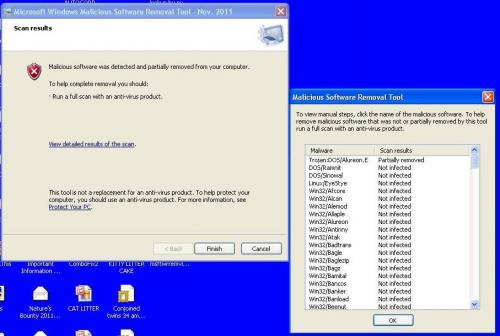
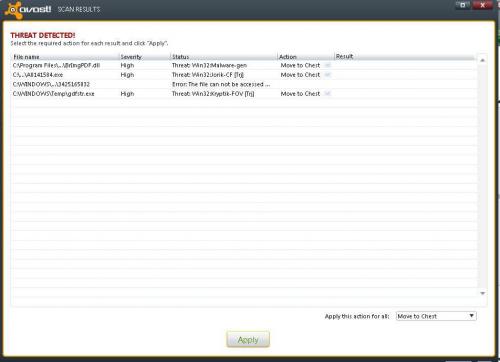
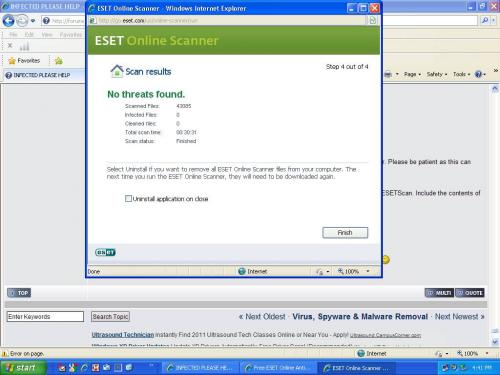
[/quote] No problem at all - there is no rush.
Thank you for being so patient with me

[/quote] All of those logs are very helpful

Great! I was so happy when I could finally get them for you

You did a really great job getting those tools to run

You are doing a fantastic job! I'm merely the puppet ...I was pulling out my hair before I got your help lol

[/quote] These should have re-appeared when ComboFix completed its run. Please let me know if they did.
They sure did

thank you!
Ok here we go with the new logs ....
(MBAM LOG)
Malwarebytes' Anti-Malware 1.51.2.1300
www.malwarebytes.org
Database version: 8129
Windows 5.1.2600 Service Pack 3
Internet Explorer 8.0.6001.18702
11/9/2011 11:48:16 PM
mbam-log-2011-11-09 (23-48-16).txt
Scan type: Full scan (C:\|)
Objects scanned: 270839
Time elapsed: 32 minute(s), 2 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 0
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 0
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
(No malicious items detected)
(JAVA)
It says that I already have the latest Java
(OTL log)
OTL logfile created on: 11/9/2011 11:53:14 PM - Run 2
OTL by OldTimer - Version 3.2.31.0 Folder = C:\Documents and Settings\Owner\Desktop\New Folder
Windows XP Professional Edition Service Pack 3 (Version = 5.1.2600) - Type = NTWorkstation
Internet Explorer (Version = 8.0.6001.18702)
Locale: 00000409 | Country: United States | Language: ENU | Date Format: M/d/yyyy
895.17 Mb Total Physical Memory | 409.20 Mb Available Physical Memory | 45.71% Memory free
2.12 Gb Paging File | 1.80 Gb Available in Paging File | 85.11% Paging File free
Paging file location(s): C:\pagefile.sys 1344 2688 [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\WINDOWS | %ProgramFiles% = C:\Program Files
Drive C: | 74.52 Gb Total Space | 50.34 Gb Free Space | 67.55% Space Free | Partition Type: NTFS
Computer Name: OWNER-BZ2MQ7E6C | User Name: Owner | Logged in as Administrator.
Boot Mode: Normal | Scan Mode: All users
Company Name Whitelist: Off | Skip Microsoft Files: Off | No Company Name Whitelist: On | File Age = 30 Days
========== Processes (SafeList) ==========
PRC - C:\Documents and Settings\Owner\Desktop\New Folder\OTL.exe (OldTimer Tools)
PRC - C:\Program Files\Alwil Software\Avast5\AvastSvc.exe (AVAST Software)
PRC - C:\WINDOWS\explorer.exe (Microsoft Corporation)
========== Modules (No Company Name) ==========
MOD - C:\Program Files\Alwil Software\Avast5\defs\11110901\algo.dll ()
MOD - C:\Program Files\Alwil Software\Avast5\defs\11110901\aswRep.dll ()
========== Win32 Services (SafeList) ==========
SRV - (HidServ) -- File not found
SRV - (avast! Antivirus) -- C:\Program Files\Alwil Software\Avast5\AvastSvc.exe (AVAST Software)
========== Driver Services (SafeList) ==========
DRV - (catchme) -- File not found
DRV - (aswSnx) -- C:\WINDOWS\System32\drivers\aswSnx.sys (AVAST Software)
DRV - (aswSP) -- C:\WINDOWS\System32\drivers\aswSP.sys (AVAST Software)
DRV - (aswRdr) -- C:\WINDOWS\System32\drivers\aswRdr.sys (AVAST Software)
DRV - (aswTdi) -- C:\WINDOWS\System32\drivers\aswTdi.sys (AVAST Software)
DRV - (aswMon2) -- C:\WINDOWS\System32\drivers\aswmon2.sys (AVAST Software)
DRV - (aswFsBlk) -- C:\WINDOWS\System32\drivers\aswFsBlk.sys (AVAST Software)
DRV - (Aavmker4) -- C:\WINDOWS\System32\drivers\aavmker4.sys (AVAST Software)
DRV - (IntcAzAudAddService) Service for Realtek HD Audio (WDM) -- C:\WINDOWS\system32\drivers\RtkHDAud.sys (Realtek Semiconductor Corp.)
DRV - (nvnetbus) -- C:\WINDOWS\system32\drivers\nvnetbus.sys (NVIDIA Corporation)
DRV - (NVENETFD) -- C:\WINDOWS\system32\drivers\NVENETFD.sys (NVIDIA Corporation)
========== Standard Registry (SafeList) ==========
========== Internet Explorer ==========
IE - HKU\.DEFAULT\SOFTWARE\Microsoft\Internet Explorer\Main,XMLHTTP_UUID_Default = 15 BD 6E 14 AB DF D9 49 AE 04 01 21 C8 32 35 AA [binary data]
IE - HKU\.DEFAULT\..\URLSearchHook: {A3BC75A2-1F87-4686-AA43-5347D756017C} - No CLSID value found
IE - HKU\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
IE - HKU\S-1-5-18\SOFTWARE\Microsoft\Internet Explorer\Main,XMLHTTP_UUID_Default = 15 BD 6E 14 AB DF D9 49 AE 04 01 21 C8 32 35 AA [binary data]
IE - HKU\S-1-5-18\..\URLSearchHook: {A3BC75A2-1F87-4686-AA43-5347D756017C} - No CLSID value found
IE - HKU\S-1-5-18\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
IE - HKU\S-1-5-19\SOFTWARE\Microsoft\Internet Explorer\Main,XMLHTTP_UUID_Default = 15 BD 6E 14 AB DF D9 49 AE 04 01 21 C8 32 35 AA [binary data]
IE - HKU\S-1-5-19\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
IE - HKU\S-1-5-20\SOFTWARE\Microsoft\Internet Explorer\Main,XMLHTTP_UUID_Default = 15 BD 6E 14 AB DF D9 49 AE 04 01 21 C8 32 35 AA [binary data]
IE - HKU\S-1-5-20\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
IE - HKU\S-1-5-21-854245398-764733703-725345543-1003\SOFTWARE\Microsoft\Internet Explorer\Main,SearchMigratedDefaultName = Google
IE - HKU\S-1-5-21-854245398-764733703-725345543-1003\SOFTWARE\Microsoft\Internet Explorer\Main,SearchMigratedDefaultURL =
http://www.google.co...m...tf8&oe=utf8
IE - HKU\S-1-5-21-854245398-764733703-725345543-1003\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page =
http://pogo.com/
IE - HKU\S-1-5-21-854245398-764733703-725345543-1003\SOFTWARE\Microsoft\Internet Explorer\Main,XMLHTTP_UUID_Default = 15 BD 6E 14 AB DF D9 49 AE 04 01 21 C8 32 35 AA [binary data]
IE - HKU\S-1-5-21-854245398-764733703-725345543-1003\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
FF - HKLM\Software\MozillaPlugins\@adobe.com/FlashPlayer: C:\WINDOWS\system32\Macromed\Flash\NPSWF32.dll ()
FF - HKLM\Software\MozillaPlugins\@adobe.com/ShockwavePlayer: C:\WINDOWS\system32\Adobe\Director\np32dsw.dll (Adobe Systems, Inc.)
FF - HKLM\Software\MozillaPlugins\@java.com/JavaPlugin: C:\Program Files\Java\jre6\bin\new_plugin\npjp2.dll (Sun Microsystems, Inc.)
FF - HKLM\Software\MozillaPlugins\@microsoft.com/WPF,version=3.5: c:\WINDOWS\Microsoft.NET\Framework\v3.5\Windows Presentation Foundation\NPWPF.dll (Microsoft Corporation)
FF - HKLM\Software\MozillaPlugins\Adobe Reader: C:\Program Files\Adobe\Reader 9.0\Reader\AIR\nppdf32.dll (Adobe Systems Inc.)
O1 HOSTS File: ([2011/11/09 14:25:00 | 000,000,027 | ---- | M]) - C:\WINDOWS\system32\drivers\etc\hosts
O1 - Hosts: 127.0.0.1 localhost
O2 - BHO: (avast! WebRep) - {8E5E2654-AD2D-48bf-AC2D-D17F00898D06} - C:\Program Files\Alwil Software\Avast5\aswWebRepIE.dll (AVAST Software)
O3 - HKLM\..\Toolbar: (no name) - {2318C2B1-4965-11d4-9B18-009027A5CD4F} - No CLSID value found.
O3 - HKLM\..\Toolbar: (avast! WebRep) - {8E5E2654-AD2D-48bf-AC2D-D17F00898D06} - C:\Program Files\Alwil Software\Avast5\aswWebRepIE.dll (AVAST Software)
O3 - HKLM\..\Toolbar: (no name) - {A057A204-BACC-4D26-9990-79A187E2698E} - No CLSID value found.
O3 - HKU\S-1-5-21-854245398-764733703-725345543-1003\..\Toolbar\ShellBrowser: (no name) - {CCC7A320-B3CA-4199-B1A6-9F516DD69829} - No CLSID value found.
O3 - HKU\S-1-5-21-854245398-764733703-725345543-1003\..\Toolbar\WebBrowser: (no name) - {A057A204-BACC-4D26-9990-79A187E2698E} - No CLSID value found.
O3 - HKU\S-1-5-21-854245398-764733703-725345543-1003\..\Toolbar\WebBrowser: (no name) - {D7E97865-918F-41E4-9CD0-25AB1C574CE8} - No CLSID value found.
O4 - HKLM..\Run: [NvCplDaemon] C:\WINDOWS\System32\NvCpl.dll (NVIDIA Corporation)
O6 - HKLM\Software\Policies\Microsoft\Internet Explorer\Restrictions present
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: HonorAutoRunSetting = 1
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDrives = 0
O7 - HKU\.DEFAULT\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKU\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O7 - HKU\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O7 - HKU\S-1-5-18\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKU\S-1-5-18\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O7 - HKU\S-1-5-18\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O7 - HKU\S-1-5-19\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKU\S-1-5-19\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 145
O7 - HKU\S-1-5-20\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKU\S-1-5-20\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 145
O7 - HKU\S-1-5-21-854245398-764733703-725345543-1003\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKU\S-1-5-21-854245398-764733703-725345543-1003\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O7 - HKU\S-1-5-21-854245398-764733703-725345543-1003\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O7 - HKU\S-1-5-21-854245398-764733703-725345543-1003\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDrives = 0
O10 - NameSpace_Catalog5\Catalog_Entries\000000000004 [] - C:\Program Files\Bonjour\mdnsNSP.dll (Apple Inc.)
O15 - HKU\S-1-5-21-854245398-764733703-725345543-1003\..Trusted Domains: ([]msn in My Computer)
O16 - DPF: {0CCA191D-13A6-4E29-B746-314DEE697D83}
http://upload.facebo...toUploader5.cab (Facebook Photo Uploader 5 Control)
O16 - DPF: {166B1BCA-3F9C-11CF-8075-444553540000}
http://download.macr...director/sw.cab (Shockwave ActiveX Control)
O16 - DPF: {233C1507-6A77-46A4-9443-F871F945D258}
http://download.macr...director/sw.cab (Shockwave ActiveX Control)
O16 - DPF: {2BC66F54-93A8-11D3-BEB6-00105AA9B6AE}
http://security.syma...bin/AvSniff.cab (Symantec AntiVirus scanner)
O16 - DPF: {6414512B-B978-451D-A0D8-FCFDF33E833C}
http://www.update.mi...b?1221784093359 (WUWebControl Class)
O16 - DPF: {644E432F-49D3-41A1-8DD5-E099162EEEC5}
http://security.syma...n/bin/cabsa.cab (Symantec RuFSI Utility Class)
O16 - DPF: {6E32070A-766D-4EE6-879C-DC1FA91D2FC3}
http://www.update.mi...b?1256451306250 (MUWebControl Class)
O16 - DPF: {8100D56A-5661-482C-BEE8-AFECE305D968}
http://upload.facebo...oUploader55.cab (Facebook Photo Uploader 5 Control)
O16 - DPF: {8AD9C840-044E-11D1-B3E9-00805F499D93}
http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_29)
O16 - DPF: {8FFBE65D-2C9C-4669-84BD-5829DC0B603C}
http://fpdownload.ma...t/ultrashim.cab (Reg Error: Key error.)
O16 - DPF: {9C23D886-43CB-43DE-B2DB-112A68D7E10A}
http://lads.myspace....ceUploader2.cab (MySpace Uploader Control)
O16 - DPF: {CAFEEFAC-0016-0000-0029-ABCDEFFEDCBA}
http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_29)
O16 - DPF: {CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA}
http://java.sun.com/...indows-i586.cab (Java Plug-in 1.6.0_29)
O16 - DPF: {E2883E8F-472F-4FB0-9522-AC9BF37916A7}
http://platformdl.ad...Plus/1.6/gp.cab (Reg Error: Key error.)
O17 - HKLM\System\CCS\Services\Tcpip\Parameters: DhcpNameServer = 68.87.72.134 68.87.77.134
O17 - HKLM\System\CCS\Services\Tcpip\Parameters\Interfaces\{722AA42D-3320-47D2-A261-FC87E700BDDD}: DhcpNameServer = 68.87.72.134 68.87.77.134
O20 - HKLM Winlogon: Shell - (Explorer.exe) -C:\WINDOWS\explorer.exe (Microsoft Corporation)
O20 - HKLM Winlogon: UserInit - (C:\WINDOWS\system32\userinit.exe) -C:\WINDOWS\system32\userinit.exe (Microsoft Corporation)
O24 - Desktop WallPaper: C:\Documents and Settings\Owner\Local Settings\Application Data\Microsoft\Wallpaper1.bmp
O24 - Desktop BackupWallPaper: C:\Documents and Settings\Owner\Local Settings\Application Data\Microsoft\Wallpaper1.bmp
O32 - HKLM CDRom: AutoRun - 1
O32 - AutoRun File - [2008/09/18 12:42:24 | 000,000,000 | ---- | M] () - C:\AUTOEXEC.BAT -- [ NTFS ]
O34 - HKLM BootExecute: (autocheck autochk *)
O35 - HKLM\..comfile [open] -- "%1" %*
O35 - HKLM\..exefile [open] -- "%1" %*
O37 - HKLM\...com [@ = ComFile] -- "%1" %*
O37 - HKLM\...exe [@ = exefile] -- "%1" %*
========== Files/Folders - Created Within 30 Days ==========
[2011/11/09 15:05:05 | 000,000,000 | -HSD | C] -- C:\RECYCLER
[2011/11/09 14:18:31 | 000,000,000 | ---D | C] -- C:\WINDOWS\temp
[2011/11/09 14:18:25 | 000,062,976 | ---- | C] (Microsoft Corporation) -- C:\WINDOWS\System32\dllcache\cdrom.sys
[2011/11/09 13:38:07 | 000,000,000 | ---D | C] -- C:\_OTL
[2011/11/09 06:34:28 | 000,000,000 | -H-D | C] -- C:\WINDOWS\PIF
[2011/11/09 05:43:55 | 000,000,000 | ---D | C] -- C:\WINDOWS\Minidump
[2011/11/09 05:37:22 | 004,287,742 | R--- | C] (Swearware) -- C:\jontom.com
[2011/11/08 12:09:22 | 000,000,000 | RHSD | C] -- C:\cmdcons
[2011/11/08 12:07:06 | 000,518,144 | ---- | C] (SteelWerX) -- C:\WINDOWS\SWREG.exe
[2011/11/08 12:07:06 | 000,406,528 | ---- | C] (SteelWerX) -- C:\WINDOWS\SWSC.exe
[2011/11/08 12:07:06 | 000,212,480 | ---- | C] (SteelWerX) -- C:\WINDOWS\SWXCACLS.exe
[2011/11/08 12:07:06 | 000,060,416 | ---- | C] (NirSoft) -- C:\WINDOWS\NIRCMD.exe
[2011/11/08 12:06:57 | 000,000,000 | ---D | C] -- C:\WINDOWS\ERDNT
[2011/11/08 12:06:49 | 000,000,000 | ---D | C] -- C:\Qoobox
[2011/11/07 13:32:18 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Start Menu\Programs\HijackThis
[2011/11/07 13:12:20 | 000,000,000 | ---D | C] -- C:\Documents and Settings\Owner\Desktop\M
[2011/11/07 09:13:17 | 000,472,808 | ---- | C] (Sun Microsystems, Inc.) -- C:\WINDOWS\System32\deployJava1.dll
[2011/11/07 09:13:17 | 000,157,472 | ---- | C] (Sun Microsystems, Inc.) -- C:\WINDOWS\System32\javaws.exe
[2011/11/07 09:13:17 | 000,145,184 | ---- | C] (Sun Microsystems, Inc.) -- C:\WINDOWS\System32\javaw.exe
[2011/11/07 09:13:17 | 000,145,184 | ---- | C] (Sun Microsystems, Inc.) -- C:\WINDOWS\System32\java.exe
[2011/11/07 01:32:03 | 000,000,000 | ---D | C] -- C:\Documents and Settings\Owner\Desktop\New Folder
[2011/11/07 01:20:23 | 000,607,260 | R--- | C] (Swearware) -- C:\Documents and Settings\Owner\Desktop\dds.scr
[2011/11/07 01:19:12 | 000,388,608 | ---- | C] (Trend Micro Inc.) -- C:\Documents and Settings\Owner\Desktop\HiJackThis.exe
[2011/11/06 19:56:41 | 000,000,000 | ---D | C] -- C:\Documents and Settings\NetworkService\Application Data\Sun
[2011/11/06 19:48:40 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Start Menu\Programs\Malwarebytes' Anti-Malware
[2011/11/06 19:48:36 | 000,022,216 | ---- | C] (Malwarebytes Corporation) -- C:\WINDOWS\System32\drivers\mbam.sys
[2011/11/06 19:48:36 | 000,000,000 | ---D | C] -- C:\Program Files\Malwarebytes' Anti-Malware
[2011/11/06 18:17:43 | 000,000,000 | R--D | C] -- C:\Documents and Settings\Owner\Recent
[2011/11/06 16:55:40 | 000,000,000 | ---D | C] -- C:\Documents and Settings\NetworkService\Local Settings\Application Data\Adobe
[2011/11/06 05:46:28 | 000,000,000 | ---D | C] -- C:\Documents and Settings\NetworkService\Application Data\Macromedia
[2011/11/06 05:46:07 | 000,000,000 | ---D | C] -- C:\Documents and Settings\NetworkService\Application Data\Adobe
[2011/10/18 16:30:49 | 000,000,000 | ---D | C] -- C:\extensions
[2011/10/18 16:30:48 | 000,000,000 | ---D | C] -- C:\Program Files\Conduit
[2011/10/18 16:30:46 | 000,000,000 | ---D | C] -- C:\Documents and Settings\Owner\Local Settings\Application Data\Temp
[2011/10/18 16:30:46 | 000,000,000 | ---D | C] -- C:\Documents and Settings\Owner\Local Settings\Application Data\Conduit
[2011/10/18 16:29:45 | 000,000,000 | ---D | C] -- C:\Documents and Settings\Owner\Application Data\uTorrent
[2011/10/16 03:12:52 | 000,000,000 | ---D | C] -- C:\Documents and Settings\Owner\Application Data\SulusGames
[2011/10/16 03:12:52 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Application Data\SulusGames
[2011/10/16 03:11:56 | 000,000,000 | ---D | C] -- C:\Program Files\Strange Cases - The Tarot Card Mystery
[2011/10/16 03:11:56 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Start Menu\Programs\Strange Cases - The Tarot Card Mystery
[2011/10/16 03:09:38 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Application Data\Big Fish Games
[2011/10/16 03:08:30 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Application Data\BigFishGamesCache
[5 C:\WINDOWS\*.tmp files -> C:\WINDOWS\*.tmp -> ]
[1 C:\WINDOWS\System32\*.tmp files -> C:\WINDOWS\System32\*.tmp -> ]
[1 C:\Documents and Settings\Owner\Desktop\*.tmp files -> C:\Documents and Settings\Owner\Desktop\*.tmp -> ]
========== Files - Modified Within 30 Days ==========
[2011/11/09 14:25:11 | 000,002,206 | ---- | M] () -- C:\WINDOWS\System32\wpa.dbl
[2011/11/09 14:25:00 | 000,000,027 | ---- | M] () -- C:\WINDOWS\System32\drivers\etc\hosts
[2011/11/09 14:24:45 | 000,002,048 | --S- | M] () -- C:\WINDOWS\bootstat.dat
[2011/11/09 14:07:07 | 004,287,742 | R--- | M] (Swearware) -- C:\jontom.com
[2011/11/09 03:20:36 | 000,000,129 | ---- | M] () -- C:\WINDOWS\System32\MRT.INI
[2011/11/08 16:17:41 | 000,433,098 | ---- | M] () -- C:\WINDOWS\System32\perfh009.dat
[2011/11/08 16:17:41 | 000,067,862 | ---- | M] () -- C:\WINDOWS\System32\perfc009.dat
[2011/11/08 12:09:27 | 000,000,339 | RHS- | M] () -- C:\boot.ini
[2011/11/07 21:14:43 | 000,031,351 | ---- | M] () -- C:\Documents and Settings\Owner\Desktop\Documentapril.rtf
[2011/11/07 13:22:36 | 000,001,324 | ---- | M] () -- C:\WINDOWS\System32\d3d9caps.dat
[2011/11/07 09:16:23 | 000,000,223 | ---- | M] () -- C:\Boot.bak
[2011/11/07 01:20:24 | 000,607,260 | R--- | M] (Swearware) -- C:\Documents and Settings\Owner\Desktop\dds.scr
[2011/11/07 01:19:13 | 000,388,608 | ---- | M] (Trend Micro Inc.) -- C:\Documents and Settings\Owner\Desktop\HiJackThis.exe
[2011/11/06 20:14:58 | 000,000,194 | -HS- | M] () -- C:\Program Files\Common Files\winset.ini
[2011/11/06 05:07:53 | 000,000,211 | ---- | M] () -- C:\Documents and Settings\Owner\Desktop\Google.url
[2011/11/05 20:30:38 | 000,035,122 | ---- | M] () -- C:\Documents and Settings\Owner\Desktop\funny-facebook-fails-wrap-your-head-around-that-math.jpg
[2011/11/05 20:30:37 | 000,048,042 | ---- | M] () -- C:\Documents and Settings\Owner\Desktop\funny-facebook-fails-its-important-to-know-where-to-measure-from.jpg
[2011/11/05 17:46:51 | 000,029,943 | ---- | M] () -- C:\Documents and Settings\Owner\Desktop\jeffrey-campbell-lita-shag.jpg
[2011/11/05 03:51:58 | 000,000,179 | ---- | M] () -- C:\Documents and Settings\Owner\Desktop\LoudCity.com.url
[2011/11/04 08:20:54 | 000,020,553 | ---- | M] () -- C:\Documents and Settings\Owner\Desktop\Important Information Regarding the National EAS Test on Nov_ 9.eml
[2011/11/02 19:35:00 | 000,012,734 | ---- | M] () -- C:\Documents and Settings\Owner\Desktop\JOB CREATED.jpg
[2011/11/02 19:03:52 | 000,302,346 | ---- | M] () -- C:\Documents and Settings\Owner\Desktop\Find area code lookup by number on WebShoppingHelper.mht
[2011/10/24 03:18:51 | 000,000,119 | ---- | M] () -- C:\Documents and Settings\Owner\Desktop\dayam YOU AUTOCORRECT.url
[2011/10/21 21:13:52 | 000,010,467 | ---- | M] () -- C:\Documents and Settings\Owner\Desktop\JEALOUS WOMEN.jpg
[2011/10/21 02:47:09 | 000,000,139 | ---- | M] () -- C:\Documents and Settings\Owner\Desktop\Tippecanoe Waste Removal, Inc Home.url
[2011/10/17 04:03:42 | 000,001,210 | ---- | M] () -- C:\Documents and Settings\Owner\Desktop\Earmarks Map – 2011 Requests Ending Spending EndingSpending.com.url
[2011/10/17 03:20:21 | 001,333,597 | ---- | M] () -- C:\Documents and Settings\Owner\Desktop\Jakie_time_out_lol.jpg
[2011/10/15 20:09:32 | 000,414,368 | ---- | M] (Adobe Systems Incorporated) -- C:\WINDOWS\System32\FlashPlayerCPLApp.cpl
[2011/10/13 17:57:09 | 000,148,400 | ---- | M] () -- C:\WINDOWS\System32\FNTCACHE.DAT
[2011/10/13 03:34:47 | 000,001,393 | ---- | M] () -- C:\WINDOWS\imsins.BAK
[2011/10/11 17:11:59 | 000,882,519 | ---- | M] () -- C:\Documents and Settings\Owner\Desktop\Conjoined twins 34 amazing photos (GRAPHIC IMAGES) Pictures - CBS News.mht
[2011/10/11 15:13:51 | 000,007,919 | ---- | M] () -- C:\Documents and Settings\Owner\Desktop\Be Strong and Save Now with Os-Cal.eml
[2011/10/11 04:26:38 | 000,000,172 | ---- | M] () -- C:\Documents and Settings\Owner\Desktop\Free Polls, Questions, and Answers, News Discussions - SodaHead.url
[5 C:\WINDOWS\*.tmp files -> C:\WINDOWS\*.tmp -> ]
[1 C:\WINDOWS\System32\*.tmp files -> C:\WINDOWS\System32\*.tmp -> ]
[1 C:\Documents and Settings\Owner\Desktop\*.tmp files -> C:\Documents and Settings\Owner\Desktop\*.tmp -> ]
========== Files Created - No Company Name ==========
[2011/11/09 14:15:22 | 000,000,784 | ---- | C] () -- C:\Documents and Settings\All Users\Desktop\Malwarebytes' Anti-Malware.lnk
[2011/11/09 14:15:22 | 000,000,242 | ---- | C] () -- C:\Documents and Settings\Owner\Application Data\Microsoft\Internet Explorer\Quick Launch\Shortcut to Internet Options.lnk
[2011/11/09 03:20:36 | 000,000,129 | ---- | C] () -- C:\WINDOWS\System32\MRT.INI
[2011/11/08 12:09:27 | 000,000,223 | ---- | C] () -- C:\Boot.bak
[2011/11/08 12:09:26 | 000,260,272 | RHS- | C] () -- C:\cmldr
[2011/11/08 12:07:06 | 000,256,000 | ---- | C] () -- C:\WINDOWS\PEV.exe
[2011/11/08 12:07:06 | 000,208,896 | ---- | C] () -- C:\WINDOWS\MBR.exe
[2011/11/08 12:07:06 | 000,098,816 | ---- | C] () -- C:\WINDOWS\sed.exe
[2011/11/08 12:07:06 | 000,080,412 | ---- | C] () -- C:\WINDOWS\grep.exe
[2011/11/08 12:07:06 | 000,068,096 | ---- | C] () -- C:\WINDOWS\zip.exe
[2011/11/07 13:32:19 | 000,000,815 | ---- | C] () -- C:\Documents and Settings\Owner\Application Data\Microsoft\Internet Explorer\Quick Launch\Launch Internet Explorer Browser.lnk
[2011/11/07 13:32:19 | 000,000,802 | ---- | C] () -- C:\Documents and Settings\Owner\Application Data\Microsoft\Internet Explorer\Quick Launch\Malwarebytes' Anti-Malware.lnk
[2011/11/07 13:32:19 | 000,000,800 | ---- | C] () -- C:\Documents and Settings\Owner\Application Data\Microsoft\Internet Explorer\Quick Launch\Windows Media Player.lnk
[2011/11/07 13:32:19 | 000,000,738 | ---- | C] () -- C:\Documents and Settings\Owner\Application Data\Microsoft\Internet Explorer\Quick Launch\Outlook Express.lnk
[2011/11/07 13:32:19 | 000,000,680 | ---- | C] () -- C:\Documents and Settings\Owner\Application Data\Microsoft\Internet Explorer\Quick Launch\EmailStripper.lnk
[2011/11/07 13:32:19 | 000,000,671 | ---- | C] () -- C:\Documents and Settings\Owner\Application Data\Microsoft\Internet Explorer\Quick Launch\Shortcut to XuMouse.lnk
[2011/11/07 13:32:19 | 000,000,211 | ---- | C] () -- C:\Documents and Settings\Owner\Application Data\Microsoft\Internet Explorer\Quick Launch\Google.url
[2011/11/07 13:32:19 | 000,000,079 | ---- | C] () -- C:\Documents and Settings\Owner\Application Data\Microsoft\Internet Explorer\Quick Launch\Show Desktop.scf
[2011/11/07 13:32:17 | 000,002,391 | ---- | C] () -- C:\Documents and Settings\All Users\Start Menu\Programs\Microsoft Office PowerPoint Viewer 2007.lnk
[2011/11/07 13:32:17 | 000,002,347 | ---- | C] () -- C:\Documents and Settings\All Users\Start Menu\Programs\Adobe Reader 9.lnk
[2011/11/07 13:32:17 | 000,001,844 | ---- | C] () -- C:\Documents and Settings\All Users\Start Menu\Programs\MSN Explorer.lnk
[2011/11/07 13:32:17 | 000,001,830 | ---- | C] () -- C:\Documents and Settings\All Users\Start Menu\Programs\Apple Software Update.lnk
[2011/11/07 13:32:17 | 000,000,785 | ---- | C] () -- C:\Documents and Settings\All Users\Start Menu\Programs\Windows Messenger.lnk
[2011/11/07 13:32:17 | 000,000,740 | ---- | C] () -- C:\Documents and Settings\All Users\Start Menu\Programs\Acrobat.com.lnk
[2011/11/06 20:03:26 | 000,000,194 | -HS- | C] () -- C:\Program Files\Common Files\winset.ini
[2011/11/06 05:47:25 | 000,001,324 | ---- | C] () -- C:\WINDOWS\System32\d3d9caps.dat
[2011/11/05 20:34:15 | 000,035,122 | ---- | C] () -- C:\Documents and Settings\Owner\Desktop\funny-facebook-fails-wrap-your-head-around-that-math.jpg
[2011/11/05 20:32:09 | 000,048,042 | ---- | C] () -- C:\Documents and Settings\Owner\Desktop\funny-facebook-fails-its-important-to-know-where-to-measure-from.jpg
[2011/11/05 17:52:54 | 000,029,943 | ---- | C] () -- C:\Documents and Settings\Owner\Desktop\jeffrey-campbell-lita-shag.jpg
[2011/11/04 08:48:16 | 000,031,351 | ---- | C] () -- C:\Documents and Settings\Owner\Desktop\Documentapril.rtf
[2011/11/04 08:20:54 | 000,020,553 | ---- | C] () -- C:\Documents and Settings\Owner\Desktop\Important Information Regarding the National EAS Test on Nov_ 9.eml
[2011/11/02 19:36:28 | 000,012,734 | ---- | C] () -- C:\Documents and Settings\Owner\Desktop\JOB CREATED.jpg
[2011/11/02 19:03:47 | 000,302,346 | ---- | C] () -- C:\Documents and Settings\Owner\Desktop\Find area code lookup by number on WebShoppingHelper.mht
[2011/10/24 03:18:51 | 000,000,119 | ---- | C] () -- C:\Documents and Settings\Owner\Desktop\dayam YOU AUTOCORRECT.url
[2011/10/21 21:16:50 | 000,010,467 | ---- | C] () -- C:\Documents and Settings\Owner\Desktop\JEALOUS WOMEN.jpg
[2011/10/21 02:47:09 | 000,000,139 | ---- | C] () -- C:\Documents and Settings\Owner\Desktop\Tippecanoe Waste Removal, Inc Home.url
[2011/10/17 04:03:42 | 000,001,210 | ---- | C] () -- C:\Documents and Settings\Owner\Desktop\Earmarks Map – 2011 Requests Ending Spending EndingSpending.com.url
[2011/10/17 03:20:30 | 001,333,597 | ---- | C] () -- C:\Documents and Settings\Owner\Desktop\Jakie_time_out_lol.jpg
[2011/10/11 17:11:51 | 000,882,519 | ---- | C] () -- C:\Documents and Settings\Owner\Desktop\Conjoined twins 34 amazing photos (GRAPHIC IMAGES) Pictures - CBS News.mht
[2011/10/11 15:13:51 | 000,007,919 | ---- | C] () -- C:\Documents and Settings\Owner\Desktop\Be Strong and Save Now with Os-Cal.eml
[2011/01/15 05:33:35 | 000,091,712 | ---- | C] () -- C:\Documents and Settings\LocalService\Local Settings\Application Data\FontCache3.0.0.0.dat
[2010/01/05 17:01:21 | 000,000,000 | ---- | C] () -- C:\WINDOWS\nsreg.dat
[2009/09/14 20:12:31 | 000,017,532 | ---- | C] () -- C:\WINDOWS\System32\mlfcache.dat
[2009/08/03 15:07:42 | 000,403,816 | ---- | C] () -- C:\WINDOWS\System32\OGACheckControl.dll
[2009/08/03 15:07:42 | 000,230,768 | ---- | C] () -- C:\WINDOWS\System32\OGAEXEC.exe
[2009/06/30 22:53:06 | 000,000,797 | ---- | C] () -- C:\Documents and Settings\Owner\Application Data\Launch Internet Explorer Browser.lnk
[2009/05/25 18:40:40 | 000,000,419 | ---- | C] () -- C:\WINDOWS\BRWMARK.INI
[2009/05/25 18:40:40 | 000,000,027 | ---- | C] () -- C:\WINDOWS\BRPP2KA.INI
[2009/05/25 18:38:56 | 000,000,228 | ---- | C] () -- C:\WINDOWS\Brpfx04a.ini
[2009/05/25 18:38:56 | 000,000,094 | ---- | C] () -- C:\WINDOWS\brpcfx.ini
[2009/05/25 18:38:56 | 000,000,050 | ---- | C] () -- C:\WINDOWS\System32\bridf06a.dat
[2009/05/25 18:38:11 | 000,106,496 | ---- | C] () -- C:\WINDOWS\System32\BrMuSNMP.dll
[2009/05/25 18:38:11 | 000,000,000 | ---- | C] () -- C:\WINDOWS\brdfxspd.dat
[2009/02/23 21:52:49 | 000,000,069 | ---- | C] () -- C:\WINDOWS\NeroDigital.ini
[2009/02/13 00:25:32 | 000,000,754 | ---- | C] () -- C:\WINDOWS\WORDPAD.INI
[2008/11/12 03:11:23 | 000,010,240 | ---- | C] () -- C:\Documents and Settings\Owner\Local Settings\Application Data\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini
[2008/09/19 01:58:51 | 000,172,032 | ---- | C] () -- C:\WINDOWS\System32\adsubtb.dll
[2008/09/19 01:58:51 | 000,002,150 | ---- | C] () -- C:\WINDOWS\System32\nshxml.ini
[2008/09/18 13:20:44 | 000,049,152 | R--- | C] () -- C:\WINDOWS\System32\ChCfg.exe
[2008/09/18 12:56:12 | 000,001,732 | R--- | C] () -- C:\WINDOWS\System32\drivers\nvphy.bin
[2008/09/18 12:44:31 | 000,002,048 | --S- | C] () -- C:\WINDOWS\bootstat.dat
[2008/09/18 12:39:12 | 000,021,640 | ---- | C] () -- C:\WINDOWS\System32\emptyregdb.dat
[2008/09/18 08:35:22 | 000,004,161 | ---- | C] () -- C:\WINDOWS\ODBCINST.INI
[2008/09/18 08:34:05 | 000,148,400 | ---- | C] () -- C:\WINDOWS\System32\FNTCACHE.DAT
[2007/04/20 08:32:00 | 001,703,936 | ---- | C] () -- C:\WINDOWS\System32\nvwdmcpl.dll
[2007/04/20 08:32:00 | 001,626,112 | ---- | C] () -- C:\WINDOWS\System32\nwiz.exe
[2007/04/20 08:32:00 | 001,474,560 | ---- | C] () -- C:\WINDOWS\System32\nview.dll
[2007/04/20 08:32:00 | 001,339,392 | ---- | C] () -- C:\WINDOWS\System32\nvdspsch.exe
[2007/04/20 08:32:00 | 001,019,904 | ---- | C] () -- C:\WINDOWS\System32\nvwimg.dll
[2007/04/20 08:32:00 | 001,018,748 | ---- | C] () -- C:\WINDOWS\System32\nvucode.bin
[2007/04/20 08:32:00 | 000,466,944 | ---- | C] () -- C:\WINDOWS\System32\nvshell.dll
[2007/04/20 08:32:00 | 000,442,368 | ---- | C] () -- C:\WINDOWS\System32\nvappbar.exe
[2007/04/20 08:32:00 | 000,425,984 | ---- | C] () -- C:\WINDOWS\System32\keystone.exe
[2007/04/20 08:32:00 | 000,286,720 | ---- | C] () -- C:\WINDOWS\System32\nvnt4cpl.dll
[2004/08/02 13:20:40 | 000,004,569 | ---- | C] () -- C:\WINDOWS\System32\secupd.dat
[2001/08/23 07:00:00 | 013,107,200 | ---- | C] () -- C:\WINDOWS\System32\oembios.bin
[2001/08/23 07:00:00 | 000,673,088 | ---- | C] () -- C:\WINDOWS\System32\mlang.dat
[2001/08/23 07:00:00 | 000,433,098 | ---- | C] () -- C:\WINDOWS\System32\perfh009.dat
[2001/08/23 07:00:00 | 000,272,128 | ---- | C] () -- C:\WINDOWS\System32\perfi009.dat
[2001/08/23 07:00:00 | 000,218,003 | ---- | C] () -- C:\WINDOWS\System32\dssec.dat
[2001/08/23 07:00:00 | 000,067,862 | ---- | C] () -- C:\WINDOWS\System32\perfc009.dat
[2001/08/23 07:00:00 | 000,046,258 | ---- | C] () -- C:\WINDOWS\System32\mib.bin
[2001/08/23 07:00:00 | 000,028,626 | ---- | C] () -- C:\WINDOWS\System32\perfd009.dat
[2001/08/23 07:00:00 | 000,004,463 | ---- | C] () -- C:\WINDOWS\System32\oembios.dat
[2001/08/23 07:00:00 | 000,001,804 | ---- | C] () -- C:\WINDOWS\System32\dcache.bin
[2001/08/23 07:00:00 | 000,000,741 | ---- | C] () -- C:\WINDOWS\System32\noise.dat
< End of report >
Before I forget to ask ...Would the files that are backed up on our USB flash drives be infected?
I will get some sleep now and be back with you in the morning

Thank you




 This topic is locked
This topic is locked