[Resolved] Virus on my computer
#1
![[Resolved] Virus on my computer: post #1](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 06 November 2009 - 02:53 PM
Register to Remove
#2
![[Resolved] Virus on my computer: post #2](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 08 November 2009 - 07:16 AM
Please download RootRepeal from one of these locations and save it to your desktop
Here
Here
Here
- Open
 on your desktop.
on your desktop. - Click the
 tab.
tab. - Click the
 button.
button. - Check just these boxes:
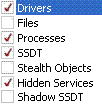
- Push Ok
- Check the box for your main system drive (Usually C:, and press Ok.
- Allow RootRepeal to run a scan of your system. This may take some time.
- Once the scan completes, push the
 button. Save the log to your desktop, using a distinctive name, such as RootRepeal.txt. Include this report in your post.
button. Save the log to your desktop, using a distinctive name, such as RootRepeal.txt. Include this report in your post.
Next
- Download random's system information tool (RSIT) by random/random from here and save it to your desktop.
- Double click on RSIT.exe to run RSIT.
- Click Continue at the disclaimer screen.
- Once it has finished, two logs will open. Please post the contents of both log.txt (<<will be maximized) and info.txt (<<will be minimized)
The forum is staffed by volunteers who donate their time and expertise.
If you feel you have been helped, please consider a donation.

Find us on Facebook
Please LIKE and SHARE
Just a reminder that threads will be closed if no reply in 3 days.
#3
![[Resolved] Virus on my computer: post #3](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 08 November 2009 - 09:56 AM
#4
![[Resolved] Virus on my computer: post #4](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 08 November 2009 - 11:49 AM

Download GMER Rootkit Scanner from here or here.
- Extract the contents of the zipped file to desktop.
- Double click GMER.exe. If asked to allow gmer.sys driver to load, please consent .
- If it gives you a warning about rootkit activity and asks if you want to run scan...click on NO.

Click the image to enlarge it
- In the right panel, you will see several boxes that have been checked. Uncheck the following ...
- Sections
- IAT/EAT
- Drives/Partition other than Systemdrive (typically C:\)
- Show All (don't miss this one)
- Then click the Scan button & wait for it to finish.
- Once done click on the [Save..] button, and in the File name area, type in "Gmer.txt" or it will save as a .log file which cannot be uploaded to your post.
- Save it where you can easily find it, such as your desktop, and post it in your next reply.
Please download Rooter Rootkit Detector to your Desktop
- Doubleclick it to start the tool.
- A Notepad file containing the report will open, also found at %systemdrive% (usually C:\Rooter.txt.
- Post the report for me to see.
The forum is staffed by volunteers who donate their time and expertise.
If you feel you have been helped, please consider a donation.

Find us on Facebook
Please LIKE and SHARE
Just a reminder that threads will be closed if no reply in 3 days.
#5
![[Resolved] Virus on my computer: post #5](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 08 November 2009 - 05:36 PM
txtGMER 1.0.15.15163 - http://www.gmer.net
Rootkit scan 2009-11-08 15:45:45
Windows 5.1.2600 Service Pack 3
Running: gmer.exe; Driver: C:\DOCUME~1\YM\LOCALS~1\Temp\pxtdrpob.sys
---- System - GMER 1.0.15 ----
SSDT spom.sys ZwCreateKey [0xF72870E0]
SSDT spom.sys ZwEnumerateKey [0xF72A5CA2]
SSDT spom.sys ZwEnumerateValueKey [0xF72A6030]
SSDT spom.sys ZwOpenKey [0xF72870C0]
SSDT spom.sys ZwQueryKey [0xF72A6108]
SSDT spom.sys ZwQueryValueKey [0xF72A5F88]
SSDT spom.sys ZwSetValueKey [0xF72A619A]
SSDT \??\C:\Program Files\SUPERAntiSpyware\SASKUTIL.sys (SASKUTIL.SYS/SUPERAdBlocker.com and SUPERAntiSpyware.com) ZwTerminateProcess [0xED71E0B0]
INT 0x62 ? 863D8BF8
INT 0x83 ? 86449BF8
INT 0xB4 ? 86327F00
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwCreateFile [0xED66078A]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwCreateProcess [0xED660738]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwCreateProcessEx [0xED66074C]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwDeleteKey [0xED66083B]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwDeleteValueKey [0xED660867]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwMapViewOfSection [0xED6607CA]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwNotifyChangeKey [0xED660901]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwOpenProcess [0xED660710]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwOpenThread [0xED660724]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwProtectVirtualMemory [0xED66079E]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwQueryMultipleValueKey [0xED6608A9]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwRenameKey [0xED660851]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwReplaceKey [0xED660929]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwRestoreKey [0xED660915]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwSetContextThread [0xED660776]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwSetInformationProcess [0xED660762]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwTerminateProcess [0xED6607F9]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwUnloadKey [0xED6608EB]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwUnmapViewOfSection [0xED6607E0]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) ZwYieldExecution [0xED6607B4]
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) NtCreateFile
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) NtMapViewOfSection
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) NtOpenProcess
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) NtOpenThread
Code \SystemRoot\system32\drivers\mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.) NtSetInformationProcess
---- Devices - GMER 1.0.15 ----
Device \FileSystem\Ntfs \Ntfs 864481F8
AttachedDevice \FileSystem\Ntfs \Ntfs mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
Device \FileSystem\Fastfat \FatCdrom 8616D1F8
Device \Driver\sptd \Device\3033018400 spom.sys
AttachedDevice \Driver\Tcpip \Device\Ip Mpfp.sys (McAfee Personal Firewall Plus Driver/McAfee, Inc.)
AttachedDevice \Driver\Kbdclass \Device\KeyboardClass0 SynTP.sys (Synaptics Touchpad Driver/Synaptics, Inc.)
AttachedDevice \Driver\Kbdclass \Device\KeyboardClass0 eabfiltr.sys (QLB PS/2 Keyboard filter driver/Hewlett-Packard Development Company, L.P.)
Device \Driver\usbohci \Device\USBPDO-0 862951F8
Device \Driver\dmio \Device\DmControl\DmIoDaemon 8644A1F8
Device \Driver\dmio \Device\DmControl\DmConfig 8644A1F8
Device \Driver\dmio \Device\DmControl\DmPnP 8644A1F8
Device \Driver\dmio \Device\DmControl\DmInfo 8644A1F8
Device \Driver\usbehci \Device\USBPDO-1 862961F8
Device \Driver\PCI_PNP0900 \Device\00000061 spom.sys
AttachedDevice \Driver\Tcpip \Device\Tcp Mpfp.sys (McAfee Personal Firewall Plus Driver/McAfee, Inc.)
Device \Driver\Ftdisk \Device\HarddiskVolume1 863D91F8
Device \Driver\Ftdisk \Device\HarddiskVolume2 863D91F8
Device \Driver\Cdrom \Device\CdRom0 862FE1F8
Device \Driver\Cdrom \Device\CdRom1 862FE1F8
Device \Driver\atapi \Device\Ide\IdeDeviceP0T0L0-3 [F71BDB40] atapi.sys[unknown section] {MOV EDX, [ESP+0x8]; LEA ECX, [ESP+0x4]; PUSH EAX; MOV EAX, ESP; PUSH EAX}
Device \Driver\atapi \Device\Ide\IdePort0 [F71BDB40] atapi.sys[unknown section] {MOV EDX, [ESP+0x8]; LEA ECX, [ESP+0x4]; PUSH EAX; MOV EAX, ESP; PUSH EAX}
Device \Driver\atapi \Device\Ide\IdePort1 [F71BDB40] atapi.sys[unknown section] {MOV EDX, [ESP+0x8]; LEA ECX, [ESP+0x4]; PUSH EAX; MOV EAX, ESP; PUSH EAX}
Device \Driver\Ftdisk \Device\HarddiskVolume3 863D91F8
Device \Driver\NetBT \Device\NetBt_Wins_Export 85F7C428
Device \Driver\nvata \Device\00000092 864491F8
Device \Driver\NetBT \Device\NetbiosSmb 85F7C428
AttachedDevice \Driver\Tcpip \Device\Udp Mpfp.sys (McAfee Personal Firewall Plus Driver/McAfee, Inc.)
AttachedDevice \Driver\Tcpip \Device\RawIp Mpfp.sys (McAfee Personal Firewall Plus Driver/McAfee, Inc.)
Device \Driver\usbohci \Device\USBFDO-0 862951F8
Device \Driver\nvata \Device\NvAta0 864491F8
Device \Driver\usbehci \Device\USBFDO-1 862961F8
Device \FileSystem\MRxSmb \Device\LanmanDatagramReceiver 862811F8
Device \FileSystem\MRxSmb \Device\LanmanRedirector 862811F8
Device \Driver\Ftdisk \Device\FtControl 863D91F8
Device \Driver\NetBT \Device\NetBT_Tcpip_{9ABAD186-9AE6-432D-ABE9-03B5C8E10A69} 85F7C428
Device \Driver\a179w7om \Device\Scsi\a179w7om1Port3Path0Target0Lun0 8630C1F8
Device \Driver\a179w7om \Device\Scsi\a179w7om1 8630C1F8
Device \FileSystem\Fastfat \Fat 8616D1F8
AttachedDevice \FileSystem\Fastfat \Fat mfehidk.sys (Host Intrusion Detection Link Driver/McAfee, Inc.)
Device \FileSystem\Cdfs \Cdfs 85EB1500
---- Registry - GMER 1.0.15 ----
Reg HKLM\SYSTEM\ControlSet001\Services\hjgruikjvmhcac@start 1
Reg HKLM\SYSTEM\ControlSet001\Services\hjgruikjvmhcac@type 1
Reg HKLM\SYSTEM\ControlSet001\Services\hjgruikjvmhcac@group file system
Reg HKLM\SYSTEM\ControlSet001\Services\hjgruikjvmhcac@imagepath \systemroot\system32\drivers\hjgruixkneyydp.sys
Reg HKLM\SYSTEM\ControlSet001\Services\hjgruikjvmhcac\main (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet001\Services\hjgruikjvmhcac\main@aid 10156
Reg HKLM\SYSTEM\ControlSet001\Services\hjgruikjvmhcac\main@sid 0
Reg HKLM\SYSTEM\ControlSet001\Services\hjgruikjvmhcac\main@cmddelay 14400
Reg HKLM\SYSTEM\ControlSet001\Services\hjgruikjvmhcac\main\delete (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet001\Services\hjgruikjvmhcac\main\injector (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet001\Services\hjgruikjvmhcac\main\injector@* hjgruiwsp.dll
Reg HKLM\SYSTEM\ControlSet001\Services\hjgruikjvmhcac\main\tasks (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet001\Services\hjgruikjvmhcac\modules (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet001\Services\hjgruikjvmhcac\modules@hjgruirk.sys \systemroot\system32\drivers\hjgruixkneyydp.sys
Reg HKLM\SYSTEM\ControlSet001\Services\hjgruikjvmhcac\modules@hjgruicmd.dll \systemroot\system32\hjgruiqvnlkaat.dll
Reg HKLM\SYSTEM\ControlSet001\Services\hjgruikjvmhcac\modules@hjgruilog.dat \systemroot\system32\hjgruiqppcixfn.dat
Reg HKLM\SYSTEM\ControlSet001\Services\hjgruikjvmhcac\modules@hjgruiwsp.dll \systemroot\system32\hjgruiyfgphouk.dll
Reg HKLM\SYSTEM\ControlSet001\Services\hjgruikjvmhcac\modules@hjgrui.dat \systemroot\system32\hjgruimrfohwad.dat
Reg HKLM\SYSTEM\ControlSet001\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4 (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet001\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4@p0 C:\Program Files\DAEMON Tools Lite\
Reg HKLM\SYSTEM\ControlSet001\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4@h0 0
Reg HKLM\SYSTEM\ControlSet001\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4@khjeh 0x5A 0xD0 0x5C 0x51 ...
Reg HKLM\SYSTEM\ControlSet001\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001 (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet001\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001@a0 0x20 0x01 0x00 0x00 ...
Reg HKLM\SYSTEM\ControlSet001\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001@khjeh 0x0E 0x1B 0x4F 0x4A ...
Reg HKLM\SYSTEM\ControlSet001\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001\0Jf40 (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet001\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001\0Jf40@khjeh 0x4C 0xB3 0x60 0x9A ...
Reg HKLM\SYSTEM\ControlSet002\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4 (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet002\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4@p0 C:\Program Files\DAEMON Tools Lite\
Reg HKLM\SYSTEM\ControlSet002\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4@h0 0
Reg HKLM\SYSTEM\ControlSet002\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4@khjeh 0x5A 0xD0 0x5C 0x51 ...
Reg HKLM\SYSTEM\ControlSet002\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001 (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet002\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001@a0 0x20 0x01 0x00 0x00 ...
Reg HKLM\SYSTEM\ControlSet002\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001@khjeh 0x0E 0x1B 0x4F 0x4A ...
Reg HKLM\SYSTEM\ControlSet002\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001\0Jf40 (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet002\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001\0Jf40@khjeh 0x4C 0xB3 0x60 0x9A ...
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg@s1 771343423
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg@s2 285507792
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg@h0 1
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4@p0 C:\Program Files\DAEMON Tools Lite\
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4@h0 0
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4@khjeh 0x5A 0xD0 0x5C 0x51 ...
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001@a0 0x20 0x01 0x00 0x00 ...
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001@khjeh 0x0E 0x1B 0x4F 0x4A ...
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001\0Jf40
Reg HKLM\SYSTEM\CurrentControlSet\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001\0Jf40@khjeh 0x4C 0xB3 0x60 0x9A ...
Reg HKLM\SYSTEM\ControlSet004\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4 (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet004\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4@p0 C:\Program Files\DAEMON Tools Lite\
Reg HKLM\SYSTEM\ControlSet004\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4@h0 0
Reg HKLM\SYSTEM\ControlSet004\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4@khjeh 0x5A 0xD0 0x5C 0x51 ...
Reg HKLM\SYSTEM\ControlSet004\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001 (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet004\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001@a0 0x20 0x01 0x00 0x00 ...
Reg HKLM\SYSTEM\ControlSet004\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001@khjeh 0x0E 0x1B 0x4F 0x4A ...
Reg HKLM\SYSTEM\ControlSet004\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001\0Jf40 (not active ControlSet)
Reg HKLM\SYSTEM\ControlSet004\Services\sptd\Cfg\19659239224E364682FA4BAF72C53EA4\00000001\0Jf40@khjeh 0x4C 0xB3 0x60 0x9A ...
Reg HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\OptionalComponents\IMAIL@Installed 1
Reg HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\OptionalComponents\MAPI@Installed 1
Reg HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\OptionalComponents\MAPI@NoChange 1
Reg HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\OptionalComponents\MSFS@Installed 1
Reg HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Prefetcher@TracesProcessed 79
Reg HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows@DeviceNotSelectedTimeout 15
Reg HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows@GDIProcessHandleQuota 10000
Reg HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows@Spooler yes
Reg HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows@swapdisk
Reg HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows@TransmissionRetryTimeout 90
Reg HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows@USERProcessHandleQuota 10000
Reg HKCU\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{D27CDB6E-AE6D-11CF-96B8-444553540000}\iexplore@Count 100522
---- Files - GMER 1.0.15 ----
File C:\Documents and Settings\YM\Cookies\ym@my.screenname.aol[2].txt 326 bytes
File C:\Documents and Settings\YM\Local Settings\Temp\~DFBBEB.tmp 16384 bytes
---- EOF - GMER 1.0.15 ----
Here is the Rooter txt
Rooter.exe (v1.0.2) by Eric_71
.
SeDebugPrivilege granted successfully ...
.
Windows XP . (5.1.2600) Service Pack 3
[32_bits] - x86 Family 15 Model 72 Stepping 2, AuthenticAMD
.
[wscsvc] (Security Center) RUNNING (state:4)
[SharedAccess] RUNNING (state:4)
.
Internet Explorer 7.0.5730.13
.
C:\ [Fixed-NTFS] .. ( Total:80 Go - Free:24 Go )
D:\ [Fixed-FAT32] .. ( Total:11 Go - Free:1 Go )
E:\ [CD_Rom]
F:\ [CD_Rom]
.
Scan : 18:30.03
Path : C:\Documents and Settings\YM\Desktop\Rooter.exe
User : YM ( Administrator -> YES )
.
----------------------\\ Processes
.
Locked [System Process] (0)
______ System (4)
______ \SystemRoot\System32\smss.exe (692)
______ \??\C:\WINDOWS\system32\csrss.exe (740)
______ \??\C:\WINDOWS\system32\winlogon.exe (772)
______ C:\WINDOWS\system32\services.exe (816)
______ C:\WINDOWS\system32\lsass.exe (828)
______ C:\WINDOWS\system32\svchost.exe (1000)
______ C:\WINDOWS\system32\svchost.exe (1048)
______ C:\WINDOWS\System32\svchost.exe (1088)
______ C:\WINDOWS\system32\svchost.exe (1180)
______ C:\WINDOWS\system32\svchost.exe (1204)
______ C:\WINDOWS\system32\LEXBCES.EXE (1500)
______ C:\WINDOWS\system32\spoolsv.exe (1544)
______ C:\WINDOWS\system32\LEXPPS.EXE (1596)
______ C:\WINDOWS\Explorer.EXE (1988)
______ C:\Program Files\hpq\HP Wireless Assistant\HP Wireless Assistant.exe (316)
______ C:\WINDOWS\system32\RUNDLL32.EXE (340)
______ C:\Program Files\Synaptics\SynTP\SynTPEnh.exe (516)
______ C:\Program Files\HP\QuickPlay\QPService.exe (572)
______ C:\Program Files\Hp\HP Software Update\HPWuSchd2.exe (600)
______ C:\Program Files\Hewlett-Packard\HP Quick Launch Buttons\QlbCtrl.exe (608)
______ C:\WINDOWS\ehome\ehtray.exe (624)
______ C:\Program Files\iTunes\iTunesHelper.exe (684)
______ C:\WINDOWS\system32\svchost.exe (128)
______ C:\Program Files\Common Files\AOL\1186906696\ee\AOLSoftware.exe (952)
______ C:\WINDOWS\system32\msdtc.exe (1108)
______ C:\Program Files\Common Files\Real\Update_OB\realsched.exe (1156)
______ C:\Program Files\QuickTime\QTTask.exe (1244)
______ C:\Program Files\McAfee.com\Agent\mcagent.exe (1280)
______ C:\Program Files\Lexmark 5600-6600 Series\lxdumon.exe (1352)
______ C:\Program Files\Common Files\AOL\TopSpeed\2.0\aoltsmon.exe (1384)
______ C:\Program Files\Messenger\msmsgs.exe (1424)
______ C:\Program Files\SUPERAntiSpyware\SUPERAntiSpyware.exe (1676)
______ C:\Program Files\Common Files\Apple\Mobile Device Support\bin\AppleMobileDeviceService.exe (1688)
______ C:\WINDOWS\system32\ctfmon.exe (1692)
______ C:\Program Files\Common Files\AOL\TopSpeed\2.0\aoltpspd.exe (1748)
______ C:\Program Files\Symantec\LiveUpdate\AluSchedulerSvc.exe (876)
______ C:\Program Files\Windows Media Player\WMPNSCFG.exe (1792)
______ C:\Program Files\Lexmark 5600-6600 Series\lxduMsdMon.exe (1764)
______ C:\Documents and Settings\YM\Local Settings\Application Data\gcawpp\wuwdsysguard.exe (1836)
______ C:\Program Files\America Online 9.0a\waol.exe (1888)
______ C:\Program Files\Bonjour\mDNSResponder.exe (2168)
______ C:\WINDOWS\eHome\ehRecvr.exe (2216)
______ C:\WINDOWS\eHome\ehSched.exe (2232)
______ c:\program files\common files\aol\1186906696\ee\services\antiSpywareApp\ver2_0_32_1\AOLSP Scheduler.exe (2428)
______ C:\WINDOWS\System32\svchost.exe (2700)
______ C:\Program Files\Java\jre6\bin\jqs.exe (2756)
______ C:\Program Files\Common Files\LightScribe\LSSrvc.exe (2772)
______ C:\WINDOWS\system32\lxducoms.exe (2852)
______ C:\Program Files\McAfee\SiteAdvisor\McSACore.exe (2928)
______ C:\PROGRA~1\McAfee\MSC\mcmscsvc.exe (2968)
______ c:\PROGRA~1\COMMON~1\mcafee\mna\mcnasvc.exe (3100)
______ c:\PROGRA~1\COMMON~1\mcafee\mcproxy\mcproxy.exe (3260)
______ C:\PROGRA~1\McAfee\VIRUSS~1\mcshield.exe (3296)
______ C:\Program Files\McAfee\MPF\MPFSrv.exe (3372)
______ C:\Program Files\McAfee\MSK\MskSrver.exe (3420)
______ C:\WINDOWS\system32\nvsvc32.exe (3500)
______ C:\WINDOWS\system32\svchost.exe (208)
______ C:\WINDOWS\system32\svchost.exe (248)
______ C:\WINDOWS\system32\mqsvc.exe (532)
______ C:\WINDOWS\ehome\mcrdsvc.exe (1044)
______ C:\Program Files\Windows Media Player\WMPNetwk.exe (2248)
______ C:\WINDOWS\system32\mqtgsvc.exe (2660)
______ C:\Program Files\Common Files\AOL\ACS\AOLacsd.exe (2932)
______ C:\WINDOWS\system32\wbem\wmiprvse.exe (2052)
______ C:\WINDOWS\system32\wbem\wmiprvse.exe (3868)
______ C:\Program Files\Common Files\AOL\1186906696\EE\aolsoftware.exe (4728)
______ C:\Program Files\iPod\bin\iPodService.exe (4968)
______ C:\WINDOWS\system32\dllhost.exe (5020)
______ C:\WINDOWS\System32\alg.exe (5628)
______ C:\WINDOWS\eHome\ehmsas.exe (4236)
______ C:\PROGRA~1\McAfee\VIRUSS~1\mcsysmon.exe (2464)
______ C:\Program Files\America Online 9.0a\shellmon.exe (5528)
______ C:\Documents and Settings\YM\Desktop\gmer.exe (5252)
______ C:\PROGRA~1\McAfee\MSM\McSmtFwk.exe (5884)
______ C:\Documents and Settings\YM\Desktop\Rooter.exe (5128)
.
----------------------\\ Device\Harddisk0\
.
\Device\Harddisk0 [Sectors : 63 x 512 Bytes]
.
\Device\Harddisk0\Partition1 --[ MBR ]-- (Start_Offset:32256 | Length:86612166144)
\Device\Harddisk0\Partition2 (Start_Offset:86620423680 | Length:12329694720)
\Device\Harddisk0\Partition3 (Start_Offset:98950118400 | Length:1077511680)
.
----------------------\\ Scheduled Tasks
.
C:\WINDOWS\Tasks\desktop.ini
C:\WINDOWS\Tasks\McDefragTask.job
C:\WINDOWS\Tasks\McQcTask.job
C:\WINDOWS\Tasks\SA.DAT
.
----------------------\\ Registry
.
.
----------------------\\ Files & Folders
.
----------------------\\ Scan completed at 18:30.51
.
C:\Rooter$\Rooter_2.txt - (08/11/2009 | 18:30.51)
#6
![[Resolved] Virus on my computer: post #6](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 08 November 2009 - 06:20 PM
Download Combofix from any of the links below. You must rename it before saving it. Save it to your desktop.
Link 1
Link 2
Link 3


* IMPORTANT !!! Save ComboFix.exe to your Desktop
- Disable your AntiVirus and AntiSpyware applications, usually via a right click on the System Tray icon. They may otherwise interfere with our tools
- See this Link for programs that need to be disabled and instruction on how to disable them.
- Remember to re-enable them when we're done.
- Double click on ComboFix.exe & follow the prompts.
- As part of it's process, ComboFix will check to see if the Microsoft Windows Recovery Console is installed. With malware infections being as they are today, it's strongly recommended to have this pre-installed on your machine before doing any malware removal. It will allow you to boot up into a special recovery/repair mode that will allow us to more easily help you should your computer have a problem after an attempted removal of malware.
- Follow the prompts to allow ComboFix to download and install the Microsoft Windows Recovery Console, and when prompted, agree to the End-User License Agreement to install the Microsoft Windows Recovery Console.
**Please note: If the Microsoft Windows Recovery Console is already installed, ComboFix will continue it's malware removal procedures.

Once the Microsoft Windows Recovery Console is installed using ComboFix, you should see the following message:

Click on Yes, to continue scanning for malware.
When finished, it shall produce a log for you. Please include the C:\ComboFix.txt in your next reply .[/b]
*If there is no internet connection when Combofix has completely finished then restart your computer to restore back the connections.
- Download random's system information tool (RSIT) by random/random from here and save it to your desktop.
- Double click on RSIT.exe to run RSIT.
- Click Continue at the disclaimer screen.
- Once it has finished, two logs will open. Please post the contents of both log.txt (<<will be maximized) and info.txt (<<will be minimized)
The forum is staffed by volunteers who donate their time and expertise.
If you feel you have been helped, please consider a donation.

Find us on Facebook
Please LIKE and SHARE
Just a reminder that threads will be closed if no reply in 3 days.
#7
![[Resolved] Virus on my computer: post #7](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 08 November 2009 - 07:22 PM
#8
![[Resolved] Virus on my computer: post #8](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 08 November 2009 - 08:04 PM
Please run this free online virus scanner from ESET
- Note: You will need to use Internet explorer for this scan
- Tick the box next to YES, I accept the Terms of Use.
- Click Start
- When asked, allow the activex control to install
- Click Start
- Make sure that the option Remove found threats is ticked, and the option Scan unwanted applications is checked
- Click Scan
- Wait for the scan to finish
- Use notepad to open the logfile located at C:\Program Files\EsetOnlineScanner\log.txt
- Copy and paste that log as a reply to this topic
The forum is staffed by volunteers who donate their time and expertise.
If you feel you have been helped, please consider a donation.

Find us on Facebook
Please LIKE and SHARE
Just a reminder that threads will be closed if no reply in 3 days.
#9
![[Resolved] Virus on my computer: post #9](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 09 November 2009 - 10:07 AM
#10
![[Resolved] Virus on my computer: post #10](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 09 November 2009 - 11:33 AM
To Enter Safemode
- Go to Start> Shut off your Computer> Restart
- As the computer starts to boot-up, Tap the F8 KEY somewhat rapidly,
this will bring up a menu. - Use the Up and Down Arrow Keys to scroll up to Safemode with Networking
- Then press the Enter Key on your Keyboard
The forum is staffed by volunteers who donate their time and expertise.
If you feel you have been helped, please consider a donation.

Find us on Facebook
Please LIKE and SHARE
Just a reminder that threads will be closed if no reply in 3 days.
Register to Remove
#11
![[Resolved] Virus on my computer: post #11](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 10 November 2009 - 08:49 AM
#12
![[Resolved] Virus on my computer: post #12](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 10 November 2009 - 09:26 AM
You need to enable windows to show all files and folders, instructions Here
Go to VirusTotal and submit these files for analysis, just use the BROWSE feature and then Send File , you will get a report back, post the report into this thread for me to see.
c:\windows\system32\winlogon.exe
c:\windows\system32\userinit.exe
c:\windows\Explorer.EXE
The forum is staffed by volunteers who donate their time and expertise.
If you feel you have been helped, please consider a donation.

Find us on Facebook
Please LIKE and SHARE
Just a reminder that threads will be closed if no reply in 3 days.
#13
![[Resolved] Virus on my computer: post #13](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 10 November 2009 - 10:56 AM
#14
![[Resolved] Virus on my computer: post #14](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 10 November 2009 - 12:26 PM
Where you able to upload those files ? See if you can run this program.
Please download Malwarebytes' Anti-Malware from Here or Here
- Double-click mbam-setup.exe and follow the prompts to install the program.
- At the end, be sure a checkmark is placed next to Update Malwarebytes' Anti-Malware and Launch Malwarebytes' Anti-Malware, then click Finish.
- If an update is found, it will download and install the latest version.
- Once the program has loaded, select Perform quick scan, then click Scan.
- When the scan is complete, click OK, then Show Results to view the results.
- Be sure that everything is checked, and click Remove Selected .
- When completed, a log will open in Notepad. Please save it to a convenient location and post the results.
- Note: If you receive a notice that some of the items couldn't be removed, that they have been added to the delete on reboot list, please reboot.
The forum is staffed by volunteers who donate their time and expertise.
If you feel you have been helped, please consider a donation.

Find us on Facebook
Please LIKE and SHARE
Just a reminder that threads will be closed if no reply in 3 days.
#15
![[Resolved] Virus on my computer: post #15](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 10 November 2009 - 02:05 PM
http://www.virustota...9b1e-1257880388
Here is the second report
http://www.virustota...f53f-1257881276
Here is the third report
http://www.virustota...f455-1257881750
Here is the AntimMalware report
Malwarebytes' Anti-Malware 1.41
Database version: 3141
Windows 5.1.2600 Service Pack 3
11/10/2009 2:51:28 PM
mbam-log-2009-11-10 (14-51-28).txt
Scan type: Quick Scan
Objects scanned: 126712
Time elapsed: 10 minute(s), 7 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 2
Registry Values Infected: 2
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 0
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\Stats\{b6d223f6-c185-49a2-ba7e-a03e84744702} (Trojan.FakeAlert) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\AvScan (Trojan.FakeAlert) -> Quarantined and deleted successfully.
Registry Values Infected:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\nsqkatgd (Trojan.FakeAlert.N) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\nsqkatgd (Trojan.FakeAlert.N) -> Quarantined and deleted successfully.
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
(No malicious items detected)
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users



 This topic is locked
This topic is locked


