[Resolved] Need help removing re-generating virus/trojan
#1
![[Resolved] Need help removing re-generating virus/trojan: post #1](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 28 October 2009 - 08:58 PM
Register to Remove
#2
![[Resolved] Need help removing re-generating virus/trojan: post #2](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 29 October 2009 - 06:24 AM
Please do the following:
Download ComboFix from either of these locations:
Link 1
Link 2
VERY IMPORTANT !!! Save ComboFix.exe to your Desktop
* IMPORTANT - Disable your AntiVirus and AntiSpyware applications, usually via a right click on the System Tray icon. They may otherwise interfere with our tools. If you have difficulty properly disabling your protective programs, refer to this link here
- Double click on ComboFix.exe & follow the prompts.
- Follow the prompts to allow ComboFix to download and install the Microsoft Windows Recovery Console, and when prompted, agree to the End-User License Agreement to install the Microsoft Windows Recovery Console.

- Once the Microsoft Windows Recovery Console is installed using ComboFix, you should see the following message:

- Click on Yes, to continue scanning for malware.
Notes:
1. Do not mouse-click Combofix's window while it is running. That may cause it to stall.
2. Do not "re-run" Combofix. If you have a problem, reply back for further instructions.
Please make sure you include the combo fix log in your next reply as well as describe how your computer is running now
Microsoft MVP 2010, 2011, 2012, 2013, 2014, 2015
#3
![[Resolved] Need help removing re-generating virus/trojan: post #3](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 29 October 2009 - 09:11 AM
ComboFix 09-10-28.08 - Owner 10/29/2009 10:37.1.1 - NTFSx86
Microsoft Windows XP Home Edition 5.1.2600.3.1252.1.1033.18.510.295 [GMT -4:00]
Running from: c:\documents and settings\Owner\Desktop\ComboFix.exe
AV: ZoneAlarm Security Suite Antivirus *On-access scanning disabled* (Updated) {5D467B10-818C-4CAB-9FF7-6893B5B8F3CF}
FW: ZoneAlarm Security Suite Firewall *disabled* {829BDA32-94B3-44F4-8446-F8FCFF809F8B}
.
ADS - svchost.exe: deleted 88 bytes in 2 streams.
((((((((((((((((((((((((((((((((((((((( Other Deletions )))))))))))))))))))))))))))))))))))))))))))))))))
.
c:\windows\system32\dovamewo.dll
c:\windows\system32\fotobike.dll
c:\windows\system32\gidahumu.dll
c:\windows\system32\giyikara.dll
c:\windows\system32\jadelamo.dll
c:\windows\system32\kedisuzo.dll
c:\windows\system32\nijopido.dll
c:\windows\system32\nimuhoke.dll.tmp
c:\windows\system32\nominenu.dll
c:\windows\system32\sakalimo.dll
c:\windows\system32\vonowiya.dll
c:\windows\system32\wuganabu.dll
c:\windows\system32\yaruvofo.dll
c:\windows\system32\zulagovi.dll
c:\windows\Tasks\keprutad.job
c:\windows\TEMP\logishrd\LVPrcInj01.dll
.
((((((((((((((((((((((((( Files Created from 2009-09-28 to 2009-10-29 )))))))))))))))))))))))))))))))
.
2009-10-26 00:59 . 2009-10-26 00:59 -------- d-----w- C:\VundoFix Backups
2009-10-25 04:29 . 2009-10-28 17:43 -------- d-----w- c:\program files\mutwgm
2009-10-08 02:49 . 2009-10-08 02:49 -------- d-----w- c:\documents and settings\Owner\Local Settings\Application Data\Identities
.
(((((((((((((((((((((((((((((((((((((((( Find3M Report ))))))))))))))))))))))))))))))))))))))))))))))))))))
.
2009-10-29 14:48 . 2009-08-22 18:08 167114784 --sha-w- c:\windows\system32\drivers\fidbox.dat
2009-10-29 14:42 . 2009-08-22 18:08 2238236 --sha-w- c:\windows\system32\drivers\fidbox.idx
2009-10-26 03:32 . 2002-06-25 21:47 14336 ----a-w- c:\windows\system32\svchost.exe
2009-10-13 02:19 . 2008-06-17 16:39 4212 ---ha-w- c:\windows\system32\zllictbl.dat
2009-09-22 23:59 . 2008-06-17 13:04 35464 ----a-w- c:\documents and settings\Owner\Local Settings\Application Data\GDIPFONTCACHEV1.DAT
2009-09-20 03:57 . 2009-09-20 03:57 -------- d-----w- c:\program files\MSBuild
2009-09-20 03:57 . 2009-09-20 03:57 -------- d-----w- c:\program files\Reference Assemblies
2009-09-20 03:15 . 2009-09-20 03:15 -------- d-----w- c:\documents and settings\All Users\Application Data\PC Drivers HeadQuarters
2009-09-11 14:18 . 2002-06-25 21:42 136192 ----a-w- c:\windows\system32\msv1_0.dll
2009-09-04 21:03 . 2002-06-25 21:41 58880 ----a-w- c:\windows\system32\msasn1.dll
2009-08-29 08:08 . 2002-03-05 12:56 916480 ----a-w- c:\windows\system32\wininet.dll
2009-08-26 08:00 . 2002-06-25 21:47 247326 ----a-w- c:\windows\system32\strmdll.dll
2009-08-05 09:01 . 2008-06-17 13:20 204800 ----a-w- c:\windows\system32\mswebdvd.dll
2009-08-05 00:44 . 2002-06-25 21:43 2189184 ----a-w- c:\windows\system32\ntoskrnl.exe
2009-08-04 14:20 . 2002-06-25 21:43 2066048 ----a-w- c:\windows\system32\ntkrnlpa.exe
2009-07-29 13:15 . 2009-07-29 13:15 60928 --sha-w- c:\windows\system32\tanovivo.dll
.
((((((((((((((((((((((((((((((((((((( Reg Loading Points ))))))))))))))))))))))))))))))))))))))))))))))))))
.
.
*Note* empty entries & legit default entries are not shown
REGEDIT4
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"HotKeysCmds"="c:\windows\system32\hkcmd.exe" [2005-10-19 126976]
"REGSHAVE"="c:\program files\REGSHAVE\REGSHAVE.EXE" [2002-02-05 53248]
"WinPatrol"="c:\program files\BillP Studios\WinPatrol\winpatrol.exe" [2008-10-09 333120]
"LogitechQuickCamRibbon"="c:\program files\Logitech\QuickCam\Quickcam.exe" [2008-12-20 2656528]
"ZoneAlarm Client"="c:\program files\Zone Labs\ZoneAlarm\zlclient.exe" [2009-05-29 1005960]
"HP Software Update"="c:\program files\HP\HP Software Update\HPWuSchd2.exe" [2007-05-08 54840]
c:\documents and settings\All Users\Start Menu\Programs\Startup\
APC UPS Status.lnk - c:\program files\APC\APC PowerChute Personal Edition\Display.exe [2008-6-17 221247]
HP Digital Imaging Monitor.lnk - c:\program files\HP\Digital Imaging\bin\hpqtra08.exe [2005-5-11 282624]
[HKEY_LOCAL_MACHINE\software\microsoft\security center\Monitoring\ZoneLabsFirewall]
"DisableMonitoring"=dword:00000001
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile]
"EnableFirewall"= 0 (0x0)
[HKLM\~\services\sharedaccess\parameters\firewallpolicy\standardprofile\AuthorizedApplications\List]
"%windir%\\system32\\sessmgr.exe"=
"%windir%\\Network Diagnostic\\xpnetdiag.exe"=
"c:\\Program Files\\Yahoo!\\Messenger\\YahooMessenger.exe"=
"c:\\WINDOWS\\system32\\ZoneLabs\\vsmon.exe"=
"c:\\WINDOWS\\system32\\spoolsv.exe"=
"c:\\Program Files\\Common Files\\logishrd\\LVMVFM\\LVPrcSrv.exe"=
"c:\\Program Files\\HP\\Digital Imaging\\bin\\hpqste08.exe"=
"c:\\Program Files\\Logitech\\QuickCam\\Quickcam.exe"=
--- Other Services/Drivers In Memory ---
*NewlyCreated* - CLASSPNP_2
*NewlyCreated* - MBR
*NewlyCreated* - PCIIDEX_2
*Deregistered* - CLASSPNP_2
*Deregistered* - mbr
*Deregistered* - PCIIDEX_2
.
Contents of the 'Scheduled Tasks' folder
2009-10-28 c:\windows\Tasks\User_Feed_Synchronization-{245287B3-D295-4B19-A02C-38FD72D7C759}.job
- c:\windows\system32\msfeedssync.exe [2007-08-13 08:31]
.
.
------- Supplementary Scan -------
.
uStart Page = hxxp://www.yahoo.com/
uSearchMigratedDefaultURL = hxxp://search.yahoo.com/search?p={searchTerms}&ei=utf-8&fr=b1ie7
mSearch Bar = hxxp://us.rd.yahoo.com/customize/ie/defaults/sb/msgr9/*http://www.yahoo.com/ext/search/search.html
uSearchURL,(Default) = hxxp://us.rd.yahoo.com/customize/ie/defaults/su/msgr9/*http://www.yahoo.com
DPF: Microsoft XML Parser for Java - file://c:\windows\Java\classes\xmldso.cab
.
- - - - ORPHANS REMOVED - - - -
BHO-{c674c59c-4970-4a98-96a2-ef4edb27481c} - jadelamo.dll
HKLM-Run-bakuweyuwa - fotobike.dll
SharedTaskScheduler-{b5be6fba-a402-499e-b1f3-0c7214a1bbc0} - c:\windows\system32\deporare.dll
SharedTaskScheduler-{7de2e170-b934-4133-98d8-2c28d4f7ba88} - c:\windows\system32\kedisuzo.dll
SSODL-zonutoyes-{b5be6fba-a402-499e-b1f3-0c7214a1bbc0} - c:\windows\system32\deporare.dll
SSODL-fokoyahey-{7de2e170-b934-4133-98d8-2c28d4f7ba88} - c:\windows\system32\kedisuzo.dll
**************************************************************************
catchme 0.3.1398 W2K/XP/Vista - rootkit/stealth malware detector by Gmer, http://www.gmer.net
Rootkit scan 2009-10-29 10:46
Windows 5.1.2600 Service Pack 3 NTFS
scanning hidden processes ...
scanning hidden autostart entries ...
scanning hidden files ...
scan completed successfully
hidden files: 0
**************************************************************************
.
--------------------- DLLs Loaded Under Running Processes ---------------------
- - - - - - - > 'explorer.exe'(2212)
c:\windows\system32\WININET.dll
c:\windows\system32\ieframe.dll
c:\windows\system32\webcheck.dll
c:\windows\system32\WPDShServiceObj.dll
c:\windows\system32\PortableDeviceTypes.dll
c:\windows\system32\PortableDeviceApi.dll
.
------------------------ Other Running Processes ------------------------
.
c:\program files\APC\APC PowerChute Personal Edition\mainserv.exe
c:\program files\Java\jre6\bin\jqs.exe
c:\windows\system32\wscntfy.exe
c:\program files\Common Files\Logishrd\LQCVFX\COCIManager.exe
c:\program files\APC\APC PowerChute Personal Edition\apcsystray.exe
c:\program files\HP\Digital Imaging\bin\hpqSTE08.exe
.
**************************************************************************
.
Completion time: 2009-10-29 10:50 - machine was rebooted
ComboFix-quarantined-files.txt 2009-10-29 14:50
Pre-Run: 101,128,634,368 bytes free
Post-Run: 101,159,579,648 bytes free
WindowsXP-KB310994-SP2-Home-BootDisk-ENU.exe
[boot loader]
timeout=2
default=multi(0)disk(0)rdisk(0)partition(1)\WINDOWS
[operating systems]
c:\cmdcons\BOOTSECT.DAT="Microsoft Windows Recovery Console" /cmdcons
multi(0)disk(0)rdisk(0)partition(2)\WINDOWS="Microsoft Windows XP Home Edition" /fastdetect /NoExecute=OptIn
multi(0)disk(0)rdisk(0)partition(1)\WINDOWS="Microsoft Windows XP Home Edition" /fastdetect /NoExecute=OptIn
- - End Of File - - 0CD25E1E291E0D57588658D14A738450
****** PS: haven't done any surfing while this problem exists to offer more description however, i could not access your reply via the email link, had to access WTT home page, direct (multiple times) ... aside from the obvious, overall function seems normal and acceptable.
mouse
#4
![[Resolved] Need help removing re-generating virus/trojan: post #4](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 29 October 2009 - 09:26 AM
Please do the following:
- Very Important! Temporarily disable your anti-virus, script blocking and any anti-malware real-time protection before following the steps below.
- They can interfere with ComboFix or remove some of its embedded files which may cause "unpredictable results".
Here's how to do that:
Click Start > Run type Notepad click OK.
This will open an empty notepad file:
Copy all the text inside of the code box - Press Ctrl+C (or right click on the highlighted section and choose 'copy')
http://forums.whatthetech.com/Need_help_removing_re_generating_virus_trojan_t107988.html&view=findpost&p=606739#entry606739 Collect:: c:\windows\system32\tanovivo.dll Folder:: c:\program files\mutwgm
Now paste the copied text into the open notepad - press CTRL+V (or right click and choose 'paste')
Save this file to your desktop, Save this as "CFScript"
Here's how to do that:
1.Click File;
2.Click Save As... Change the directory to your desktop;
3.Change the Save as type to "All Files";
4.Type in the file name: CFScript
5.Click Save ...

- Referring to the screenshot above, drag CFScript.txt into ComboFix.exe.
- ComboFix will now run a scan on your system. It may reboot your system when it finishes. This is normal.
- When finished, it shall produce a log for you.
- Copy and paste the contents of the log in your next reply.
CAUTION: Do not mouse-click ComboFix's window while it is running. That may cause it to stall.
NEXT
Please do the following:
Download Inherit and save it to your desk top
Drag each of the exe files that you are unable to run into Inherit.exe (must be the exe - not the shortcut)
Then wait for it to say "OK"
Drop MBAM.exe into inherit - that should free it up to run. Update Malwarebytes from the Update Tab
Run a quick scan. Delete anything it finds. Post the resulting log.
Microsoft MVP 2010, 2011, 2012, 2013, 2014, 2015
#5
![[Resolved] Need help removing re-generating virus/trojan: post #5](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 29 October 2009 - 01:09 PM
#6
![[Resolved] Need help removing re-generating virus/trojan: post #6](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 29 October 2009 - 01:22 PM
Please do the following:
Using Internet Explorer or Firefox, visit Kaspersky Online Scanner:
1. Click Accept, when prompted to download and install the program files and database of malware definitions.
2. To optimize scanning time and produce a more sensible report for review:
- Close any open programs
- Turn off the real time scanner of any existing antivirus program while performing the online scan
3. Click Run at the Security prompt. The program will then begin downloading and installing and will also update the database. Please be patient as this can take several minutes.
- Once the update is complete, click on My Computer under the green Scan bar to the left to start the scan.
- Once the scan is complete, it will display if your system has been infected. It does not provide an option to clean/disinfect. We only require a report from it.
- Do NOT be alarmed by what you see in the report. Many of the finds have likely been quarantined.
- Click View scan report at the bottom.
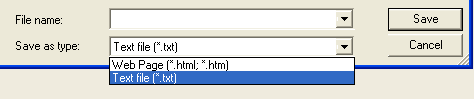
- Click the Save as Text button to save the file to your desktop so that you may post it in your next reply
NEXT
Please post a fresh DDS Log and Attach.txt
Microsoft MVP 2010, 2011, 2012, 2013, 2014, 2015
#7
![[Resolved] Need help removing re-generating virus/trojan: post #7](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 29 October 2009 - 01:22 PM
#8
![[Resolved] Need help removing re-generating virus/trojan: post #8](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 29 October 2009 - 01:59 PM
Microsoft MVP 2010, 2011, 2012, 2013, 2014, 2015
#9
![[Resolved] Need help removing re-generating virus/trojan: post #9](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 29 October 2009 - 08:11 PM
Attached Files
#10
![[Resolved] Need help removing re-generating virus/trojan: post #10](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 29 October 2009 - 10:17 PM
Just some house keeping to do now:
Please do the following:
Visit ADOBEand download the latest version of Acrobat Reader (version 9.2)
Having the latest updates ensures there are no security vulnerabilities in your system.
NEXT
Go to Start > Run > copy/paste the following text into the open run box > javacpl.cpl
> Press Enter > Select the Update tab > Click Update now
NEXT
Follow these steps to uninstall Combofix
- Click START then RUN
- Now type Combofix /uninstall in the runbox and click OK. Note the space between the ..X and the /U, it needs to be there.
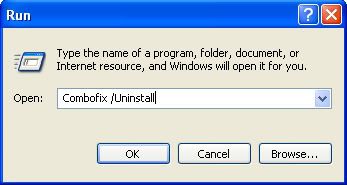
NEXT
Now to remove the rest of the tools that we have used in fixing your machine:
- Make sure you have an Internet Connection.
- Download OTC to your desktop and run it
- A list of tool components used in the Cleanup of malware will be downloaded.
- If your Firewall or Real Time protection attempts to block OTC to reach the Internet, please allow the application to do so.
- Click Yes to begin the Cleanup process and remove these components, including this application.
- You will be asked to reboot the machine to finish the Cleanup process. If you are asked to reboot the machine choose Yes.
NOTE: If there are any remaining logs/tools on your desktop after running this tool > right click and delete them.
NEXT
Below I have included a number of recommendations for how to protect your computer against malware infections.
- It is good security practice to change your passwords to all your online accounts on a fairly regular basis, this is especially true after an infection. Refer to this Microsoft article
Strong passwords: How to create and use them
Then consider a password keeper, to keep all your passwords safe.
- Keep Windows updated by regularly checking their website at :
http://windowsupdate.microsoft.com/
This will ensure your computer has always the latest security updates available installed on your computer.
- SpywareBlaster protects against bad ActiveX, it immunizes your PC against them.
- SpywareGuard offers realtime protection from spyware installation attempts. Make sure you are only running one real-time anti-spyware protection program ( eg : TeaTimer, Windows Defender ) or there will be a conflict.
- Make Internet Explorer more secure
- Click Start > Run
- Type Inetcpl.cpl & click OK
- Click on the Security tab
- Click Reset all zones to default level
- Make sure the Internet Zone is selected & Click Custom level
- In the ActiveX section, set the first two options ("Download signed and unsigned ActiveX controls) to "Prompt", and ("Initialize and Script ActiveX controls not marked as safe") to "Disable".
- Next Click OK, then Apply button and then OK to exit the Internet Properties page.
- ATF Cleaner - Cleans temporary files from IE and Windows, empties the recycle bin and more. Great tool to help speed up your computer and knock out those nasties that like to reside in the temp folders.
- MVPS Hosts file replaces your current HOSTS file with one containing well known ad sites and other bad sites. Basically, this prevents your computer from connecting to those sites by redirecting them to 127.0.0.1 which is your local computer, meaning it will be difficult to infect yourself in the future.
WOT, Web of Trust, warns you about risky websites that try to scam visitors, deliver malware or send spam. Protect your computer against online threats by using WOT as your front-line layer of protection when browsing or searching in unfamiliar territory. WOT's color-coded icons show you ratings for 21 million websites, helping you avoid the dangerous sites:- Green to go
- Yellow for caution
- Red to stop
- Please consider using an alternate browser. Mozilla's Firefox browser is fantastic; it is much more
secure than Internet Explorer, immune to almost all known browser hijackers, and also has the best built-in pop up
blocker (as an added benefit!) that I have ever seen. If you are interested, Firefox may be downloaded from
Here
If you choose to use Firefox, I highly recommend this add-on to keep your PC even more secure.
- NoScript - for blocking ads and other potential website attacks
- Keep a backup of your important files - Now, more than ever, it's especially important to protect your digital files and memories. This article is full of good information on alternatives for home backup solutions.
- ERUNT (Emergency Recovery Utility NT) allows you to keep a complete backup of your registry and restore it when needed. The standard registry backup options that come with Windows back up most of the registry but not all of it. ERUNT however creates a complete backup set, including the Security hive and user related sections. ERUNT is easy to use and since it creates a full backup, there are no options or choices other than to select the location of the backup files. The backup set includes a small executable that will launch the registry restore if needed.
- In light of your recent issue, I'm sure you'd like to avoid any future infections. Please take a look at these well written articles:
Think Prevention.
PC Safety and Security--What Do I Need?.
**Be very wary with any security software that is advertised in popups or in other ways. They are not only usually of no use, but often have malware in them.
Thank you for your patience, and performing all of the procedures requested.
Please respond one last time so we can consider the thread resolved and close it, thank-you.
Microsoft MVP 2010, 2011, 2012, 2013, 2014, 2015
Register to Remove
#11
![[Resolved] Need help removing re-generating virus/trojan: post #11](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 31 October 2009 - 07:37 PM
#12
![[Resolved] Need help removing re-generating virus/trojan: post #12](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 04 November 2009 - 11:30 PM
#13
![[Resolved] Need help removing re-generating virus/trojan: post #13](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 04 November 2009 - 11:30 PM
Edited by Granny Mouse, 04 November 2009 - 11:40 PM.
#14
![[Resolved] Need help removing re-generating virus/trojan: post #14](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 05 November 2009 - 02:00 AM
#15
![[Resolved] Need help removing re-generating virus/trojan: post #15](https://forums.whatthetech.com/public/style_images/smart34xbuild2/icon_share.png)
Posted 05 November 2009 - 04:15 AM
Microsoft MVP 2010, 2011, 2012, 2013, 2014, 2015
0 user(s) are reading this topic
0 members, 0 guests, 0 anonymous users



 This topic is locked
This topic is locked



