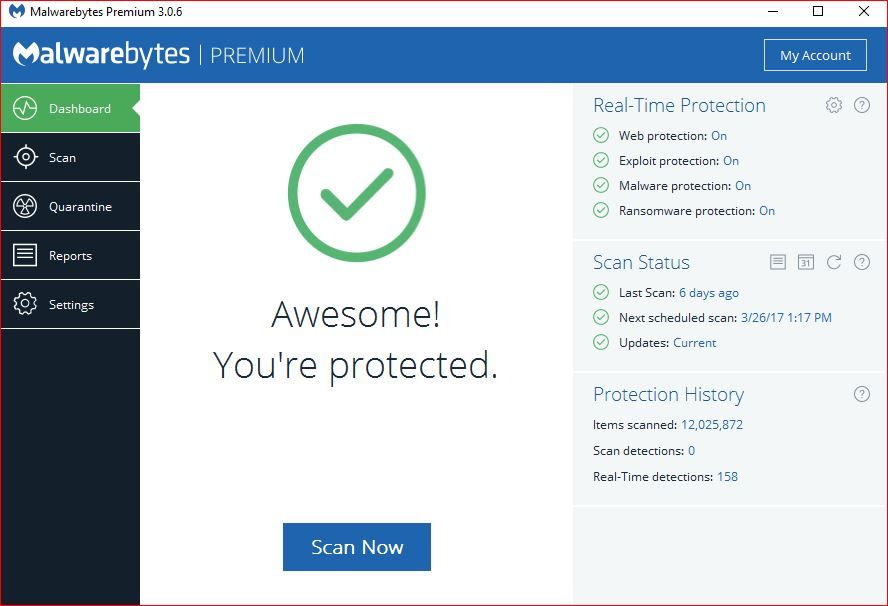
As asked for all files were opened from the desktop and as admin:
ADWCleaner -
# AdwCleaner v6.045 - Logfile created 22/04/2017 at 21:34:17
# Updated on 28/03/2017 by Malwarebytes
# Database : 2017-04-22.1 [Server]
# Operating System : Windows 10 Home (X64)
# Username : user - VIKTOR
# Running from : C:\Users\user\Downloads\AdwCleaner.exe
# Mode: Clean
***** [ Services ] *****
***** [ Folders ] *****
[-] Folder deleted: C:\users\user\AppData\Roaming\Enigma Software Group
[-] Folder deleted: C:\users\user\Documents\vShare
[-] Folder deleted: C:\Program Files\Enigma Software Group
[-] Folder deleted: C:\sh4ldr
***** [ Files ] *****
[-] File deleted: C:\Users\user\AppData\Local\Google\Chrome\User Data\Profile 1\Local Storage\hxxps_balabolka.en.softonic.com_0.localstorage
[-] File deleted: C:\Users\user\AppData\Local\Google\Chrome\User Data\Profile 1\Local Storage\hxxps_balabolka.en.softonic.com_0.localstorage-journal
[-] File deleted: C:\Users\user\AppData\Local\Google\Chrome\User Data\Profile 1\Local Storage\hxxp_funsafetab.com_0.localstorage
[-] File deleted: C:\Users\user\AppData\Local\Google\Chrome\User Data\Profile 1\Local Storage\hxxp_funsafetab.com_0.localstorage-journal
[-] File deleted: C:\Users\user\AppData\Local\Google\Chrome\User Data\Profile 1\Local Storage\hxxp_search.funsafetabsearch.com_0.localstorage
[-] File deleted: C:\Users\user\AppData\Local\Google\Chrome\User Data\Profile 1\Local Storage\hxxp_search.funsafetabsearch.com_0.localstorage-journal
[-] File deleted: C:\Users\user\AppData\Local\Google\Chrome\User Data\Profile 1\Local Storage\hxxp_www.vshare.com_0.localstorage
[-] File deleted: C:\Users\user\AppData\Local\Google\Chrome\User Data\Profile 1\Local Storage\hxxp_www.vshare.com_0.localstorage-journal
***** [ DLL ] *****
***** [ WMI ] *****
***** [ Shortcuts ] *****
***** [ Scheduled Tasks ] *****
***** [ Registry ] *****
[-] Key deleted: [x64] HKLM\SOFTWARE\Ludashi
[-] Key deleted: [x64] HKLM\SOFTWARE\EnigmaSoftwareGroup
[-] Key deleted: HKLM\SOFTWARE\Classes\AppID\OverlayIcon.DLL
***** [ Web browsers ] *****
[-] [C:\Users\user\AppData\Local\Google\Chrome\User Data\Default\Web data] [Search Provider] Deleted: search.snap.do
[-] [C:\Users\user\AppData\Local\Google\Chrome\User Data\Default\Web data] [Search Provider] Deleted: aol.com
[-] [C:\Users\user\AppData\Local\Google\Chrome\User Data\Default\Web data] [Search Provider] Deleted: ask.com
[-] [C:\Users\user\AppData\Local\Google\Chrome\User Data\Default\Web data] [Search Provider] Deleted: search.snapdo.com
*************************
:: "Tracing" keys deleted
:: Winsock settings cleared
*************************
C:\AdwCleaner\AdwCleaner[C0].txt - [2699 Bytes] - [22/04/2017 21:34:17]
C:\AdwCleaner\AdwCleaner[S0].txt - [2844 Bytes] - [22/04/2017 21:32:54]
########## EOF - C:\AdwCleaner\AdwCleaner[C0].txt - [2845 Bytes] ##########
JRT -
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Junkware Removal Tool (JRT) by Malwarebytes
Version: 8.1.3 (04.10.2017)
Operating System: Windows 10 Home x64
Ran by user (Administrator) on Sat 22/04/2017 at 21:28:05.83
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
File System: 1
Successfully deleted: C:\Users\user\AppData\Roaming\vshare (Folder)
Registry: 1
Successfully deleted: HKCU\Software\Microsoft\Windows\CurrentVersion\Run\\GoogleChromeAutoLaunch_4E874A737D5662A34EBBEADB3A9C4A09 (Registry Value)
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Scan was completed on Sat 22/04/2017 at 21:28:42.60
End of JRT log
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
MalwareBytes Test Results Summary -
Malwarebytes
www.malwarebytes.com
-Log Details-
Scan Date: 4/22/17
Scan Time: 9:41 PM
Logfile: malwarebytes test.txt
Administrator: Yes
-Software Information-
Version: 3.0.6.1469
Components Version: 1.0.103
Update Package Version: 1.0.1784
License: Free
-System Information-
OS: Windows 10
CPU: x64
File System: NTFS
User: VIKTOR\user
-Scan Summary-
Scan Type: Threat Scan
Result: Completed
Objects Scanned: 450398
Time Elapsed: 2 min, 2 sec
-Scan Options-
Memory: Enabled
Startup: Enabled
Filesystem: Enabled
Archives: Enabled
Rootkits: Disabled
Heuristics: Enabled
PUP: Enabled
PUM: Enabled
-Scan Details-
Process: 0
(No malicious items detected)
Module: 0
(No malicious items detected)
Registry Key: 0
(No malicious items detected)
Registry Value: 0
(No malicious items detected)
Registry Data: 0
(No malicious items detected)
Data Stream: 0
(No malicious items detected)
Folder: 0
(No malicious items detected)
File: 0
(No malicious items detected)
Physical Sector: 0
(No malicious items detected)
(end)
Thanks,
HypoCheese.



 This topic is locked
This topic is locked