[Resolved] A really tough problem!
#1
![[Resolved] A really tough problem!: post #1](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 14 February 2010 - 05:24 PM
Register to Remove
#2
![[Resolved] A really tough problem!: post #2](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 14 February 2010 - 06:47 PM
- Malware removal is a sometimes lengthy and tedious process. Please stick with the thread until I’ve given you the “All clear.” Absence of symptoms does not mean your machine is clean!
- Please do not run any scans or install/uninstall any applications without being directed to do so.
- Please follow my instructions carefully and in the order they are posted.
- Any underlined text in my posts indicates a clickable link.
- You should print any instruction I give you for ease of use and reference.
- If you have any questions at all, please stop and ask before proceeding.
I will post back shortly with instructions.
ASAP & UNITE Member - Proud Graduate of the WTT Classroom
The help you receive here is free. If you wish to show your appreciation, then you may [url="https://www.paypal.com/cgi-bin/webscr?cmd=_donations&business=RPMcMurphy%40whatthetech%2ecom&lc=US&item_name=RPMcMurphy¤cy_code=USD&bn=PP%2dDonationsBF%3abtn_donate_SM%2egif%3aNonHosted""]
 [/url]
[/url]
#3
![[Resolved] A really tough problem!: post #3](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 14 February 2010 - 06:52 PM
#4
![[Resolved] A really tough problem!: post #4](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 15 February 2010 - 05:12 AM
Double click DeFogger to run the tool.
- The application window will appear
- Click the Disable button to disable your CD Emulation drivers
- Click Yes to continue
- A 'Finished!' message will appear
- Click OK
- If it needs to, DeFogger may ask to reboot the machine - click OK
Do not re-enable these drivers until otherwise instructed.
Link 1
Link 2
VERY IMPORTANT !!! Save ComboFix.exe to your Desktop
* IMPORTANT - Disable your AntiVirus and AntiSpyware applications, usually via a right click on the System Tray icon. They may otherwise interfere with our tools. If you have difficulty properly disabling your protective programs, refer to this link here
- Double click on ComboFix.exe & follow the prompts.
- Follow the prompts to allow ComboFix to download and install the Microsoft Windows Recovery Console, and when prompted, agree to the End-User License Agreement to install the Microsoft Windows Recovery Console.

- Once the Microsoft Windows Recovery Console is installed using ComboFix, you should see the following message:

- Click on Yes, to continue scanning for malware.
Notes:
1. Do not mouse-click Combofix's window while it is running. That may cause it to stall.
2. Do not "re-run" Combofix. If you have a problem, reply back for further instructions.
Please include the following in your next post:
- ComboFix log
ASAP & UNITE Member - Proud Graduate of the WTT Classroom
The help you receive here is free. If you wish to show your appreciation, then you may [url="https://www.paypal.com/cgi-bin/webscr?cmd=_donations&business=RPMcMurphy%40whatthetech%2ecom&lc=US&item_name=RPMcMurphy¤cy_code=USD&bn=PP%2dDonationsBF%3abtn_donate_SM%2egif%3aNonHosted""]
 [/url]
[/url]
#5
![[Resolved] A really tough problem!: post #5](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 15 February 2010 - 12:13 PM
They should be self explanatory.
Also, I had to run a Macfee cleanup program because I did not even know I had Macafee running on my system and I could not find it in my Add/remove Programs in Control Panel.
Attached Files
#6
![[Resolved] A really tough problem!: post #6](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 15 February 2010 - 02:59 PM
 P2P - I see you have P2P software (Vuze & BitComet) installed on your machine. We are not here to pass judgment on file-sharing as a concept. However, we will warn you that engaging in this activity and having this kind of software installed on your machine will always make you more susceptible to re-infections. It likely contributed to your current situation.
P2P - I see you have P2P software (Vuze & BitComet) installed on your machine. We are not here to pass judgment on file-sharing as a concept. However, we will warn you that engaging in this activity and having this kind of software installed on your machine will always make you more susceptible to re-infections. It likely contributed to your current situation.Please note: Even if you are using a "safe" P2P program, it is only the program that is safe. You will be sharing files from uncertified sources, and these are often infected. The bad guys use P2P filesharing as a major conduit to spread their wares. I would strongly recommend that you uninstall these now. You can do so via Control Panel >> Add or Remove Programs.
If you choose to keep these applications, please do not use them until our fixes at WTT are complete.
KillAll::
SecCenter::
AV: McAfee VirusScan *On-access scanning enabled* (Updated) {84B5EE75-6421-4CDE-A33A-DD43BA9FAD83}
FW: McAfee Personal Firewall Plus *enabled* {94894B63-8C7F-4050-BDA4-813CA00DA3E8}
DDS::
Trusted Zone: buy-internetsecurity10.com
Trusted Zone: buy-is2010.com
Trusted Zone: is-software-download.com
Trusted Zone: is-software-download25.com
Trusted Zone: is10-soft-download.com
RenV::
c:\program files\Adobe\Reader 9.0\Reader\reader_sl .exe
c:\program files\Common Files\Adobe\ARM\1.0\adobearm .exe
c:\program files\Common Files\InstallShield\UpdateService\isuspm .exe
c:\program files\Creative\SBAudigy\Surround Mixer\ctsysvol .exe
c:\program files\Dell Support Center\bin\sprtcmd .exe
c:\program files\iTunes\ituneshelper .exe
c:\program files\Malwarebytes' Anti-Malware\mbamgui .exe
c:\program files\NoAds\noads .exe
c:\program files\QuickTime\qttask .exe
c:\program files\Uniblue\RegistryBooster\registrybooster .exe
c:\program files\Verizon\mccitrayapp .exe
c:\program files\Verizon\VSP\verizonservicepoint .exe
c:\program files\WinCustomize\LogonStudio\logonstudio .exe
c:\program files\Windows Defender\msascui .exe
c:\program files\Yahoo!\Common\ymailadvisor .exe
c:\program files\Yahoo!\Search Protection\searchprotection .exe
c:\windows\system32\DLA\dlactrlw .exe
Save this as CFScript to your desktop.
Then drag the CFScript into ComboFix.exe as you see in the screenshot below.

This will start ComboFix again. After reboot, (in case it asks to reboot), post the contents of Combofix.txt in your next reply.
Please include the following in your next post:
- ComboFix log
ASAP & UNITE Member - Proud Graduate of the WTT Classroom
The help you receive here is free. If you wish to show your appreciation, then you may [url="https://www.paypal.com/cgi-bin/webscr?cmd=_donations&business=RPMcMurphy%40whatthetech%2ecom&lc=US&item_name=RPMcMurphy¤cy_code=USD&bn=PP%2dDonationsBF%3abtn_donate_SM%2egif%3aNonHosted""]
 [/url]
[/url]
#7
![[Resolved] A really tough problem!: post #7](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 15 February 2010 - 05:56 PM
I understand completely. Considering my own risky behaviors got me into this situation to begin with, I would like to take this opportunity to thank you for continuing to assist me in remedying my problem!
P.S. PC is already improved and more responsive
Re: Problem
After Combo Fix ran it rebooted and ran some more then created a log, but after that it froze so I rebooted again.
Here is the log:
ComboFix 10-02-12.01 - Stephen 02/15/2010 18:09:04.2.2 - x86
Microsoft Windows XP Home Edition 5.1.2600.3.1252.1.1033.18.3070.2506 [GMT -5:00]
Running from: c:\documents and settings\Stephen\Desktop\ComboFix.exe
Command switches used :: c:\documents and settings\Stephen\Desktop\CFScript.txt
AV: avast! antivirus 4.8.1368 [VPS 100215-0] *On-access scanning disabled* (Updated) {7591DB91-41F0-48A3-B128-1A293FD8233D}
.
The following files were disabled during the run:
c:\windows\system32\APTRRNTm.dll
c:\windows\system32\APTRRNTl.dll
c:\program files\Replay Music 2\TRUserDLL.dll
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
c:\windows\Temp\tmp3.tmp
.
((((((((((((((((((((((((( Files Created from 2010-01-15 to 2010-02-15 )))))))))))))))))))))))))))))))
.
2010-02-15 21:00 . 2010-02-15 21:00 -------- d-----w- c:\documents and settings\NetworkService\Local Settings\Application Data\Apple
2010-02-15 02:52 . 2010-02-15 02:52 -------- d-----w- c:\documents and settings\Stephen\Local Settings\Application Data\Deployment
2010-02-14 23:50 . 2010-02-14 23:52 -------- dc-h--w- c:\windows\ie8
2010-02-14 02:34 . 2009-11-24 23:48 23120 ----a-w- c:\windows\system32\drivers\aswRdr.sys
2010-02-14 02:34 . 2009-11-24 23:49 48560 ----a-w- c:\windows\system32\drivers\aswTdi.sys
2010-02-14 02:34 . 2009-11-24 23:47 27408 ----a-w- c:\windows\system32\drivers\aavmker4.sys
2010-02-14 02:34 . 2009-11-24 23:47 97480 ----a-w- c:\windows\system32\AvastSS.scr
2010-02-14 02:34 . 2009-11-24 23:51 93424 ----a-w- c:\windows\system32\drivers\aswmon.sys
2010-02-14 02:34 . 2009-11-24 23:50 94160 ----a-w- c:\windows\system32\drivers\aswmon2.sys
2010-02-14 02:34 . 2009-11-24 23:50 114768 ----a-w- c:\windows\system32\drivers\aswSP.sys
2010-02-14 02:34 . 2009-11-24 23:50 20560 ----a-w- c:\windows\system32\drivers\aswFsBlk.sys
2010-02-14 02:34 . 2009-11-24 23:54 1280480 ----a-w- c:\windows\system32\aswBoot.exe
2010-02-13 02:40 . 2008-04-14 05:10 34688 ----a-w- c:\windows\system32\drivers\lbrtfdc.sys
2010-02-13 02:40 . 2008-04-14 05:10 34688 ----a-w- c:\windows\system32\dllcache\lbrtfdc.sys
2010-02-13 02:31 . 2001-08-17 18:52 18688 ----a-w- c:\windows\system32\drivers\cdaudio.sys
2010-02-13 02:31 . 2001-08-17 18:52 18688 ----a-w- c:\windows\system32\dllcache\cdaudio.sys
2010-02-13 02:31 . 2008-04-14 05:11 8192 ----a-w- c:\windows\system32\dllcache\changer.sys
2010-02-13 02:27 . 2010-02-13 02:27 -------- d-----w- c:\windows\Sun
2010-02-13 01:21 . 2010-02-13 01:21 -------- d-----w- c:\documents and settings\Stephen\Local Settings\Application Data\Threat Expert
2010-02-13 00:56 . 2010-02-13 00:56 -------- d-----w- c:\documents and settings\NetworkService\Local Settings\Application Data\Google
2010-02-12 23:59 . 2010-02-15 23:21 -------- d---a-w- c:\documents and settings\All Users\Application Data\TEMP
2010-02-08 22:52 . 2010-02-08 22:52 -------- d-----w- c:\program files\iPod
2010-02-08 22:52 . 2010-02-15 23:08 -------- d-----w- c:\program files\iTunes
2010-02-07 02:49 . 2010-02-07 02:48 59240 ----a-w- c:\windows\system32\GenSvcInst.exe
2010-02-07 02:49 . 2010-02-07 02:48 38944 ----a-w- c:\windows\system32\drivers\CDRBSDRV.SYS
2010-02-07 02:49 . 2010-02-07 02:48 139264 ----a-w- c:\windows\system32\bgsvcgen.exe
2010-02-03 02:00 . 2010-02-03 02:00 -------- d-----w- c:\documents and settings\Stephen\DesktopProblems Book
2010-01-18 01:56 . 2008-11-10 16:41 32656 ----a-w- c:\windows\system32\msonpmon.dll
2010-01-18 01:56 . 2006-10-27 00:56 33104 ----a-w- c:\windows\system32\Spool\prtprocs\w32x86\msonpppr.dll
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2024-03-21 17:44 . 2007-03-19 21:25 246272 ----a-w- c:\windows\UNINST16.EXE
2010-02-15 23:21 . 2006-10-27 17:49 -------- d-----w- c:\program files\Replay Music 2
2010-02-15 23:08 . 2009-08-25 01:32 -------- d-----w- c:\program files\Windows Defender
2010-02-15 23:08 . 2009-11-10 15:25 -------- d-----w- c:\program files\Verizon
2010-02-15 23:08 . 2009-01-27 00:40 -------- d-----w- c:\program files\Malwarebytes' Anti-Malware
2010-02-15 23:08 . 2006-12-31 04:47 -------- d-----w- c:\program files\QuickTime
2010-02-15 23:08 . 2006-08-21 23:18 -------- d-----w- c:\program files\NoAds
2010-02-15 02:56 . 2006-08-12 03:25 -------- d-----w- c:\program files\Digital Line Detect
2010-02-15 00:47 . 2007-12-09 23:14 -------- d-----w- c:\documents and settings\Stephen\Application Data\Azureus
2010-02-15 00:47 . 2007-10-18 16:07 -------- d-----w- c:\program files\PeerGuardian2
2010-02-14 23:42 . 2009-10-16 01:47 -------- d-----w- c:\program files\Windows Desktop Search
2010-02-14 22:14 . 2009-12-02 01:23 -------- d-----w- c:\program files\Spyware Doctor
2010-02-14 16:14 . 2009-12-15 16:40 -------- d-----w- c:\program files\ERUNT
2010-02-14 15:59 . 2009-07-05 04:28 -------- d-----w- c:\documents and settings\Stephen\Application Data\Apple Computer
2010-02-14 02:23 . 2007-09-03 17:49 1324 ----a-w- c:\windows\system32\d3d9caps.dat
2010-02-14 01:09 . 2006-08-21 22:51 -------- d-----w- c:\documents and settings\All Users\Application Data\Spybot - Search & Destroy
2010-02-13 04:31 . 2009-11-10 15:28 -------- d-----w- c:\program files\Common Files\Motive
2010-02-13 01:21 . 2006-08-24 02:40 -------- d-----w- c:\documents and settings\All Users\Application Data\Yahoo! Companion
2010-02-13 01:02 . 2007-02-11 04:13 -------- d-----w- c:\documents and settings\Stephen\Application Data\Yahoo!
2010-02-13 00:57 . 2009-12-30 15:46 -------- d-----w- c:\documents and settings\All Users\Application Data\Radialpoint
2010-02-13 00:48 . 2006-08-12 03:41 -------- d-----w- c:\program files\Google
2010-02-12 23:56 . 2009-11-28 22:44 -------- d-----w- c:\program files\Yamb
2010-02-12 23:21 . 2009-11-13 01:27 -------- d-----w- c:\program files\Xobni
2010-02-12 23:21 . 2007-03-04 05:30 -------- d-----w- c:\program files\Windows Live Safety Center
2010-02-12 23:19 . 2007-06-05 01:18 -------- d-----w- c:\program files\TextAloud
2010-02-12 23:17 . 2007-03-11 21:01 -------- d-----w- c:\program files\palmOne
2010-02-12 23:17 . 2009-10-13 06:21 -------- d-----w- c:\program files\Microsoft Visual Studio 8
2010-02-12 23:12 . 2009-08-31 00:38 -------- d-----w- c:\program files\Common Files\PC Tools
2010-02-12 23:00 . 2009-07-05 04:50 -------- d-----w- c:\documents and settings\Stephen\Application Data\Pegasys Inc
2010-02-12 22:59 . 2006-11-18 21:05 -------- d-----w- c:\documents and settings\Stephen\Application Data\dvdcss
2010-02-12 22:59 . 2006-08-25 01:26 -------- d-----w- c:\documents and settings\Stephen\Application Data\Creative
2010-02-12 22:59 . 2009-08-01 03:09 -------- d-----w- c:\documents and settings\Stephen\Application Data\AVS4YOU
2010-02-10 17:52 . 2009-10-13 06:20 -------- d-----w- c:\documents and settings\All Users\Application Data\Microsoft Help
2010-02-08 22:52 . 2009-09-14 21:44 -------- d-----w- c:\program files\Common Files\Apple
2010-02-08 22:40 . 2010-02-08 22:40 72488 ----a-w- c:\documents and settings\All Users\Application Data\Apple Computer\Installer Cache\iTunes 9.0.3.15\SetupAdmin.exe
2010-02-07 22:44 . 2010-02-07 22:44 -------- d-----w- c:\documents and settings\Stephen\Application Data\Total Recorder Editor Pro
2010-02-07 22:44 . 2010-02-07 22:44 -------- d-----w- c:\program files\Total Recorder Editor Pro
2010-02-07 02:48 . 2009-07-05 04:50 -------- d-----w- c:\program files\Pegasys Inc
2010-02-06 02:39 . 2008-03-01 06:03 -------- d-----w- c:\program files\Thinkwell
2010-01-25 02:38 . 2009-05-30 12:04 -------- d-----w- c:\program files\WinDjView
2010-01-20 17:19 . 2009-08-07 18:00 -------- d-----w- c:\program files\Microsoft Silverlight
2010-01-13 18:35 . 2009-02-12 02:14 5115824 ----a-w- c:\documents and settings\All Users\Application Data\Malwarebytes\Malwarebytes' Anti-Malware\mbam-setup.exe
2010-01-10 04:56 . 2010-01-10 04:56 -------- d-----w- c:\program files\Scan Tailor
2010-01-07 21:07 . 2009-01-27 00:40 38224 ----a-w- c:\windows\system32\drivers\mbamswissarmy.sys
2010-01-07 21:07 . 2009-01-27 00:40 19160 ----a-w- c:\windows\system32\drivers\mbam.sys
2009-12-31 16:50 . 2006-08-12 03:03 353792 ----a-w- c:\windows\system32\drivers\srv.sys
2009-12-30 15:47 . 2009-12-30 15:47 -------- d-----w- c:\documents and settings\Stephen\Application Data\Verizon
2009-12-30 15:46 . 2009-12-30 15:46 -------- d-----w- c:\documents and settings\All Users\Application Data\Verizon
2009-12-27 00:13 . 2007-02-27 01:58 -------- d-----w- c:\program files\TurboTax
2009-12-26 19:34 . 2009-12-26 19:34 68432 ---ha-w- c:\windows\system32\mlfcache.dat
2009-12-23 17:36 . 2007-12-09 23:12 -------- d-----w- c:\program files\Azureus
2009-12-21 19:14 . 2004-08-10 16:51 916480 ----a-w- c:\windows\system32\wininet.dll
2009-12-16 18:43 . 2004-08-10 17:01 343040 ----a-w- c:\windows\system32\mspaint.exe
2009-12-14 07:08 . 2004-08-10 16:50 33280 ----a-w- c:\windows\system32\csrsrv.dll
2009-12-11 17:53 . 2009-12-11 17:53 7 ----a-w- c:\windows\sbacknt.bin
2009-12-11 17:52 . 2009-12-11 17:52 152904 ----a-w- c:\windows\system32\vghd.scr
2009-12-08 19:26 . 2004-08-10 16:51 2145280 ----a-w- c:\windows\system32\ntoskrnl.exe
2009-12-08 18:43 . 2004-08-04 02:59 2023936 ----a-w- c:\windows\system32\ntkrnlpa.exe
2009-12-04 18:22 . 2006-08-12 03:03 455424 ----a-w- c:\windows\system32\drivers\mrxsmb.sys
2009-11-27 17:11 . 2004-08-10 16:51 1291776 ----a-w- c:\windows\system32\quartz.dll
2009-11-27 17:11 . 2004-08-04 04:56 17920 ----a-w- c:\windows\system32\msyuv.dll
2009-11-27 16:07 . 2004-08-10 16:51 28672 ----a-w- c:\windows\system32\msvidc32.dll
2009-11-27 16:07 . 2001-08-18 02:36 8704 ----a-w- c:\windows\system32\tsbyuv.dll
2009-11-27 16:07 . 2004-08-10 16:51 11264 ----a-w- c:\windows\system32\msrle32.dll
2009-11-27 16:07 . 2004-08-10 16:50 84992 ----a-w- c:\windows\system32\avifil32.dll
2009-11-27 16:07 . 2004-08-04 04:56 48128 ----a-w- c:\windows\system32\iyuv_32.dll
2009-11-21 15:51 . 2004-08-10 16:50 471552 ----a-w- c:\windows\AppPatch\aclayers.dll
2004-03-01 17:25 . 2006-08-27 00:33 114688 ----a-w- c:\program files\internet explorer\plugins\ChimeShim.dll
2009-06-19 19:09 . 2009-06-19 19:09 0 --sh--w- c:\windows\S4A97AEBB.tmp
2006-08-23 16:42 . 2006-08-23 16:42 88 --sha-r- c:\windows\system32\8FAF4E4293.sys
2007-12-27 17:34 . 2007-12-27 17:34 8 --sha-r- c:\windows\system32\9BFCCDF554.sys
2008-03-03 23:35 . 2007-12-27 17:34 2828 --sha-w- c:\windows\system32\KGyGaAvL.sys
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"ctfmon.exe"="c:\windows\system32\ctfmon.exe" [2008-04-14 15360]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"Kernel and Hardware Abstraction Layer"="KHALMNPR.EXE" [2007-04-11 56080]
"avast!"="c:\progra~1\ALWILS~1\Avast4\ashDisp.exe" [2009-11-24 81000]
"iTunesHelper"="c:\program files\iTunes\iTunesHelper.exe" [2010-01-23 141608]
"dellsupportcenter"="c:\program files\Dell Support Center\bin\sprtcmd.exe" [2009-05-21 206064]
c:\documents and settings\Stephen\Start Menu\Programs\Startup\
ERUNT AutoBackup.lnk - c:\program files\ERUNT\AUTOBACK.EXE [2005-10-20 38912]
MemTurbo.lnk - c:\program files\Memturbo 4\MemTurbo.exe [2008-8-3 2314752]
OneNote 2007 Screen Clipper and Launcher.lnk - c:\program files\Microsoft Office\Office12\ONENOTEM.EXE [2008-10-25 98696]
c:\documents and settings\All Users\Start Menu\Programs\Startup\
Digital Line Detect.lnk - c:\program files\Digital Line Detect\DLG.exe [2006-8-11 24576]
[HKEY_LOCAL_MACHINE\software\microsoft\windows nt\currentversion\winlogon]
"UIHost"="c:\windows\system32\logonuiX.exe"
[HKEY_LOCAL_MACHINE\software\microsoft\windows nt\currentversion\winlogon\notify\LBTWlgn]
2008-05-02 06:42 72208 ----a-w- c:\program files\Common Files\Logitech\Bluetooth\LBTWLgn.dll
[HKEY_LOCAL_MACHINE\software\microsoft\windows nt\currentversion\drivers32]
"wave"=APTRRNTm.dll
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\aawservice]
@="Service"
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\WdfLoadGroup]
@=""
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\WinDefend]
@="Service"
[HKLM\~\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^Digital Line Detect.lnk]
backup=c:\windows\pss\Digital Line Detect.lnkCommon Startup
[HKLM\~\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^Google Updater.lnk]
backup=c:\windows\pss\Google Updater.lnkCommon Startup
[HKLM\~\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^HotSync Manager.lnk]
backup=c:\windows\pss\HotSync Manager.lnkCommon Startup
[HKLM\~\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^HOTSYNCSHORTCUTNAME.lnk]
backup=c:\windows\pss\HOTSYNCSHORTCUTNAME.lnkCommon Startup
[HKLM\~\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^Logitech SetPoint.lnk]
backup=c:\windows\pss\Logitech SetPoint.lnkCommon Startup
[HKLM\~\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^Microsoft Office.lnk]
backup=c:\windows\pss\Microsoft Office.lnkCommon Startup
[HKLM\~\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^ymetray.lnk]
backup=c:\windows\pss\ymetray.lnkCommon Startup
[HKLM\~\startupfolder\C:^Documents and Settings^Stephen^Start Menu^Programs^Startup^GameSpot Download Manager.lnk]
backup=c:\windows\pss\GameSpot Download Manager.lnkStartup
[HKLM\~\startupfolder\C:^Documents and Settings^Stephen^Start Menu^Programs^Startup^MagicDisc.lnk]
backup=c:\windows\pss\MagicDisc.lnkStartup
[HKLM\~\startupfolder\C:^Documents and Settings^Stephen^Start Menu^Programs^Startup^palmOne Registration.lnk]
backup=c:\windows\pss\palmOne Registration.lnkStartup
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\Acrobat Assistant 8.0]
2009-12-18 07:38 624056 ----a-w- c:\program files\Adobe\Acrobat 8.0\Acrobat\acrotray.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\Adobe ARM]
2009-12-11 20:57 948672 ----a-r- c:\program files\Common Files\Adobe\ARM\1.0\adobearm.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\Adobe Reader Speed Launcher]
2009-12-22 06:57 35760 ----a-w- c:\program files\Adobe\Reader 9.0\Reader\reader_sl.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\AppleSyncNotifier]
2009-08-13 19:51 177440 ----a-w- c:\program files\Common Files\Apple\Mobile Device Support\bin\AppleSyncNotifier.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\Creative Detector]
2004-12-02 22:23 102400 ------w- c:\program files\Creative\MediaSource\Detector\CTDetect.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\ctfmon.exe]
2008-04-14 00:12 15360 ------w- c:\windows\system32\ctfmon.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\dscactivate]
2007-11-15 14:24 16384 ----a-w- c:\program files\Dell Support Center\gs_agent\custom\dsca.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\NeroFilterCheck]
2007-03-01 20:57 153136 ----a-w- c:\program files\Common Files\Ahead\Lib\NeroCheck.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\RegistryMechanic]
2008-07-08 20:41 2828184 ----a-w- c:\program files\Registry Mechanic\RegMech.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\SetDefaultMIDI]
2004-12-22 21:40 24576 ----a-w- c:\windows\MIDIDEF.EXE
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\TkBellExe]
2009-10-24 20:25 198160 ----a-w- c:\program files\Common Files\Real\Update_OB\realsched.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\UniblueSpeedUpMyPC]
2009-04-28 12:05 614696 ----a-w- c:\program files\Uniblue\SpeedUpMyPC\Launcher.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\Yahoo! Pager]
2005-08-15 19:32 3092480 ----a-w- c:\program files\Yahoo!\Messenger\YPager.exe
[HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\services]
"IDriverT"=3 (0x3)
"gusvc"=2 (0x2)
"FLEXnet Licensing Service"=3 (0x3)
"Bonjour Service"=2 (0x2)
"WMPNetworkSvc"=3 (0x3)
"WinDefend"=2 (0x2)
"sdCoreService"=3 (0x3)
"NMIndexingService"=3 (0x3)
"NBService"=3 (0x3)
"Creative Service for CDROM Access"=2 (0x2)
"Creative Labs Licensing Service"=3 (0x3)
"Cepstral License Server"=2 (0x2)
"avast! Web Scanner"=3 (0x3)
"avast! Mail Scanner"=3 (0x3)
"avast! Antivirus"=2 (0x2)
"Ati HotKey Poller"=2 (0x2)
"aswUpdSv"=2 (0x2)
"Adobe LM Service"=3 (0x3)
"TuneUp.ProgramStatisticsSvc"=2 (0x2)
"TuneUp.Defrag"=3 (0x3)
"IntuitUpdateService"=2 (0x2)
"aawservice"=2 (0x2)
[HKEY_CURRENT_USER\software\microsoft\windows\currentversion\run-]
"BgMonitor_{79662E04-7C6C-4d9f-84C7-88D8A56B10AA}"="c:\program files\Common Files\Ahead\Lib\NMBgMonitor.exe"
"ctfmon.exe"=c:\windows\system32\ctfmon.exe
[HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\run-]
"DMXLauncher"=c:\program files\Dell\Media Experience\DMXLauncher.exe
"dscactivate"="c:\program files\Dell Support Center\gs_agent\custom\dsca.exe"
"ECenter"="c:\dell\E-Center\gtb.exe"
"SigmatelSysTrayApp"=stsystra.exe
"SunJavaUpdateSched"="c:\program files\Java\jre1.6.0_03\bin\jusched.exe"
"TkBellExe"="c:\program files\Common Files\Real\Update_OB\realsched.exe" -osboot
"UpdReg"=c:\windows\UpdReg.EXE
"USBToolTip"="c:\program files\Pinnacle\Shared Files\Programs\USBTip\USBTip.exe"
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile]
"DisableNotifications"= 1 (0x1)
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"%windir%\\system32\\sessmgr.exe"=
"%windir%\\Network Diagnostic\\xpnetdiag.exe"=
"c:\\Program Files\\Yahoo!\\Messenger\\YPager.exe"=
"c:\\Program Files\\Yahoo!\\Messenger\\YServer.exe"=
"c:\\PROGRA~1\\Yahoo!\\MESSEN~1\\YPager.exe"= c:\\Program Files\\Yahoo!\\Messenger\\YPager.exe
"c:\\PROGRA~1\\Yahoo!\\MESSEN~1\\Yserver.exe"= c:\\Program Files\\Yahoo!\\Messenger\\YServer.exe
"c:\\Program Files\\Yahoo!\\Yahoo! Music Engine\\YahooMusicEngine.exe"=
"c:\\Program Files\\Java\\jre1.5.0_06\\bin\\javaw.exe"=
"c:\\BentleyPubs\\eBahn\\jre\\1.3.1\\bin\\javaw.exe"=
"c:\\Program Files\\Common Files\\Ahead\\Nero Web\\SetupX.exe"=
"c:\\Program Files\\Nero\\Nero 7\\Nero ShowTime\\ShowTime.exe"=
"c:\\Program Files\\palmOne\\Hotsync.exe"=
"c:\\Program Files\\VideoLAN\\VLC\\vlc.exe"=
"c:\\Program Files\\Azureus\\Azureus.exe"=
"c:\\Program Files\\NextUp-Acapela\\bin\\acatel_srv.exe"=
"c:\\Documents and Settings\\All Users\\Application Data\\Kaspersky Lab Setup Files\\Kaspersky Internet Security 2009\\English\\setup.exe"=
"c:\\Program Files\\Real\\RealPlayer\\realplay.exe"=
"c:\\Program Files\\Ubisoft\\Chessmaster Grandmaster Edition\\game.exe"=
"c:\\Program Files\\Rosetta Stone\\Rosetta Stone Version 3\\support\\bin\\win\\RosettaStoneLtdServices.exe"=
"c:\\Program Files\\Rosetta Stone\\Rosetta Stone Version 3\\RosettaStoneVersion3.exe"=
"c:\\Program Files\\Bonjour\\mDNSResponder.exe"=
"c:\\Program Files\\Verizon\\VSP\\ServicepointService.exe"=
"c:\\Program Files\\Microsoft Office\\Office12\\ONENOTE.EXE"=
"c:\\Program Files\\iTunes\\iTunes.exe"=
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\GloballyOpenPorts\List]
"3389:TCP"= 3389:TCP:@xpsp2res.dll,-22009
"7619:TCP"= 7619:TCP:BitComet 7619 TCP
"7619:UDP"= 7619:UDP:BitComet 7619 UDP
"16252:TCP"= 16252:TCP:BitComet 16252 TCP
"16252:UDP"= 16252:UDP:BitComet 16252 UDP
"4000:TCP"= 4000:TCP:Important
"4001:TCP"= 4001:TCP:Important
"4002:TCP"= 4002:TCP:Important
"4003:TCP"= 4003:TCP:Important
"4004:TCP"= 4004:TCP:Important
"4005:TCP"= 4005:TCP:Important
R0 PCTCore;PCTools KDS;c:\windows\system32\drivers\PCTCore.sys [12/1/2009 8:23 PM 207792]
R1 aswSP;avast! Self Protection;c:\windows\system32\drivers\aswSP.sys [2/13/2010 9:34 PM 114768]
R2 aswFsBlk;aswFsBlk;c:\windows\system32\drivers\aswFsBlk.sys [2/13/2010 9:34 PM 20560]
R2 Browser Defender Update Service;Browser Defender Update Service;c:\program files\Spyware Doctor\BDT\BDTUpdateService.exe [12/1/2009 8:23 PM 112592]
R2 MBAMService;MBAMService;c:\program files\Malwarebytes' Anti-Malware\mbamservice.exe [1/26/2009 7:40 PM 236368]
R2 ServicepointService;ServicepointService;c:\program files\Verizon\VSP\ServicepointService.exe [12/30/2009 10:46 AM 668912]
R2 XobniService;XobniService;c:\program files\Xobni\XobniService.exe [10/12/2009 11:33 AM 46824]
R3 MBAMProtector;MBAMProtector;c:\windows\system32\drivers\mbam.sys [1/26/2009 7:40 PM 19160]
S0 Lbd;Lbd;c:\windows\system32\DRIVERS\Lbd.sys --> c:\windows\system32\DRIVERS\Lbd.sys [?]
S2 gupdate1c9ccf99ba708a;Google Update Service (gupdate1c9ccf99ba708a);c:\program files\Google\Update\GoogleUpdate.exe [5/4/2009 3:43 PM 133104]
S3 sdAuxService;PC Tools Auxiliary Service;c:\program files\Spyware Doctor\pctsAuxs.exe [12/1/2009 8:23 PM 359624]
S4 ASKService;ASKService;c:\program files\AskBarDis\bar\bin\AskService.exe [11/12/2009 8:25 PM 464264]
S4 ASKUpgrade;ASKUpgrade;c:\program files\AskBarDis\bar\bin\ASKUpgrade.exe [11/12/2009 8:26 PM 234888]
S4 Cepstral License Server;Cepstral License Server;c:\program files\Cepstral\bin\CepstralLicSrv.exe [3/15/2007 12:54 PM 57344]
S4 sptd;sptd;c:\windows\system32\drivers\sptd.sys [12/11/2006 6:37 PM 646392]
S4 WinDefend;Windows Defender;c:\program files\Windows Defender\MsMpEng.exe [11/3/2006 6:19 PM 13592]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost - NetSvcs
UxTuneUp
.
Contents of the 'Scheduled Tasks' folder
2010-02-15 c:\windows\Tasks\1-Click Maintenance.job
- c:\program files\TuneUp Utilities 2009\OneClickStarter.exe [2009-07-16 08:54]
2010-02-15 c:\windows\Tasks\AppleSoftwareUpdate.job
- c:\program files\Apple Software Update\SoftwareUpdate.exe [2007-08-29 16:34]
2010-02-15 c:\windows\Tasks\AWC AutoSweep.job
- c:\program files\IObit\Advanced SystemCare 3\AutoSweep.exe [2009-06-21 19:35]
2010-02-15 c:\windows\Tasks\GoogleUpdateTaskMachineCore.job
- c:\program files\Google\Update\GoogleUpdate.exe [2009-05-04 20:43]
2010-02-15 c:\windows\Tasks\GoogleUpdateTaskMachineUA.job
- c:\program files\Google\Update\GoogleUpdate.exe [2009-05-04 20:43]
2010-02-15 c:\windows\Tasks\Malwarebytes' Scheduled Scan for Stephen.job
- c:\program files\Malwarebytes' Anti-Malware\mbam.exe [2009-01-27 21:07]
2010-02-15 c:\windows\Tasks\Malwarebytes' Scheduled Update for Stephen.job
- c:\program files\Malwarebytes' Anti-Malware\mbam.exe [2009-01-27 21:07]
.
.
------- Supplementary Scan -------
.
uStart Page = hxxp://wapp.verizon.net/bookmarks/bmredir.asp?region=all&bw=fiber&cd=7.0yahoo&bm=yh_home
uInternet Settings,ProxyOverride = <local>;*.local
uSearchURL,(Default) = hxxp://us.rd.yahoo.com/customize/ycomp/defaults/su/*http://www.yahoo.com
IE: &Highlight - c:\windows\WEB\highlight.htm
IE: &Links List - c:\windows\WEB\urllist.htm
IE: Append to existing PDF - c:\program files\Adobe\Acrobat 8.0\Acrobat\AcroIEFavClient.dll/AcroIEAppend.html
IE: Convert link target to Adobe PDF - c:\program files\Adobe\Acrobat 8.0\Acrobat\AcroIEFavClient.dll/AcroIECapture.html
IE: Convert link target to existing PDF - c:\program files\Adobe\Acrobat 8.0\Acrobat\AcroIEFavClient.dll/AcroIEAppend.html
IE: Convert selected links to Adobe PDF - c:\program files\Adobe\Acrobat 8.0\Acrobat\AcroIEFavClient.dll/AcroIECaptureSelLinks.html
IE: Convert selected links to existing PDF - c:\program files\Adobe\Acrobat 8.0\Acrobat\AcroIEFavClient.dll/AcroIEAppendSelLinks.html
IE: Convert selection to Adobe PDF - c:\program files\Adobe\Acrobat 8.0\Acrobat\AcroIEFavClient.dll/AcroIECapture.html
IE: Convert selection to existing PDF - c:\program files\Adobe\Acrobat 8.0\Acrobat\AcroIEFavClient.dll/AcroIEAppend.html
IE: Convert to Adobe PDF - c:\program files\Adobe\Acrobat 8.0\Acrobat\AcroIEFavClient.dll/AcroIECapture.html
IE: E&xport to Microsoft Excel - c:\progra~1\MICROS~4\Office12\EXCEL.EXE/3000
IE: I&mages List - c:\windows\Web\imglist.htm
IE: Open Frame in &New Window - c:\windows\WEB\frm2new.htm
IE: Zoom &In - c:\windows\WEB\zoomin.htm
IE: Zoom O&ut - c:\windows\WEB\zoomout.htm
Trusted Zone: intuit.com\ttlc
Trusted Zone: musicmatch.com\online
DPF: {E6BB2089-163F-466B-812A-748096614DFD} - hxxp://cainternetsecurity.net/scanner/cascanner.cab
.
**************************************************************************
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2010-02-15 18:27
Windows 5.1.2600 Service Pack 3 NTFS
scanning hidden processes ...
scanning hidden autostart entries ...
scanning hidden files ...
scan completed successfully
hidden files: 0
**************************************************************************
"ImagePath"="\??\c:\windows\system32\drivers\rootrepeal
[1].sys"
[HKEY_LOCAL_MACHINE\System\ControlSet006\Services\rootrepeal[1]]
"ImagePath"="\??\c:\windows\system32\drivers\rootrepeal
.
--------------------- DLLs Loaded Under Running Processes ---------------------
- - - - - - - > 'winlogon.exe'(1168)
c:\windows\system32\Ati2evxx.dll
c:\program files\common files\logitech\bluetooth\LBTWlgn.dll
c:\program files\common files\logitech\bluetooth\LBTServ.dll
- - - - - - - > 'Explorer.EXE'(4016)
c:\windows\system32\WININET.dll
c:\windows\system32\ieframe.dll
c:\windows\system32\mshtml.dll
c:\windows\system32\msls31.dll
c:\windows\WinSxS\x86_Microsoft.VC80.CRT_1fc8b3b9a1e18e3b_8.0.50727.4053_x-ww_e6967989\MSVCR80.dll
c:\windows\system32\webcheck.dll
c:\windows\system32\WPDShServiceObj.dll
c:\windows\system32\PortableDeviceTypes.dll
c:\windows\system32\PortableDeviceApi.dll
c:\program files\Memturbo 4\cpurocket.dll
.
------------------------ Other Running Processes ------------------------
.
c:\program files\Alwil Software\Avast4\aswUpdSv.exe
c:\program files\Alwil Software\Avast4\ashServ.exe
c:\program files\Common Files\Apple\Mobile Device Support\bin\AppleMobileDeviceService.exe
c:\windows\system32\bgsvcgen.exe
c:\program files\Google\Update\1.2.183.13\GoogleCrashHandler.exe
c:\program files\Common Files\Motive\McciCMService.exe
c:\program files\Dell Support Center\bin\sprtsvc.exe
c:\program files\Alcohol Soft\Alcohol 120\StarWind\StarWindService.exe
c:\windows\system32\MsPMSPSv.exe
c:\program files\Yahoo!\SoftwareUpdate\YahooAUService.exe
c:\program files\Alwil Software\Avast4\ashMaiSv.exe
c:\program files\Alwil Software\Avast4\ashWebSv.exe
c:\program files\Dell Support Center\gs_agent\dsc.exe
c:\program files\iPod\bin\iPodService.exe
.
**************************************************************************
.
Completion time: 2010-02-15 18:37:07 - machine was rebooted
ComboFix-quarantined-files.txt 2010-02-15 23:37
ComboFix2.txt 2010-02-15 17:34
ComboFix3.txt 2009-06-19 19:21
Pre-Run: 42,330,460,160 bytes free
Post-Run: 42,283,683,840 bytes free
Current=6 Default=6 Failed=5 LastKnownGood=7 Sets=1,2,3,4,5,6,7
- - End Of File - - A758FE9B613D3C42C8EA950B70D5A3B8
#8
![[Resolved] A really tough problem!: post #8](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 16 February 2010 - 04:11 AM
Good work! It looks like we are making progress.
Open MBAM
- Click the Update tab
- Click Check for Updates
- If an update is found, it will download and install the latest version.
- The program will close to update and reopen.
- Once the program has loaded, select "Perform Full Scan", then click Scan.
- The scan may take some time to finish,so please be patient.
- When the scan is complete, click OK, then Show Results to view the results.
- Make sure that everything is checked, and click Remove Selected.
- When disinfection is completed, a log will open in Notepad and you may be prompted to Restart.(See Extra Note)
- The log is automatically saved by MBAM and can be viewed by clicking the Logs tab in MBAM.
- Copy&Paste the entire report in your next reply.
If MBAM encounters a file that is difficult to remove,you will be presented with 1 of 2 prompts,click OK to either and let MBAM proceed with the disinfection process,if asked to restart the computer,please do so immediatly.
1. Click Accept, when prompted to download and install the program files and database of malware definitions.
2. To optimize scanning time and produce a more sensible report for review:
- Close any open programs
- Turn off the real time scanner of any existing antivirus program while performing the online scan. Click HERE to see how to disable the most common antivirus programs.
The program will then begin downloading and installing and will also update the database.
Please be patient as this can take quite a long time to download.
- Once the update is complete, click on Settings.
- Make sure these boxes are checked (ticked). If they are not, please tick them and click on the Save button:
- Spyware, adware, dialers, and other riskware
- Archives
- E-mail databases
- Click on My Computer under the green Scan bar to the left to start the scan.
- Once the scan is complete, it will display if your system has been infected. It does not provide an option to clean/disinfect. We only require a report from it.
- Do NOT be alarmed by what you see in the report. Many of the finds have likely been quarantined.
- Click View report... at the bottom.
- Click the Save report... button.

- Change the Files of type dropdown box to Text file (.txt) and name the file KasReport.txt to save the file to your desktop so that you may post it in your next reply
- MBAM log
- Kaspersky log
- Any outstanding issues or symptoms with your PC
ASAP & UNITE Member - Proud Graduate of the WTT Classroom
The help you receive here is free. If you wish to show your appreciation, then you may [url="https://www.paypal.com/cgi-bin/webscr?cmd=_donations&business=RPMcMurphy%40whatthetech%2ecom&lc=US&item_name=RPMcMurphy¤cy_code=USD&bn=PP%2dDonationsBF%3abtn_donate_SM%2egif%3aNonHosted""]
 [/url]
[/url]
#9
![[Resolved] A really tough problem!: post #9](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 17 February 2010 - 09:44 AM
Malwarebytes found a boat load and froze in the middle of scan. Here's the log:
Malwarebytes' Anti-Malware 1.44
Database version: 3746
Windows 5.1.2600 Service Pack 3
Internet Explorer 8.0.6001.18702
2/16/2010 8:10:11 PM
mbam-log-2010-02-16 (20-10-11).txt
Scan type: Full Scan (C:\|E:\|)
Objects scanned: 445842
Time elapsed: 3 hour(s), 37 minute(s), 50 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 0
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 21
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
C:\Program Files\Movkit\Movkit Batch Video Converter\MovKitVC.exe (Malware.Packer.Morphine) -> Quarantined and deleted successfully.
C:\Program Files\Pegasys Inc\TMPGEnc 4.0 XPress\keygen.exe (Malware.Packer.Gen) -> Quarantined and deleted successfully.
C:\System Volume Information\_restore{202550A8-7A33-4BCA-9586-051D24DDBF8F}\RP187\A0057601.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\System Volume Information\_restore{202550A8-7A33-4BCA-9586-051D24DDBF8F}\RP187\A0057619.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\System Volume Information\_restore{202550A8-7A33-4BCA-9586-051D24DDBF8F}\RP187\A0057679.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\System Volume Information\_restore{202550A8-7A33-4BCA-9586-051D24DDBF8F}\RP187\A0057680.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\System Volume Information\_restore{202550A8-7A33-4BCA-9586-051D24DDBF8F}\RP187\A0057681.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\System Volume Information\_restore{202550A8-7A33-4BCA-9586-051D24DDBF8F}\RP187\A0057682.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\System Volume Information\_restore{202550A8-7A33-4BCA-9586-051D24DDBF8F}\RP187\A0057683.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\System Volume Information\_restore{202550A8-7A33-4BCA-9586-051D24DDBF8F}\RP187\A0057684.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\System Volume Information\_restore{202550A8-7A33-4BCA-9586-051D24DDBF8F}\RP187\A0057685.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\System Volume Information\_restore{202550A8-7A33-4BCA-9586-051D24DDBF8F}\RP187\A0057686.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\System Volume Information\_restore{202550A8-7A33-4BCA-9586-051D24DDBF8F}\RP187\A0057687.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\System Volume Information\_restore{202550A8-7A33-4BCA-9586-051D24DDBF8F}\RP187\A0057688.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\System Volume Information\_restore{202550A8-7A33-4BCA-9586-051D24DDBF8F}\RP187\A0057689.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\System Volume Information\_restore{202550A8-7A33-4BCA-9586-051D24DDBF8F}\RP187\A0057690.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\System Volume Information\_restore{202550A8-7A33-4BCA-9586-051D24DDBF8F}\RP187\A0057691.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\System Volume Information\_restore{202550A8-7A33-4BCA-9586-051D24DDBF8F}\RP187\A0057703.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\System Volume Information\_restore{202550A8-7A33-4BCA-9586-051D24DDBF8F}\RP187\A0060712.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\System Volume Information\_restore{202550A8-7A33-4BCA-9586-051D24DDBF8F}\RP187\A0060713.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
E:\My documents\Azureus Downloads\Recover Keys 3.0.0.33 Portable\Recover Keys 3.0.0.33 Portable.exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
Manually unistalled these programs:
Movkit Batch Video Converter
TMPGEnc 4.0 XPress
Recover Keys 3.0.0.33 Portable
Also, I had malwarebytes remove this stuff from quarantine.
Kaspersky started up but never finished the scan went to blue screen saying scan was interuppted by mbamswissarmy.sys
Page fault in nonpaged area.
Do you want me to redo these two steps again?
Don't know if this will help you, but here is the scan I did in safe mode with Malewarebytes immediately after all this stuff occurred to my PC:
Malwarebytes' Anti-Malware 1.44
Database version: 3718
Windows 5.1.2600 Service Pack 3 (Safe Mode)
Internet Explorer 8.0.6001.18702
2/12/2010 10:31:02 PM
mbam-log-2010-02-12 (22-31-02).txt
Scan type: Quick Scan
Objects scanned: 123917
Time elapsed: 7 minute(s), 53 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 13
Registry Values Infected: 1
Registry Data Items Infected: 3
Folders Infected: 0
Files Infected: 21
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\jukebox3 (Rootkit.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\lhidfilt (Rootkit.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\lmoufilt (Rootkit.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\palmusbd (Rootkit.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\secdrv (Rootkit.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\ser2pl (Rootkit.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\sfng32 (Rootkit.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\sigfilt (Rootkit.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\sntnlusb (Rootkit.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\usbaapl (Rootkit.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\wdf01000 (Rootkit.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\wudfpf (Rootkit.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\wudfrd (Rootkit.Agent) -> Quarantined and deleted successfully.
Registry Values Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\dla (Malware.Packer.Gen) -> Quarantined and deleted successfully.
Registry Data Items Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\AntiVirusDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\FirewallDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\UpdatesDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
Folders Infected:
(No malicious items detected)
Files Infected:
C:\WINDOWS\system32\DLA\dlactrlw.exe (Malware.Packer.Gen) -> Quarantined and deleted successfully.
C:\Program Files\Internet Explorer\js.mui (Malware.Packer.Gen) -> Quarantined and deleted successfully.
C:\Program Files\Internet Explorer\wmpscfgs.exe (Malware.Packer.Gen) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\smss32 .exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\drivers\ctpdusb.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\drivers\lhidfilt.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\drivers\lmoufilt.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\drivers\palmusbd.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\drivers\secdrv.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\drivers\ser2pl.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\drivers\sfng32.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\drivers\sigfilt.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\drivers\sntnlusb.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\drivers\usbaapl.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\drivers\wdf01000.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\drivers\wudfpf.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\drivers\wudfrd.sys (Rootkit.Agent) -> Quarantined and deleted successfully.
C:\Documents and Settings\Stephen\Local Settings\Application Data\av.exe (ROGUE.Win7Antispyware2010) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\helper32.dll (Trojan.FakeAlert) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\41.exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\IS15.exe (Trojan.FakeAlert) -> Quarantined and deleted successfully.
Edited by quirmche, 17 February 2010 - 09:52 AM.
#10
![[Resolved] A really tough problem!: post #10](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 17 February 2010 - 01:25 PM
Thanks for manually deleting those cracks and keygens. We don't support software piracy on this forum and having those on your system is very risky!
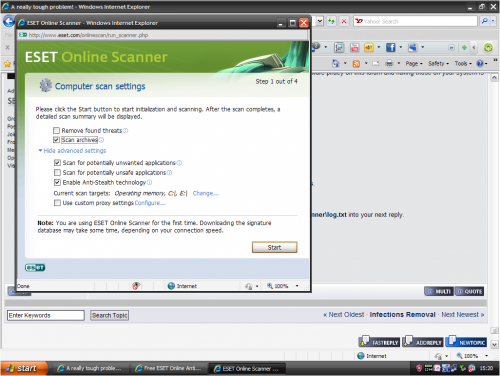
Let's try this online scan instead of Kaspersky:
- Place a check mark in the box YES, I accept the Terms Of Use
- Click the Start button.
- Now click the Install button.
- Click Start. The scanner engine will initialize and update.
- Do Not place a check mark in the box beside Remove found threats.
- Click the Scan button. The scan will now run, please be patient.
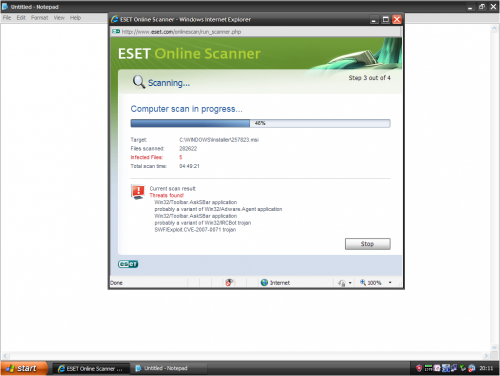
- When the scan finishes click the Details tab.
- Copy and paste the contents of the C:\ProgramFiles\EsetOnlineScanner\log.txt into your next reply.
- ESET log
- Any outstanding issues or symptoms with your PC
ASAP & UNITE Member - Proud Graduate of the WTT Classroom
The help you receive here is free. If you wish to show your appreciation, then you may [url="https://www.paypal.com/cgi-bin/webscr?cmd=_donations&business=RPMcMurphy%40whatthetech%2ecom&lc=US&item_name=RPMcMurphy¤cy_code=USD&bn=PP%2dDonationsBF%3abtn_donate_SM%2egif%3aNonHosted""]
 [/url]
[/url]
Register to Remove
#12
![[Resolved] A really tough problem!: post #12](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 17 February 2010 - 02:27 PM
ASAP & UNITE Member - Proud Graduate of the WTT Classroom
The help you receive here is free. If you wish to show your appreciation, then you may [url="https://www.paypal.com/cgi-bin/webscr?cmd=_donations&business=RPMcMurphy%40whatthetech%2ecom&lc=US&item_name=RPMcMurphy¤cy_code=USD&bn=PP%2dDonationsBF%3abtn_donate_SM%2egif%3aNonHosted""]
 [/url]
[/url]
#13
![[Resolved] A really tough problem!: post #13](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 17 February 2010 - 02:32 PM
#15
![[Resolved] A really tough problem!: post #15](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 17 February 2010 - 07:18 PM
ASAP & UNITE Member - Proud Graduate of the WTT Classroom
The help you receive here is free. If you wish to show your appreciation, then you may [url="https://www.paypal.com/cgi-bin/webscr?cmd=_donations&business=RPMcMurphy%40whatthetech%2ecom&lc=US&item_name=RPMcMurphy¤cy_code=USD&bn=PP%2dDonationsBF%3abtn_donate_SM%2egif%3aNonHosted""]
 [/url]
[/url]
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users



 This topic is locked
This topic is locked