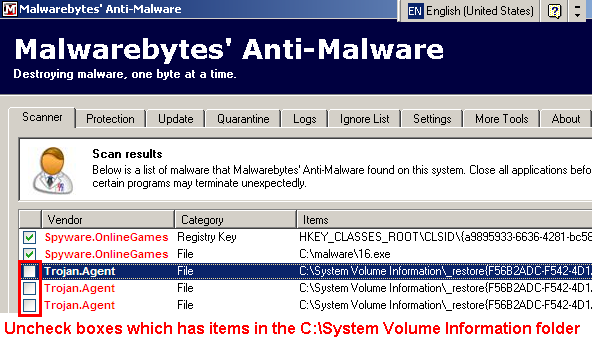
I have done a log file from Hijackthis also and included it below.
If anyone can see other problems out there thanks for your knowledge.
the worm in question is stopping me from accessing many files on my pc but also on my external hard drive
thanks for your much needed help.
Here is the log.
Logfile of Trend Micro HijackThis v2.0.4
Scan saved at 10:17:42 AM, on 16/05/2010
Platform: Windows XP SP3 (WinNT 5.01.2600)
MSIE: Internet Explorer v8.00 (8.00.6001.18702)
Boot mode: Normal
Running processes:
C:\WINDOWS\System32\smss.exe
C:\WINDOWS\system32\winlogon.exe
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\System32\svchost.exe
C:\WINDOWS\system32\svchost.exe
C:\Program Files\Intel\Wireless\Bin\EvtEng.exe
C:\Program Files\Intel\Wireless\Bin\S24EvMon.exe
C:\Program Files\Intel\Wireless\Bin\WLKeeper.exe
C:\WINDOWS\system32\spoolsv.exe
C:\Program Files\Common Files\LightScribe\LSSrvc.exe
C:\Program Files\Nero\Nero8\Nero BackItUp\NBService.exe
C:\Program Files\Dell\NICCONFIGSVC\NICCONFIGSVC.exe
C:\Program Files\Intel\Wireless\Bin\RegSrvc.exe
C:\WINDOWS\system32\svchost.exe
C:\Documents and Settings\Owner\Desktop\online marketing\Email2DB2\Email2DBMailServer.exe
C:\Program Files\Intel\Wireless\Bin\ZcfgSvc.exe
C:\Program Files\Apoint\Apoint.exe
C:\Program Files\Dell\QuickSet\quickset.exe
C:\Program Files\ScanSoft\OmniPageSE2.0\OpwareSE2.exe
C:\WINDOWS\system32\hkcmd.exe
C:\WINDOWS\system32\igfxpers.exe
C:\Program Files\Apoint\Apntex.exe
C:\Program Files\Microsoft IntelliPoint\ipoint.exe
C:\WINDOWS\system32\igfxsrvc.exe
C:\Program Files\Vista Drive Icon\DrvIcon.exe
C:\WINDOWS\system32\ctfmon.exe
C:\Program Files\LClock\LClock.exe
C:\Program Files\Google\GoogleToolbarNotifier\GoogleToolbarNotifier.exe
c:\Program Files\Microsoft IntelliPoint\dpupdchk.exe
C:\Program Files\AVG\AVG8\avgtray.exe
C:\PROGRA~1\AVG\AVG8\avgwdsvc.exe
C:\PROGRA~1\AVG\AVG8\avgrsx.exe
C:\Program Files\Common Files\Adobe\Updater5\AdobeUpdater.exe
C:\Program Files\PC Connectivity Solution\ServiceLayer.exe
C:\WINDOWS\explorer.exe
C:\Program Files\Dodo Wireless Broadband\Dodo Wireless Broadband.exe
C:\Program Files\Mozilla Firefox\firefox.exe
C:\WINDOWS\system32\msiexec.exe
C:\Program Files\Trend Micro\HijackThis\HiJackThis.exe
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://go.microsoft....k/?LinkId=69157
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft....k/?LinkId=54896
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft....k/?LinkId=54896
R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://go.microsoft....k/?LinkId=69157
O2 - BHO: The blinkx Toolbar - {0069B690-7A2B-41C5-98CA-9F535B4C8532} - C:\Program Files\blinkx Remote Toolbar\the_blinkx_bho.dll
O2 - BHO: Adobe PDF Reader Link Helper - {06849E9F-C8D7-4D59-B87D-784B7D6BE0B3} - C:\Program Files\Common Files\Adobe\Acrobat\ActiveX\AcroIEHelper.dll
O2 - BHO: ShoppingReport - {100EB1FD-D03E-47FD-81F3-EE91287F9465} - C:\Program Files\ShoppingReport\Bin\2.6.58\ShoppingReport.dll
O2 - BHO: Skype add-on (mastermind) - {22BF413B-C6D2-4d91-82A9-A0F997BA588C} - C:\Program Files\Skype\Toolbars\Internet Explorer\SkypeIEPlugin.dll
O2 - BHO: WormRadar.com IESiteBlocker.NavFilter - {3CA2F312-6F6E-4B53-A66E-4E65E497C8C0} - C:\Program Files\AVG\AVG8\avgssie.dll
O2 - BHO: Windows Live Sign-in Helper - {9030D464-4C02-4ABF-8ECC-5164760863C6} - C:\Program Files\Common Files\Microsoft Shared\Windows Live\WindowsLiveLogin.dll
O2 - BHO: Google Toolbar Helper - {AA58ED58-01DD-4d91-8333-CF10577473F7} - C:\Program Files\Google\Google Toolbar\GoogleToolbar_32.dll
O2 - BHO: Google Toolbar Notifier BHO - {AF69DE43-7D58-4638-B6FA-CE66B5AD205D} - C:\Program Files\Google\GoogleToolbarNotifier\5.5.4723.1820\swg.dll
O3 - Toolbar: Easy-WebPrint - {327C2873-E90D-4c37-AA9D-10AC9BABA46C} - C:\Program Files\Canon\Easy-WebPrint\Toolband.dll
O3 - Toolbar: StylerToolBar - {D2F8F919-690B-4EA2-9FA7-A203D1E04F75} - C:\Program Files\Styler\TB\StylerTB.dll
O3 - Toolbar: The blinkx Toolbar - {E5A1ECE5-3E3D-4FE7-8447-78CB1FD377C6} - C:\Program Files\blinkx Remote Toolbar\the_blinkx_toolbar.dll
O3 - Toolbar: Google Toolbar - {2318C2B1-4965-11d4-9B18-009027A5CD4F} - C:\Program Files\Google\Google Toolbar\GoogleToolbar_32.dll
O4 - HKLM\..\Run: [Apoint] C:\Program Files\Apoint\Apoint.exe
O4 - HKLM\..\Run: [Dell QuickSet] C:\Program Files\Dell\QuickSet\quickset.exe
O4 - HKLM\..\Run: [Lexmark X74-X75] "C:\Program Files\Lexmark X74-X75\lxbbbmgr.exe"
O4 - HKLM\..\Run: [OpwareSE2] "C:\Program Files\ScanSoft\OmniPageSE2.0\OpwareSE2.exe"
O4 - HKLM\..\Run: [AVG8_TRAY] C:\PROGRA~1\AVG\AVG8\avgtray.exe
O4 - HKLM\..\Run: [igfxtray] C:\WINDOWS\system32\igfxtray.exe
O4 - HKLM\..\Run: [igfxhkcmd] C:\WINDOWS\system32\hkcmd.exe
O4 - HKLM\..\Run: [igfxpers] C:\WINDOWS\system32\igfxpers.exe
O4 - HKLM\..\Run: [IntelZeroConfig] C:\Program Files\Intel\Wireless\bin\ZCfgSvc.exe
O4 - HKLM\..\Run: [IntelliPoint] "c:\Program Files\Microsoft IntelliPoint\ipoint.exe"
O4 - HKLM\..\Run: [NeroFilterCheck] C:\Program Files\Common Files\Nero\Lib\NeroCheck.exe
O4 - HKLM\..\Run: [DrvIcon] C:\Program Files\Vista Drive Icon\DrvIcon.exe
O4 - HKLM\..\Run: [QuickTime Task] "C:\Program Files\QuickTime\qttask.exe" -atboottime
O4 - HKCU\..\Run: [CTFMON.EXE] C:\WINDOWS\system32\ctfmon.exe
O4 - HKCU\..\Run: [LClock] C:\Program Files\LClock\LClock.exe
O4 - HKCU\..\Run: [swg] "C:\Program Files\Google\GoogleToolbarNotifier\GoogleToolbarNotifier.exe"
O4 - HKUS\S-1-5-19\..\Run: [CTFMON.EXE] C:\WINDOWS\system32\CTFMON.EXE (User 'LOCAL SERVICE')
O4 - HKUS\S-1-5-20\..\Run: [CTFMON.EXE] C:\WINDOWS\system32\CTFMON.EXE (User 'NETWORK SERVICE')
O4 - HKUS\S-1-5-18\..\Run: [CTFMON.EXE] C:\WINDOWS\system32\CTFMON.EXE (User 'SYSTEM')
O4 - HKUS\S-1-5-18\..\RunOnce: [RunNarrator] Narrator.exe (User 'SYSTEM')
O4 - HKUS\.DEFAULT\..\Run: [CTFMON.EXE] C:\WINDOWS\system32\CTFMON.EXE (User 'Default user')
O4 - HKUS\.DEFAULT\..\RunOnce: [RunNarrator] Narrator.exe (User 'Default user')
O4 - Startup: OpenOffice.org 3.1.lnk = C:\Program Files\OpenOffice.org 3\program\quickstart.exe
O4 - Global Startup: Microsoft Office.lnk = C:\Program Files\Microsoft Office\Office\OSA9.EXE
O8 - Extra context menu item: Google Sidewiki... - res://C:\Program Files\Google\Google Toolbar\Component\GoogleToolbarDynamic_mui_en_96D6FF0C6D236BF8.dll/cmsidewiki.html
O9 - Extra button: ShopperReports - Compare product prices - {C5428486-50A0-4a02-9D20-520B59A9F9B2} - C:\Program Files\ShoppingReport\Bin\2.6.58\ShoppingReport.dll
O9 - Extra button: ShopperReports - Compare travel rates - {C5428486-50A0-4a02-9D20-520B59A9F9B3} - C:\Program Files\ShoppingReport\Bin\2.6.58\ShoppingReport.dll
O9 - Extra button: Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Program Files\Messenger\msmsgs.exe
O9 - Extra 'Tools' menuitem: Windows Messenger - {FB5F1910-F110-11d2-BB9E-00C04F795683} - C:\Program Files\Messenger\msmsgs.exe
O16 - DPF: {4CCA4E80-9259-11D9-AC6E-444553544200} (FixController Control) - http://h30155.www3.h...llMgr_v01_5.cab
O16 - DPF: {AB86CE53-AC9F-449F-9399-D8ABCA09EC09} (Get_ActiveX Control) - https://h17000.www1....loadManager.ocx
O17 - HKLM\System\CCS\Services\Tcpip\..\{B71984A0-F691-41FF-A581-0A45CD0CF3AA}: NameServer = 202.136.43.240 202.136.43.241
O18 - Protocol: linkscanner - {F274614C-63F8-47D5-A4D1-FBDDE494F8D1} - C:\Program Files\AVG\AVG8\avgpp.dll
O20 - Winlogon Notify: avgrsstarter - avgrsstx.dll (file missing)
O22 - SharedTaskScheduler: Browseui preloader - {438755C2-A8BA-11D1-B96B-00A0C90312E1} - C:\WINDOWS\system32\browseui.dll
O22 - SharedTaskScheduler: Component Categories cache daemon - {8C7461EF-2B13-11d2-BE35-3078302C2030} - C:\WINDOWS\system32\browseui.dll
O23 - Service: AVG8 WatchDog (avg8wd) - AVG Technologies CZ, s.r.o. - C:\PROGRA~1\AVG\AVG8\avgwdsvc.exe
O23 - Service: Email2DB Server (Email2DB) - Parker Software - C:\Documents and Settings\Owner\Desktop\online marketing\Email2DB2\Email2DBServer.exe
O23 - Service: Email2DB IMAP Server (Email2DBIMAP) - Parker Software - C:\Documents and Settings\Owner\Desktop\online marketing\Email2DB2\Email2DBIMAPServer.exe
O23 - Service: Email2DB POP3 Server (Email2DBPOP3) - Parker Software - C:\Documents and Settings\Owner\Desktop\online marketing\Email2DB2\Email2DBPOP3Server.exe
O23 - Service: Email2DB Mail Server (Email2DBSMTP) - Parker Software - C:\Documents and Settings\Owner\Desktop\online marketing\Email2DB2\Email2DBMailServer.exe
O23 - Service: EvtEng - Intel Corporation - C:\Program Files\Intel\Wireless\Bin\EvtEng.exe
O23 - Service: Google Update Service (gupdate) (gupdate) - Google Inc. - C:\Program Files\Google\Update\GoogleUpdate.exe
O23 - Service: Google Software Updater (gusvc) - Google - C:\Program Files\Google\Common\Google Updater\GoogleUpdaterService.exe
O23 - Service: InstallDriver Table Manager (IDriverT) - Macrovision Corporation - C:\Program Files\Common Files\InstallShield\Driver\11\Intel 32\IDriverT.exe
O23 - Service: iPod Service - Apple Inc. - C:\Program Files\iPod\bin\iPodService.exe
O23 - Service: LightScribeService Direct Disc Labeling Service (LightScribeService) - Hewlett-Packard Company - C:\Program Files\Common Files\LightScribe\LSSrvc.exe
O23 - Service: Nero BackItUp Scheduler 3 - Nero AG - C:\Program Files\Nero\Nero8\Nero BackItUp\NBService.exe
O23 - Service: NICCONFIGSVC - Dell Inc. - C:\Program Files\Dell\NICCONFIGSVC\NICCONFIGSVC.exe
O23 - Service: NMIndexingService - Nero AG - C:\Program Files\Common Files\Nero\Lib\NMIndexingService.exe
O23 - Service: RegSrvc - Intel Corporation - C:\Program Files\Intel\Wireless\Bin\RegSrvc.exe
O23 - Service: Spectrum24 Event Monitor (S24EventMonitor) - Intel Corporation - C:\Program Files\Intel\Wireless\Bin\S24EvMon.exe
O23 - Service: ServiceLayer - Nokia. - C:\Program Files\PC Connectivity Solution\ServiceLayer.exe
O23 - Service: WLANKEEPER - Intel® Corporation - C:\Program Files\Intel\Wireless\Bin\WLKeeper.exe
--
End of file - 9933 bytes



 This topic is locked
This topic is locked