 ----a-w- c:\windows\system32\wucltui.dll
2009-08-07 00:24 . 2009-02-13 02:02 209632 ----a-w- c:\windows\system32\wuweb.dll
2009-08-07 00:24 . 2009-02-13 02:02 35552 ----a-w- c:\windows\system32\wups.dll
2009-08-07 00:24 . 2008-10-16 20:09 44768 ----a-w- c:\windows\system32\wups2.dll
2009-08-07 00:24 . 2009-02-13 02:02 53472 ------w- c:\windows\system32\wuauclt.exe
2009-08-07 00:24 . 2004-08-12 13:56 96480 ----a-w- c:\windows\system32\cdm.dll
2009-08-07 00:23 . 2009-02-13 02:02 575704 ----a-w- c:\windows\system32\wuapi.dll
2009-08-07 00:23 . 2009-02-13 02:02 1929952 ----a-w- c:\windows\system32\wuaueng.dll
2009-08-05 09:01 . 2004-08-12 14:01 204800 ----a-w- c:\windows\system32\mswebdvd.dll
2009-07-29 03:42 . 2009-07-29 03:42 796672 ----a-w- c:\windows\GPInstall.exe
2009-07-27 02:43 . 2009-07-27 02:43 58908 ----a-w- c:\windows\system32\drivers\scdemu.sys
2009-07-17 19:01 . 2004-08-12 13:55 58880 ----a-w- c:\windows\system32\atl.dll
2003-12-18 16:33 . 2009-08-10 05:39 20102 ----a-w- c:\program files\Readme.txt
2003-09-03 12:46 . 2009-08-10 05:39 10960 ----a-w- c:\program files\EULA.txt
.
((((((((((((((((((((((((((((( SnapShot@2009-10-12_09.15.31 )))))))))))))))))))))))))))))))))))))))))
.
+ 2004-08-12 14:03 . 2009-10-13 04:57 68558 c:\windows\system32\perfc009.dat
- 2004-08-12 14:03 . 2009-10-12 08:53 68558 c:\windows\system32\perfc009.dat
+ 2004-08-12 13:56 . 2004-08-12 13:56 130048 c:\windows\system32\wmdtc.exe
+ 2004-08-12 14:03 . 2009-10-13 04:57 435828 c:\windows\system32\perfh009.dat
- 2004-08-12 14:03 . 2009-10-12 08:53 435828 c:\windows\system32\perfh009.dat
+ 2009-10-13 05:11 . 2009-06-29 16:12 1159680 c:\windows\temp\x1c51164.dll
+ 2009-10-13 05:11 . 2009-06-29 16:12 1159680 c:\windows\temp\mta64078.dll
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"DAEMON Tools Lite"="c:\program files\DAEMON Tools Lite\daemon.exe" [2009-04-23 691656]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"NvCplDaemon"="c:\windows\system32\NvCpl.dll" [2009-01-30 13594624]
"NvMediaCenter"="c:\windows\system32\NvMcTray.dll" [2009-01-30 86016]
"Dell QuickSet"="c:\program files\Dell\QuickSet\Quickset.exe" [2007-05-14 1191936]
"SigmatelSysTrayApp"="c:\program files\SigmaTel\C-Major Audio\WDM\stsystra.exe" [2007-05-10 405504]
"nwiz"="nwiz.exe" - c:\windows\system32\nwiz.exe [2009-01-30 1657376]
"NVHotkey"="nvHotkey.dll" - c:\windows\system32\nvhotkey.dll [2009-01-30 90112]
[HKEY_LOCAL_MACHINE\software\microsoft\windows nt\currentversion\winlogon\notify\GoToAssist]
2009-08-11 07:19 10536 ----a-w- c:\program files\Citrix\GoToAssist\514\g2awinlogon.dll
[HKLM\~\startupfolder\C:^Documents and Settings^John^Start Menu^Programs^Startup^Adobe Gamma.lnk]
path=c:\documents and settings\John\Start Menu\Programs\Startup\Adobe Gamma.lnk
backup=c:\windows\pss\Adobe Gamma.lnkStartup
[HKLM\~\startupfolder\C:^Documents and Settings^John^Start Menu^Programs^Startup^OneNote 2007 Screen Clipper and Launcher.lnk]
path=c:\documents and settings\John\Start Menu\Programs\Startup\OneNote 2007 Screen Clipper and Launcher.lnk
backup=c:\windows\pss\OneNote 2007 Screen Clipper and Launcher.lnkStartup
[HKEY_LOCAL_MACHINE\software\microsoft\security center]
"UpdatesDisableNotify"=dword:00000001
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile]
"EnableFirewall"= 0 (0x0)
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"%windir%\\system32\\sessmgr.exe"=
"%windir%\\Network Diagnostic\\xpnetdiag.exe"=
"c:\\Program Files\\Valve\\Steam\\SteamApps\\sulljoh1\\source sdk base 2007\\hl2.exe"=
"c:\\Program Files\\Opera\\opera.exe"=
"c:\\Program Files\\Valve\\Steam\\SteamApps\\sulljoh1\\source sdk base\\hl2.exe"=
"c:\\Program Files\\BitComet\\BitComet.exe"=
"c:\\Program Files\\Bonjour\\mDNSResponder.exe"=
"c:\\Program Files\\iTunes\\iTunes.exe"=
"c:\\Program Files\\LucasArts\\Star Wars Empire at War\\GameData\\sweaw.exe"=
"c:\\Documents and Settings\\John\\Local Settings\\Application Data\\Google\\Google Talk Plugin\\googletalkplugin.dll"=
"c:\\Documents and Settings\\John\\Local Settings\\Application Data\\Google\\Google Talk Plugin\\googletalkplugin.exe"=
"c:\\Program Files\\Google\\Google Talk\\googletalk.exe"=
"c:\\Program Files\\ICQ6.5\\ICQ.exe"=
"c:\\Program Files\\Autodesk\\3ds Max 9\\3dsmax.exe"=
"c:\\Program Files\\Autodesk\\Backburner\\monitor.exe"=
"c:\\Program Files\\Autodesk\\Backburner\\manager.exe"=
"c:\\Program Files\\Autodesk\\Backburner\\server.exe"=
"c:\\Program Files\\Microsoft Office\\Office12\\OUTLOOK.EXE"=
"c:\\Program Files\\Microsoft Office\\Office12\\GROOVE.EXE"=
"c:\\Program Files\\Microsoft Office\\Office12\\ONENOTE.EXE"=
"c:\\Program Files\\Codemasters\\Overlord\\Overlord.exe"=
"c:\\Program Files\\Codemasters\\Overlord II\\Overlord2.exe"=
"c:\\Program Files\\Skype\\Phone\\Skype.exe"=
"c:\\WINDOWS\\system32\\HPZipm12.exe"=
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\GloballyOpenPorts\List]
"15043:TCP"= 15043:TCP:BitComet 15043 TCP
"15043:UDP"= 15043:UDP:BitComet 15043 UDP
R2 BtwSrv;BtwSrv;c:\windows\system32\svchost.exe -k netsvcs [8/12/2004 9:06 AM 14336]
R2 fastnetsrv;fastnetsrv Service;c:\windows\system32\FastNetSrv.exe [8/12/2004 8:56 AM 94720]
R2 ICQ Service;ICQ Service;c:\program files\ICQ6Toolbar\ICQ Service.exe [4/14/2009 4:19 PM 222456]
S2 gupdate1c9be9f4c4ca05c;Google Update Service (gupdate1c9be9f4c4ca05c);c:\program files\Google\Update\GoogleUpdate.exe [4/16/2009 9:26 AM 133104]
--- Other Services/Drivers In Memory ---
*NewlyCreated* - BTWSRV
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost - NetSvcs
BtwSrv
.
Contents of the 'Scheduled Tasks' folder
2009-10-13 c:\windows\Tasks\Google Software Updater.job
- c:\program files\Google\Common\Google Updater\GoogleUpdaterService.exe [2009-04-16 14:25]
2009-10-13 c:\windows\Tasks\GoogleUpdateTaskMachineCore.job
- c:\program files\Google\Update\GoogleUpdate.exe [2009-04-16 14:26]
2009-10-10 c:\windows\Tasks\GoogleUpdateTaskMachineUA.job
- c:\program files\Google\Update\GoogleUpdate.exe [2009-04-16 14:26]
2009-10-08 c:\windows\Tasks\GoogleUpdateTaskUserS-1-5-21-1177238915-1844823847-725345543-1004Core.job
- c:\documents and settings\John\Local Settings\Application Data\Google\Update\GoogleUpdate.exe [2009-04-06 00:12]
2009-10-09 c:\windows\Tasks\GoogleUpdateTaskUserS-1-5-21-1177238915-1844823847-725345543-1004UA.job
- c:\documents and settings\John\Local Settings\Application Data\Google\Update\GoogleUpdate.exe [2009-04-06 00:12]
.
.
------- Supplementary Scan -------
.
uStart Page = hxxp://start.icq.com/
uInternet Settings,ProxyOverride = *.local
IE: &D&ownload &with BitComet - c:\program files\BitComet\BitComet.exe/AddLink.htm
IE: &D&ownload all video with BitComet - c:\program files\BitComet\BitComet.exe/AddVideo.htm
IE: &D&ownload all with BitComet - c:\program files\BitComet\BitComet.exe/AddAllLink.htm
IE: E&xport to Microsoft Excel - c:\progra~1\MICROS~2\Office12\EXCEL.EXE/3000
FF - ProfilePath - c:\documents and settings\John\Application Data\Mozilla\Firefox\Profiles\j1cizrmh.default\
FF - prefs.js: browser.startup.homepage - hxxp://forums.whatthetech.com/WinFixer_woes_t107488.html
FF - component: c:\program files\Mozilla Firefox\extensions\{B13721C7-F507-4982-B2E5-502A71474FED}\components\NPComponent.dll
FF - plugin: c:\documents and settings\John\Application Data\Mozilla\plugins\npgoogletalk.dll
FF - plugin: c:\documents and settings\John\Local Settings\Application Data\Google\Update\1.2.183.7\npGoogleOneClick8.dll
FF - plugin: c:\program files\Google\Google Updater\2.4.1536.6592\npCIDetect13.dll
FF - plugin: c:\program files\Google\Update\1.2.183.7\npGoogleOneClick8.dll
FF - plugin: c:\program files\Opera\program\plugins\nppl3260.dll
FF - plugin: c:\program files\Opera\program\plugins\nprpjplug.dll
FF - HiddenExtension: Microsoft .NET Framework Assistant: {20a82645-c095-46ed-80e3-08825760534b} - c:\windows\Microsoft.NET\Framework\v3.5\Windows Presentation Foundation\DotNetAssistantExtension\
FF - HiddenExtension: XULRunner: {4BF73112-CBC1-4A44-8924-6123A4FBDC00} - c:\documents and settings\John\Local Settings\Application Data\{4BF73112-CBC1-4A44-8924-6123A4FBDC00}
.
- - - - ORPHANS REMOVED - - - -
HKLM-Run-Grujekepem - c:\windows\ibakulemu.dll
**************************************************************************
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2009-10-13 00:11
Windows 5.1.2600 Service Pack 3 NTFS
scanning hidden processes ...
scanning hidden autostart entries ...
scanning hidden files ...
scan completed successfully
hidden files: 0
**************************************************************************
.
--------------------- LOCKED REGISTRY KEYS ---------------------
[HKEY_USERS\S-1-5-21-1177238915-1844823847-725345543-1004\Software\SecuROM\License information*]
"datasecu"=hex:98,83,92,bc,bd,a4,1b,90,d7,8b,71,08,35,d6,44,ac,c0,9a,4f,d7,88,
10,33,be,78,3a,0f,54,ee,6a,27,80,1f,f4,52,24,2c,b4,69,fa,6b,fb,ce,c2,af,e2,\
"rkeysecu"=hex:5c,6a,b3,2c,b9,5a,0d,e2,88,50,3c,5d,3e,01,f6,0e
.
--------------------- DLLs Loaded Under Running Processes ---------------------
- - - - - - - > 'winlogon.exe'(964)
c:\program files\Citrix\GoToAssist\514\G2AWinLogon.dll
- - - - - - - > 'explorer.exe'(3180)
c:\windows\system32\WININET.dll
c:\windows\system32\ieframe.dll
c:\program files\Common Files\Adobe\Acrobat\ActiveX\PDFShell.dll
c:\program files\Dell\QuickSet\dadkeyb.dll
.
------------------------ Other Running Processes ------------------------
.
c:\windows\system32\scardsvr.exe
c:\program files\Common Files\Apple\Mobile Device Support\bin\AppleMobileDeviceService.exe
c:\program files\Common Files\Autodesk Shared\Service\AdskScSrv.exe
c:\program files\Bonjour\mDNSResponder.exe
c:\windows\system32\Crypserv.exe
c:\program files\Dell\QuickSet\NicConfigSvc.exe
c:\windows\system32\nvsvc32.exe
c:\windows\system32\HPZipm12.exe
c:\windows\system32\wdfmgr.exe
c:\windows\system32\wscntfy.exe
c:\windows\system32\rundll32.exe
c:\windows\system32\rundll32.exe
c:\windows\system32\opeia.exe
c:\windows\system32\wbem\wmiadap.exe
c:\windows\system32\lsm32.sys
.
**************************************************************************
.
Completion time: 2009-10-13 0:15 - machine was rebooted
ComboFix-quarantined-files.txt 2009-10-13 05:15
ComboFix2.txt 2009-10-12 09:22
Pre-Run: 5,457,113,088 bytes free
Post-Run: 5,416,767,488 bytes free
296 --- E O F --- 2009-09-22 08:02
#15
![[Resolved] WinFixer woes: post #15](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 12 October 2009 - 11:26 PM
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users



 This topic is locked
This topic is locked