[Resolved] pc Running very slowly
#1
![[Resolved] pc Running very slowly: post #1](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 16 November 2009 - 10:02 PM
Register to Remove
#2
![[Resolved] pc Running very slowly: post #2](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 16 November 2009 - 10:31 PM
#3
![[Resolved] pc Running very slowly: post #3](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 16 November 2009 - 10:31 PM
#4
![[Resolved] pc Running very slowly: post #4](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 24 November 2009 - 11:56 AM
My name is Tomk. I would be glad to take a look at your log and help you with solving any malware problems. Logs can take a while to research, so please be patient and I'd be grateful if you would note the following:
- I will be working on your Malware issues, this may or may not, solve other issues you have with your machine.
- The fixes are specific to your problem and should only be used for the issues on this machine.
- Please continue to review my answers until I tell you your machine appears to be clear. Absence of symptoms does not mean that everything is clear.
- It's often worth reading through these instructions and printing them for ease of reference.
- If you don't know or understand something, please don't hesitate to say or ask!! It's better to be sure and safe than sorry.
- Please reply to this thread. Do not start a new topic.
- Download DDS and save it to your desktop from
- Here
- here or
- here.
- Disable any script blocking protection (How to Disable your Security Programs)
- Double click DDS icon to run the tool (may take up to 3 minutes to run)
- When done, DDS.txt will open.
- After a few moments, attach.txt will open in a second window.
- Save both reports to your desktop.
- We Need to check for Rootkits with RootRepeal
- Download RootRepeal from one of the following locations and save it to your desktop.
- Open
 on your desktop.
on your desktop. - Click the
 tab.
tab. - Click the
 button.
button. - In the Select Scan dialog, check
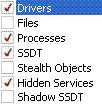
- Push Ok
- Check the box for your main system drive (Usually C:), and press Ok.
- Allow RootRepeal to run a scan of your system. This may take some time.
- Once the scan completes, push the
 button. Save the log to your desktop, using a distinctive name, such as RootRepeal.txt.
button. Save the log to your desktop, using a distinctive name, such as RootRepeal.txt.
- Download RootRepeal from one of the following locations and save it to your desktop.
- Copy/paste the log (that you've previously saved to your desktop) from RootRepeal onto your post.
- Copy/paste the DDS.txt log (that you've previously saved to your desktop) onto your post.
- Attach the Attach.txt report to your post by scroling down to the Attachments area and then clicking Browse. Browse to where you saved the file, and click Open and then click UPLOAD.
------------------------------------------------------------
Microsoft MVP 2010-2014
#5
![[Resolved] pc Running very slowly: post #5](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 24 November 2009 - 02:02 PM
Attached Files
#6
![[Resolved] pc Running very slowly: post #6](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 24 November 2009 - 02:07 PM
Not much showing. Let's try a couple more scans.
Download Rooter.exe to your desktop
- Then doubleclick it to start the tool
- A Notepad file containing the report will open, also found at %systemdrive%\Rooter.txt. Post that here
Please go to Kaspersky website and perform an online antivirus scan.
- Read through the requirements and privacy statement and click on Accept button.
- It will start downloading and installing the scanner and virus definitions. You will be prompted to install an application from Kaspersky. Click Run.
- When the downloads have finished, click on Settings.
- Make sure these boxes are checked (ticked). If they are not, please tick them and click on the Save button:
- Spyware, Adware, Dialers, and other potentially dangerous programs
Archives
Mail databases
- Spyware, Adware, Dialers, and other potentially dangerous programs
- Click on My Computer under Scan.
- Once the scan is complete, it will display the results. Click on View Scan Report.
- You will see a list of infected items there. Click on Save Report As....
- Save this report to a convenient place. Change the Files of type to Text file (.txt) before clicking on the Save button.
- Please post this log in your next reply.
------------------------------------------------------------
Microsoft MVP 2010-2014
#7
![[Resolved] pc Running very slowly: post #7](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 24 November 2009 - 07:47 PM
#8
![[Resolved] pc Running very slowly: post #8](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 24 November 2009 - 07:51 PM
------------------------------------------------------------
Microsoft MVP 2010-2014
#9
![[Resolved] pc Running very slowly: post #9](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 26 November 2009 - 07:05 AM
#10
![[Resolved] pc Running very slowly: post #10](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 26 November 2009 - 10:06 AM
Let's try this...
Download ComboFix from one of these locations:
Link 1
Link 2
Link 3
* IMPORTANT !!! Save ComboFix.exe to your Desktop
- Disable your AntiVirus and AntiSpyware applications, usually via a right click on the System Tray icon. They may otherwise interfere with our tools. If you have difficulty properly disabling your protective programs, refer to this link --> http://forums.whatth...ams_t96260.html
- Double click on ComboFix.exe & follow the prompts.
- As part of it's process, ComboFix will check to see if the Microsoft Windows Recovery Console is installed. With malware infections being as they are today, it's strongly recommended to have this pre-installed on your machine before doing any malware removal. It will allow you to boot up into a special recovery/repair mode that will allow us to more easily help you should your computer have a problem after an attempted removal of malware.
- Follow the prompts to allow ComboFix to download and install the Microsoft Windows Recovery Console, and when prompted, agree to the End-User License Agreement to install the Microsoft Windows Recovery Console.
**Please note: If the Microsoft Windows Recovery Console is already installed, ComboFix will continue it's malware removal procedures.

Once the Microsoft Windows Recovery Console is installed using ComboFix, you should see the following message:

Click on Yes, to continue scanning for malware.
When finished, it shall produce a log for you. Please include the C:\ComboFix.txt in your next reply.
Notes:
1. Do not mouse-click Combofix's window while it is running. That may cause it to stall.
2. Do not "re-run" Combofix. If you have a problem, reply back for further instructions.
3. ComboFix may reset a number of Internet Explorer's settings, including making I-E the default browser.
4. Combofix prevents autorun of ALL CD, floppy and USB devices to assist with malware removal & increase security. If this is an issue or makes it difficult for you -- please tell your helper.
5. CF disconnects your machine from the internet. The connection is automatically restored before CF completes its run. If CF runs into difficulty and terminates prematurely, the connection can be manually restored by restarting your machine.
------------------------------------------------------------
Microsoft MVP 2010-2014
Register to Remove
#11
![[Resolved] pc Running very slowly: post #11](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 26 November 2009 - 09:39 PM
Here is the result of the combofix scan:
ComboFix 09-11-26.02 - Alain 11/26/2009 20:20.3.2 - x86
Microsoft Windows XP Home Edition 5.1.2600.3.1252.1.1033.18.447.227 [GMT -7:00]
Running from: c:\documents and settings\Alain\Desktop\ComboFix.exe
.
((((((((((((((((((((((((( Files Created from 2009-10-27 to 2009-11-27 )))))))))))))))))))))))))))))))
.
2009-11-25 03:22 . 2009-11-25 13:10 -------- d-----w- c:\documents and settings\All Users\Application Data\Kaspersky Lab
2009-11-24 20:12 . 2009-11-24 20:12 -------- d-----w- C:\Rooter$
2009-11-23 23:09 . 2009-11-24 01:19 -------- d-----w- c:\documents and settings\All Users\Application Data\SITEguard
2009-11-23 23:08 . 2009-11-23 23:08 -------- d-----w- c:\program files\Common Files\iS3
2009-11-23 15:38 . 2009-11-23 15:38 93360 ----a-w- c:\windows\system32\drivers\SBREDrv.sys
2009-11-18 17:40 . 2009-11-18 17:41 -------- d-----w- c:\program files\LimeWire
2009-11-12 19:46 . 2009-11-12 19:48 -------- d-----w- C:\e0ca4154876d7715d3
2009-11-04 16:54 . 2009-11-04 16:54 152576 ----a-w- c:\documents and settings\Alain\Application Data\Sun\Java\jre1.6.0_17\lzma.dll
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2009-11-26 13:13 . 2006-06-07 05:29 -------- d-----w- c:\program files\Spybot - Search & Destroy
2009-11-26 13:11 . 2006-06-07 05:29 -------- d-----w- c:\documents and settings\All Users\Application Data\Spybot - Search & Destroy
2009-11-24 20:12 . 2007-01-12 00:02 664 ----a-w- c:\windows\system32\d3d9caps.dat
2009-11-24 01:26 . 2006-06-26 16:39 -------- d-----w- c:\program files\STOPzilla!
2009-11-23 23:41 . 2009-11-23 23:40 5936 ----a-w- c:\windows\system32\drivers\kgpcpy.cfg
2009-11-23 23:23 . 2006-06-26 16:39 -------- d-----w- c:\documents and settings\All Users\Application Data\STOPzilla!
2009-11-23 23:06 . 2008-04-08 15:00 -------- d---a-w- c:\documents and settings\All Users\Application Data\TEMP
2009-11-23 22:20 . 2008-10-01 05:14 -------- d-----w- c:\program files\ERUNT
2009-11-23 22:01 . 2006-09-17 22:44 -------- d-----w- c:\program files\Lavasoft
2009-11-23 22:00 . 2008-02-11 04:52 -------- d-----w- c:\documents and settings\All Users\Application Data\Lavasoft
2009-11-04 16:56 . 2006-09-19 02:28 -------- d-----w- c:\program files\Java
2009-10-27 16:38 . 2008-10-03 16:00 -------- d-----w- c:\program files\Malwarebytes' Anti-Malware
2009-10-27 16:36 . 2008-10-03 16:01 4045527 ----a-w- c:\documents and settings\All Users\Application Data\Malwarebytes\Malwarebytes' Anti-Malware\mbam-setup.exe
2009-10-22 22:03 . 2009-10-22 22:03 26 ----a-w- c:\windows\winstart.bat
2009-10-22 22:03 . 2009-10-22 22:03 123 ----a-w- c:\windows\tmpcpyis.bat
2009-10-22 22:03 . 2009-10-22 22:03 122 ----a-w- c:\windows\tmpdelis.bat
2009-10-22 19:41 . 2009-10-22 19:41 -------- d-----w- c:\program files\PowerISO
2009-10-14 14:22 . 2004-08-21 01:32 -------- d-----w- c:\program files\Common Files\Adobe
2009-10-12 02:43 . 2006-06-07 00:48 28296 ----a-w- c:\documents and settings\Alain\Local Settings\Application Data\GDIPFONTCACHEV1.DAT
2009-10-11 11:17 . 2009-01-08 17:18 411368 ----a-w- c:\windows\system32\deploytk.dll
2009-09-11 14:18 . 2004-08-21 00:47 136192 ----a-w- c:\windows\system32\msv1_0.dll
2009-09-10 20:54 . 2008-10-03 16:00 38224 ----a-w- c:\windows\system32\drivers\mbamswissarmy.sys
2009-09-10 20:53 . 2008-10-03 16:00 19160 ----a-w- c:\windows\system32\drivers\mbam.sys
2009-09-04 21:03 . 2004-08-21 00:47 58880 ----a-w- c:\windows\system32\msasn1.dll
2009-08-29 08:08 . 2004-08-21 00:47 916480 ----a-w- c:\windows\system32\wininet.dll
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"SpybotSD TeaTimer"="c:\program files\Spybot - Search & Destroy\TeaTimer.exe" [2009-03-05 2260480]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"CeEKEY"="c:\program files\TOSHIBA\E-KEY\CeEKey.exe" [2004-06-14 638976]
"CeEPOWER"="c:\program files\TOSHIBA\Power Management\CePMTray.exe" [2004-08-20 135168]
"Apoint"="c:\program files\Apoint2K\Apoint.exe" [2003-10-30 192512]
"TPNF"="c:\program files\TOSHIBA\TouchPad\TPTray.exe" [2004-03-15 53248]
"dla"="c:\windows\system32\dla\tfswctrl.exe" [2004-04-21 118843]
"Adobe Reader Speed Launcher"="c:\program files\Adobe\Reader 8.0\Reader\Reader_sl.exe" [2009-10-03 39792]
"Adobe ARM"="c:\program files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" [2009-09-04 935288]
"AGRSMMSG"="AGRSMMSG.exe" - c:\windows\agrsmmsg.exe [2004-02-20 88363]
c:\documents and settings\Alain\Start Menu\Programs\Startup\
Microsoft Office OneNote 2003 Quick Launch.lnk - c:\program files\Microsoft Office\OFFICE11\ONENOTEM.EXE [2007-4-19 64864]
c:\documents and settings\All Users\Start Menu\Programs\Startup\
RAMASST.lnk - c:\windows\system32\RAMASST.exe [2004-8-20 155648]
[HKLM\~\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^HP Digital Imaging Monitor.lnk]
path=c:\documents and settings\All Users\Start Menu\Programs\Startup\HP Digital Imaging Monitor.lnk
backup=c:\windows\pss\HP Digital Imaging Monitor.lnkCommon Startup
HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\HP Software Update
HKEY_LOCAL_MACHINE\software\microsoft\shared tools\msconfig\startupreg\SunJavaUpdateSched
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"%windir%\\system32\\sessmgr.exe"=
"c:\\WINDOWS\\system32\\fxsclnt.exe"=
"%windir%\\Network Diagnostic\\xpnetdiag.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqtra08.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqste08.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpofxm08.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hposfx08.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hposid01.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqscnvw.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqkygrp.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqCopy.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpfccopy.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpzwiz01.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\Unload\\HpqPhUnl.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\Unload\\HpqDIA.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpoews01.exe"=
"c:\\StubInstaller.exe"=
"c:\\WINDOWS\\system32\\mmc.exe"=
"c:\\Program Files\\BitTornado\\btdownloadgui.exe"=
S3 Roxio UPnP Renderer 11;Roxio UPnP Renderer 11;"c:\program files\Roxio Creator 2009\Digital Home 11\RoxioUPnPRenderer11.exe" --> c:\program files\Roxio Creator 2009\Digital Home 11\RoxioUPnPRenderer11.exe [?]
.
Contents of the 'Scheduled Tasks' folder
2009-10-20 c:\windows\Tasks\Disk Cleanup.job
- c:\windows\system32\cleanmgr.exe [2004-08-21 00:12]
2007-02-23 c:\windows\Tasks\Spybot - Search & Destroy - Scheduled Task.job
- c:\program files\Spybot - Search & Destroy\SpybotSD.exe [2009-01-31 22:31]
.
.
------- Supplementary Scan -------
.
uStart Page = hxxp://www.mytelus.com/
IE: Add to Google Photos Screensa&ver - c:\windows\system32\GPhotos.scr/200
IE: E&xport to Microsoft Excel - c:\progra~1\MICROS~2\OFFICE11\EXCEL.EXE/3000
DPF: {D9CDEFE3-51BB-4737-A12C-53D9814A148C} - hxxps://my.calgaryhealthregion.ca/redirect/http://exCAS1a.crha-health.ab.ca/owa/MWScripts/AttachView/1.5/DAX.cab
.
- - - - ORPHANS REMOVED - - - -
Toolbar-SITEguard - (no file)
MSConfigStartUp-CTFMON - (no file)
AddRemove-{2FCE4FC5-6930-40E7-A4F1-F862207424EF} - c:\program files\InstallShield Installation Information\{2FCE4FC5-6930-40E7-A4F1-F862207424EF}\setup.exe REMOVEALL
AddRemove-{91810AFC-A4F8-4EBA-A5AA-B198BBC81144} - c:\program files\InstallShield Installation Information\{91810AFC-A4F8-4EBA-A5AA-B198BBC81144}\setup.exe REMOVEALL
**************************************************************************
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2009-11-26 20:30
Windows 5.1.2600 Service Pack 3 NTFS
scanning hidden processes ...
scanning hidden autostart entries ...
scanning hidden files ...
scan completed successfully
hidden files: 0
**************************************************************************
.
--------------------- LOCKED REGISTRY KEYS ---------------------
[HKEY_USERS\S-1-5-21-2688664847-4137593175-816191208-1006\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved\{81B79AEB-7465-1339-8968-CCB1E1E78026}*]
@Allowed: (Read) (RestrictedCode)
@Allowed: (Read) (RestrictedCode)
"ialfkanghpldckgabi"=hex:6a,61,6c,61,65,70,6a,62,69,6e,65,68,61,6f,69,6a,65,66,
6b,61,00,00
"hajgeimfgncjcfob"=hex:6a,61,6f,61,64,70,63,6e,63,6f,64,70,70,6e,65,61,63,6c,
6f,66,00,23
.
--------------------- DLLs Loaded Under Running Processes ---------------------
- - - - - - - > 'explorer.exe'(3288)
c:\windows\system32\WININET.dll
c:\windows\system32\ieframe.dll
c:\windows\system32\webcheck.dll
c:\windows\system32\WPDShServiceObj.dll
c:\windows\system32\PortableDeviceTypes.dll
c:\windows\system32\PortableDeviceApi.dll
c:\program files\Common Files\Adobe\Acrobat\ActiveX\AcroIEHelper.dll
c:\windows\WinSxS\x86_Microsoft.VC80.CRT_1fc8b3b9a1e18e3b_8.0.50727.3053_x-ww_b80fa8ca\MSVCR80.dll
c:\progra~1\SPYBOT~1\SDHelper.dll
c:\windows\system32\dla\tfswshx.dll
c:\windows\system32\tfswapi.dll
c:\windows\system32\dla\tfswcres.dll
.
Completion time: 2009-11-26 20:33
ComboFix-quarantined-files.txt 2009-11-27 03:33
ComboFix2.txt 2008-10-07 15:38
ComboFix3.txt 2008-10-05 19:46
Pre-Run: 21,653,463,040 bytes free
Post-Run: 21,629,247,488 bytes free
- - End Of File - - 7D18E86DA2E35C591BA1ED65B1CCC6ED
Let me know how this is... Thanks...
#12
![[Resolved] pc Running very slowly: post #12](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 26 November 2009 - 10:28 PM
COMBOFIX-Script
- Please open Notepad (Start -> Run -> type notepad in the Open field -> OK) and copy and paste the text present inside the code box below:
regnull:: [HKEY_USERS\S-1-5-21-2688664847-4137593175-816191208-1006\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved\{81B79AEB-7465-1339-8968-CCB1E1E78026}*] - Save this as CFScript.txt and change the "Save as type" to "All Files" and place it on your desktop.

- Very Important! Temporarily disable your anti-virus, script blocking and any anti-malware real-time protection before following the steps below. They can interfere with ComboFix or remove some of its embedded files which may cause "unpredictable results".
- Referring to the screenshot above, drag CFScript.txt into ComboFix.exe.
- ComboFix will now run a scan on your system. It may reboot your system when it finishes. This is normal.
- When finished, it shall produce a log for you. Copy and paste the contents of the log in your next reply.
I would further suggest that you also read this tutorial on slow running computers
and Help! My computer is slow! by miekiemoes.
Then let me know how things are running.
------------------------------------------------------------
Microsoft MVP 2010-2014
#13
![[Resolved] pc Running very slowly: post #13](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 26 November 2009 - 11:21 PM
Here is the newest Combofix log: (I'll read through the recommended links)
ComboFix 09-11-26.02 - Alain 11/26/2009 21:58.4.2 - x86
Microsoft Windows XP Home Edition 5.1.2600.3.1252.1.1033.18.447.206 [GMT -7:00]
Running from: c:\documents and settings\Alain\Desktop\ComboFix.exe
Command switches used :: c:\documents and settings\Alain\Desktop\CFScript.txt
.
((((((((((((((((((((((((( Files Created from 2009-10-27 to 2009-11-27 )))))))))))))))))))))))))))))))
.
2009-11-25 03:22 . 2009-11-25 13:10 -------- d-----w- c:\documents and settings\All Users\Application Data\Kaspersky Lab
2009-11-24 20:12 . 2009-11-24 20:12 -------- d-----w- C:\Rooter$
2009-11-23 23:09 . 2009-11-24 01:19 -------- d-----w- c:\documents and settings\All Users\Application Data\SITEguard
2009-11-23 23:08 . 2009-11-23 23:08 -------- d-----w- c:\program files\Common Files\iS3
2009-11-23 15:38 . 2009-11-23 15:38 93360 ----a-w- c:\windows\system32\drivers\SBREDrv.sys
2009-11-18 17:40 . 2009-11-18 17:41 -------- d-----w- c:\program files\LimeWire
2009-11-12 19:46 . 2009-11-12 19:48 -------- d-----w- C:\e0ca4154876d7715d3
2009-11-04 16:54 . 2009-11-04 16:54 152576 ----a-w- c:\documents and settings\Alain\Application Data\Sun\Java\jre1.6.0_17\lzma.dll
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2009-11-26 13:13 . 2006-06-07 05:29 -------- d-----w- c:\program files\Spybot - Search & Destroy
2009-11-26 13:11 . 2006-06-07 05:29 -------- d-----w- c:\documents and settings\All Users\Application Data\Spybot - Search & Destroy
2009-11-24 20:12 . 2007-01-12 00:02 664 ----a-w- c:\windows\system32\d3d9caps.dat
2009-11-24 01:26 . 2006-06-26 16:39 -------- d-----w- c:\program files\STOPzilla!
2009-11-23 23:41 . 2009-11-23 23:40 5936 ----a-w- c:\windows\system32\drivers\kgpcpy.cfg
2009-11-23 23:23 . 2006-06-26 16:39 -------- d-----w- c:\documents and settings\All Users\Application Data\STOPzilla!
2009-11-23 23:06 . 2008-04-08 15:00 -------- d---a-w- c:\documents and settings\All Users\Application Data\TEMP
2009-11-23 22:20 . 2008-10-01 05:14 -------- d-----w- c:\program files\ERUNT
2009-11-23 22:01 . 2006-09-17 22:44 -------- d-----w- c:\program files\Lavasoft
2009-11-23 22:00 . 2008-02-11 04:52 -------- d-----w- c:\documents and settings\All Users\Application Data\Lavasoft
2009-11-04 16:56 . 2006-09-19 02:28 -------- d-----w- c:\program files\Java
2009-10-27 16:38 . 2008-10-03 16:00 -------- d-----w- c:\program files\Malwarebytes' Anti-Malware
2009-10-27 16:36 . 2008-10-03 16:01 4045527 ----a-w- c:\documents and settings\All Users\Application Data\Malwarebytes\Malwarebytes' Anti-Malware\mbam-setup.exe
2009-10-22 22:03 . 2009-10-22 22:03 26 ----a-w- c:\windows\winstart.bat
2009-10-22 22:03 . 2009-10-22 22:03 123 ----a-w- c:\windows\tmpcpyis.bat
2009-10-22 22:03 . 2009-10-22 22:03 122 ----a-w- c:\windows\tmpdelis.bat
2009-10-22 19:41 . 2009-10-22 19:41 -------- d-----w- c:\program files\PowerISO
2009-10-14 14:22 . 2004-08-21 01:32 -------- d-----w- c:\program files\Common Files\Adobe
2009-10-12 02:43 . 2006-06-07 00:48 28296 ----a-w- c:\documents and settings\Alain\Local Settings\Application Data\GDIPFONTCACHEV1.DAT
2009-10-11 11:17 . 2009-01-08 17:18 411368 ----a-w- c:\windows\system32\deploytk.dll
2009-09-11 14:18 . 2004-08-21 00:47 136192 ----a-w- c:\windows\system32\msv1_0.dll
2009-09-10 20:54 . 2008-10-03 16:00 38224 ----a-w- c:\windows\system32\drivers\mbamswissarmy.sys
2009-09-10 20:53 . 2008-10-03 16:00 19160 ----a-w- c:\windows\system32\drivers\mbam.sys
2009-09-04 21:03 . 2004-08-21 00:47 58880 ----a-w- c:\windows\system32\msasn1.dll
2009-08-29 08:08 . 2004-08-21 00:47 916480 ------w- c:\windows\system32\wininet.dll
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"SpybotSD TeaTimer"="c:\program files\Spybot - Search & Destroy\TeaTimer.exe" [2009-03-05 2260480]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"CeEKEY"="c:\program files\TOSHIBA\E-KEY\CeEKey.exe" [2004-06-14 638976]
"CeEPOWER"="c:\program files\TOSHIBA\Power Management\CePMTray.exe" [2004-08-20 135168]
"Apoint"="c:\program files\Apoint2K\Apoint.exe" [2003-10-30 192512]
"TPNF"="c:\program files\TOSHIBA\TouchPad\TPTray.exe" [2004-03-15 53248]
"dla"="c:\windows\system32\dla\tfswctrl.exe" [2004-04-21 118843]
"Adobe Reader Speed Launcher"="c:\program files\Adobe\Reader 8.0\Reader\Reader_sl.exe" [2009-10-03 39792]
"Adobe ARM"="c:\program files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" [2009-09-04 935288]
"AGRSMMSG"="AGRSMMSG.exe" - c:\windows\agrsmmsg.exe [2004-02-20 88363]
c:\documents and settings\Alain\Start Menu\Programs\Startup\
Microsoft Office OneNote 2003 Quick Launch.lnk - c:\program files\Microsoft Office\OFFICE11\ONENOTEM.EXE [2007-4-19 64864]
c:\documents and settings\All Users\Start Menu\Programs\Startup\
RAMASST.lnk - c:\windows\system32\RAMASST.exe [2004-8-20 155648]
[HKLM\~\startupfolder\C:^Documents and Settings^All Users^Start Menu^Programs^Startup^HP Digital Imaging Monitor.lnk]
path=c:\documents and settings\All Users\Start Menu\Programs\Startup\HP Digital Imaging Monitor.lnk
backup=c:\windows\pss\HP Digital Imaging Monitor.lnkCommon Startup
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"%windir%\\system32\\sessmgr.exe"=
"c:\\WINDOWS\\system32\\fxsclnt.exe"=
"%windir%\\Network Diagnostic\\xpnetdiag.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqtra08.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqste08.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpofxm08.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hposfx08.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hposid01.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqscnvw.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqkygrp.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqCopy.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpfccopy.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpzwiz01.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\Unload\\HpqPhUnl.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\Unload\\HpqDIA.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpoews01.exe"=
"c:\\StubInstaller.exe"=
"c:\\WINDOWS\\system32\\mmc.exe"=
"c:\\Program Files\\BitTornado\\btdownloadgui.exe"=
S3 Roxio UPnP Renderer 11;Roxio UPnP Renderer 11;"c:\program files\Roxio Creator 2009\Digital Home 11\RoxioUPnPRenderer11.exe" --> c:\program files\Roxio Creator 2009\Digital Home 11\RoxioUPnPRenderer11.exe [?]
.
Contents of the 'Scheduled Tasks' folder
2009-10-20 c:\windows\Tasks\Disk Cleanup.job
- c:\windows\system32\cleanmgr.exe [2004-08-21 00:12]
2007-02-23 c:\windows\Tasks\Spybot - Search & Destroy - Scheduled Task.job
- c:\program files\Spybot - Search & Destroy\SpybotSD.exe [2009-01-31 22:31]
.
.
------- Supplementary Scan -------
.
uStart Page = hxxp://www.mytelus.com/
IE: Add to Google Photos Screensa&ver - c:\windows\system32\GPhotos.scr/200
IE: E&xport to Microsoft Excel - c:\progra~1\MICROS~2\OFFICE11\EXCEL.EXE/3000
DPF: {D9CDEFE3-51BB-4737-A12C-53D9814A148C} - hxxps://my.calgaryhealthregion.ca/redirect/http://exCAS1a.crha-health.ab.ca/owa/MWScripts/AttachView/1.5/DAX.cab
.
**************************************************************************
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2009-11-26 22:06
Windows 5.1.2600 Service Pack 3 NTFS
scanning hidden processes ...
scanning hidden autostart entries ...
scanning hidden files ...
scan completed successfully
hidden files: 0
**************************************************************************
.
--------------------- DLLs Loaded Under Running Processes ---------------------
- - - - - - - > 'explorer.exe'(3300)
c:\windows\system32\WININET.dll
c:\windows\system32\ieframe.dll
c:\windows\system32\webcheck.dll
c:\windows\system32\WPDShServiceObj.dll
c:\windows\system32\PortableDeviceTypes.dll
c:\windows\system32\PortableDeviceApi.dll
.
Completion time: 2009-11-26 22:09
ComboFix-quarantined-files.txt 2009-11-27 05:08
ComboFix2.txt 2009-11-27 03:33
ComboFix3.txt 2008-10-07 15:38
ComboFix4.txt 2008-10-05 19:46
Pre-Run: 21,636,190,208 bytes free
Post-Run: 21,624,688,640 bytes free
- - End Of File - - BC3A0D5C5B6D290379480A6DC3CC3650
#14
![[Resolved] pc Running very slowly: post #14](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 27 November 2009 - 06:31 AM
#15
![[Resolved] pc Running very slowly: post #15](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 27 November 2009 - 08:51 AM
All we did is clean up some remnants that may or may not have been left by malware. Most were references to files that no longer exist but there was one entry that was corrupted whether by accident or a virus I don't know.
I don't see anything more to mess with so...
Log looks good
Time for some housekeeping
- Click START then RUN
- Now type ComboFix /Uninstall in the runbox and click OK.
- Note the space between the X and the U, it needs to be there.
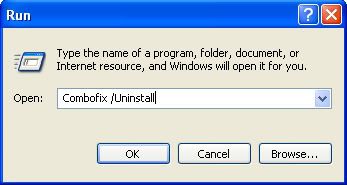
- Implement some cleanup procedures.
- Reset System Restore.
Please re-enable any security that was disabled.
The following is my standard advice for the future. Use what you can and pat yourself on the back for what you're already doing.
Please take time to read Preventing Malware - Tools and Practices for Safe Computing. Very important information for your consideration is contained therein.
I would also suggest you read this:
So how did I get infected in the first place?
by Tony Klein
Also: "How to prevent malware"
by miekiemoes
Please respond back that you understand the above and let me know if you have any questions. Otherwise, this thread will be closed Resolved.
------------------------------------------------------------
Microsoft MVP 2010-2014
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users



 This topic is locked
This topic is locked



