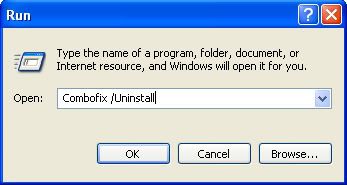
- Click the Browse button and search for the following file: C:\WINDOWS\system32\winlogon.exe
- Click Open
- Then click Send File
- Please be patient while the file is scanned.
- Once the scan results appear, please provide them in your next reply.
Please repeat the above process for these two files as well:
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
Please post the results in your next reply.



 This topic is locked
This topic is locked